好的,我现在需要帮用户总结一篇文章的内容,控制在100字以内。用户已经提供了文章的详细内容,所以我得先仔细阅读并理解文章的主要观点。 首先,文章主要讨论了2025年勒索软件的变化。过去,安全团队主要关注技术层面的问题,比如加密文件和数据恢复。但现在勒索软件已经演变成系统化的敲诈活动,利用被盗数据、法律责任和心理压力来施压。 文章提到勒索软件的结构发生了变化,变得分散和协作,使得归因和破坏变得更加困难。攻击者不再只依赖加密技术,而是转向双重勒索模式,威胁公开披露数据、法律诉讼和声誉损害。 此外,攻击者开始针对中小企业和高监管区域,利用这些地区的严格法规来增加受害者支付赎金的压力。心理战术也被广泛使用,比如制造紧迫感、威胁曝光数据以及利用内部压力。 最后,文章给出了安全团队的应对策略,包括法律准备、员工培训、漏洞管理和配置审计等。 总结下来,文章的核心是勒索软件在2025年的演变及其带来的新挑战。我需要将这些要点浓缩到100字以内,并且直接描述内容,不需要开头语。 现在开始组织语言:勒索软件在2025年从技术问题演变为系统化敲诈活动。攻击者利用被盗数据、法律风险和心理压力进行双重勒索。他们针对中小企业和高监管区域,并通过心理战术施压。安全团队需调整策略以应对这些变化。 检查字数:确保不超过100字,并且涵盖主要变化和应对措施。 </think> 勒索软件在2025年从单纯的技术问题演变为系统化的敲诈活动,攻击者通过窃取数据、制造法律风险和施加心理压力进行双重勒索,并针对中小企业和高监管区域展开精准攻击,安全团队需调整策略以应对这一新威胁。 2026-1-27 15:15:15 Author: www.bleepingcomputer.com(查看原文) 阅读量:0 收藏

For years, security teams treated ransomware as a technological problem. Security teams hardened backup systems, deployed endpoint detection, practiced incident response playbooks built around data recovery, and employed attack surface management to prevent initial access.
But in 2025, that playbook is dangerously outdated. Today's ransomware operations have evolved beyond file encryption into something far more difficult to defend against, systematized extortion campaigns that weaponize stolen data, legal liability, and psychological pressure at industrial scale.
The known solution—restore from backup—no longer addresses the threat. Now, organizations need to respond to data exposure, legal liability, and reputation damage.
How Ransomware Reorganized in 2025
Ransomware in 2025 didn't simply grow—it fundamentally reorganized. After major takedowns in 2024 (LockBit, BlackSuit, and 8Base), no single group started dominating the ecosystem again. Instead, ransomware became fragmented and collaborative, with affiliates moving fluidly between brands, reusing tooling, and sharing access brokers.
This decentralization made attribution and disruption far harder, while the impact on victims remained severe.
From Single Playbook to Extortion Spectrum
Recent campaigns reveal that double extortion has evolved beyond a single playbook. Threat actors now deploy a spectrum of tactics optimized for scale, leverage, and resilience. Threat actors demonstrated that identity abuse and social engineering alone can drive large-scale extortion.
This pressure is being amplified through public shaming and recycled data. This marked a shift toward pressure-first operations where reputation damage and exposure threats outweigh technical disruption.
At the same time, groups such as Qilin, Akira, SafePay, INC, and Lynx formalized the classic double-extortion model: steal data, encrypt systems, then threaten public disclosure. Their negotiations increasingly invoked legal liability, regulatory fines, and civil lawsuits, reframing ransom demands as a form of “risk mitigation” rather than mere recovery.
Cl0p refined encryption-less extortion at industrial scale by exploiting supply-chain software to exfiltrate data from hundreds of victims simultaneously.
Meanwhile, DragonForce and RansomHub highlighted the durability of cartel-style operations, where affiliate reuse and shared infrastructure sustain double extortion even as brands vanish, splinter, or rebrand.
Why Threat Actors Now Target SMBs in High-Regulation Regions
Flare researchers recently analyzed how SafePay ransomware emerged rapidly in late 2024 and scaled aggressively through 2025 using a textbook double-extortion approach combining data theft, encryption, and Tor-based leak sites.
By analyzing 500 SafePay leak records, researchers found that over 90% of victims were small and mid-sized businesses (SMBs) large enough to pay ransoms but with insufficient resilience to withstand prolonged downtime or public data exposure.
Victims were predominantly service-based companies (approximately 66%), indicating deliberate economic targeting rather than opportunistic scanning.
Geographically, incidents clustered in high-regulation, high-GDP regions (particularly the United States and Germany), where frameworks such as GDPR, NIS2, HIPAA, and breach-notification laws dramatically amplify the cost of data leaks. In these environments, public exposure often triggers regulatory, legal, and reputational consequences that outweigh the ransom itself.
This analysis reveals how SafePay’s victim profile exposes broader risk dynamics that rarely appear in official incident disclosures. Because many victims never report ransomware attacks publicly, leak-site intelligence provides a “shadow transparency layer,” revealing sector concentration, geographic exposure, and organizational vulnerability.
For security teams and risk managers, these insights are directly actionable, informing third-party risk assessments, cyber-insurance underwriting, M&A due diligence, and proactive defensive investment.
Inside the Psychological Playbook: How Ransom Notes Weaponize Fear
The shift toward pressure-centric extortion extends far beyond sophisticated operations. Separate Flare research on MongoDB ransom operations (active since 2017) illustrates how even long-standing, low-tech campaigns have adapted to the same pressure-centric model. What was once a simple “encrypt to get paid” scheme now prioritizes stolen data, reputational harm, and legal exposure over technical sophistication.
In the MongoDB ecosystem, attackers do not rely on advanced malware or zero-day vulnerabilities. Instead, they exploit predictable misconfigurations: internet-exposed MongoDB or Mongo Express instances with no authentication.
Automated bots scan for open databases, connect, dump or delete collections, and leave ransom notes demanding relatively small Bitcoin payments (historically ~$500–$600), often without any evidence that recovery is possible.
This mirrors the broader evolution of ransomware economics: optimize for scale, speed, and psychological pressure—not technical novelty.
Where early ransomware notes were simple— “pay or lose your data”— modern extortion has become a fully scripted coercion process, complete with negotiation guidance, legal framing, and psychological manipulation.
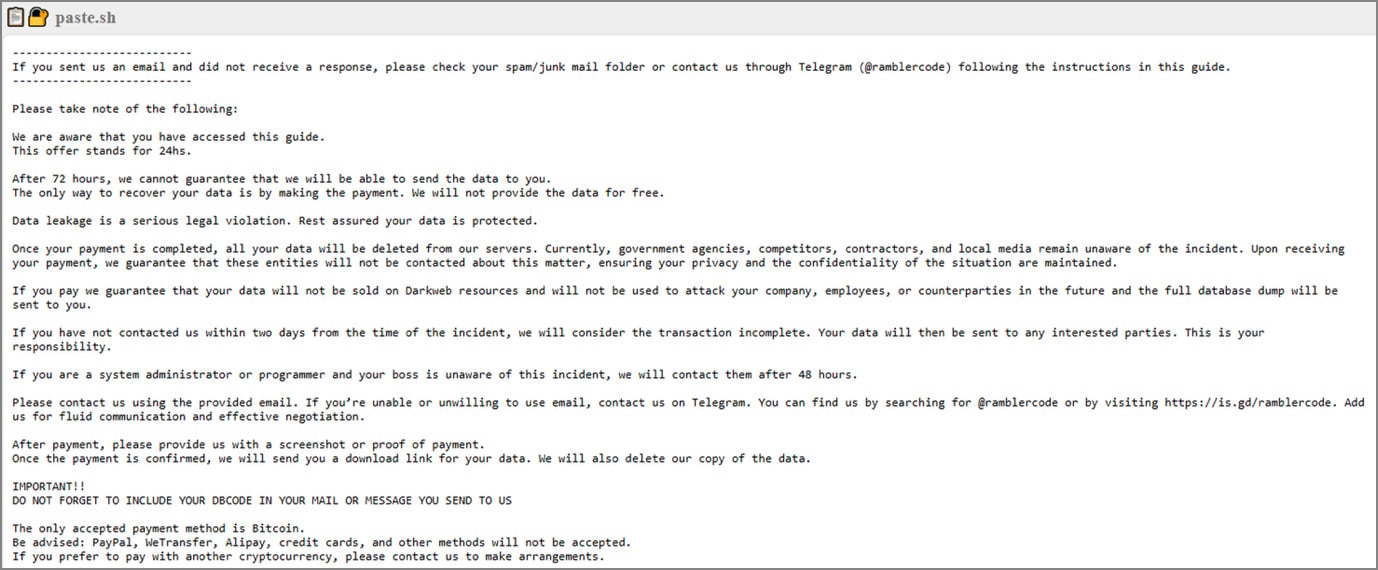
Psychological Pressure Points
Below are the key themes ransomware groups employ to manipulate their victims:
1. Surveillance & Awareness
“We are aware that you have accessed this guide.”
This creates perceived omniscience. The attacker signals monitoring capability, inducing paranoia and urgency (“they’re watching us”), even if it’s likely untrue.
2. Artificial Time Pressure
“This offer stands for 24hs.”
“If you have not contacted us within two days…”
Short, escalating deadlines are used to override rational decision-making, forcing impulsive action before legal, executive, or forensic consultation.
3. Loss of Control Framing
“The only way to recover your data is by making the payment.”
This removes perceived alternatives (backups, law enforcement, and incident response), framing payment as the sole viable path.
4. Legal & Regulatory Fear
“Data leakage is a serious legal violation.”
This explicitly triggers compliance anxiety (GDPR, breach notification laws, and lawsuits), reframing ransom as a cheaper alternative to regulatory fallout.
5. Reputation & Exposure Threats
“Government agencies, competitors, contractors, and local media remain unaware…”
The attacker names specific audiences to maximize fear: regulators, competitors, and media. This is reputational blackmail layered on top of data loss.
6. Internal Hierarchy Pressure
“If you are a system administrator… we will contact [your boss].”
This weaponizes organizational politics, isolating technical staff and pushing them to act secretly to avoid blame or job loss.
7. False Reassurance & Trust Engineering
“We guarantee your data will not be sold… will be deleted from our servers.”
This mimics contractual language to create illusory trust, despite no enforcement mechanism or proof of good faith.
8. Responsibility Shifting
“This is your responsibility.”
Explicitly assigns blame to the victim for future harm, increasing guilt and perceived moral obligation to pay.
9. Friction Reduction
Detailed Bitcoin purchasing instructions eliminate logistical excuses and reduce hesitation—removing barriers to compliance.
Double-Extortion Components
This note clearly demonstrates double extortion, even without encryption:
1. Primary Extortion: Data Availability
-
Threat of permanent data loss
-
Claim that data recovery is impossible without payment
2. Secondary Extortion: Data Disclosure
-
Threats to:
-
Sell data on dark web
-
Leak to “interested parties”
-
Contact media, regulators, and competitors
-
Target employees and counterparties
-
This converts a technical incident into a legal, reputational, and business-continuity crisis.
What Security Teams Can Do
Defending against exposure-focused ransomware requires four strategic shifts:
1. Prepare legal and communications teams early.
When the primary weapon is reputational damage and regulatory exposure, technical remediation alone won't suffice. Incident response plans should include pre-drafted breach notification templates, regulatory disclosure procedures, and media response frameworks—not as afterthoughts, but as first-line defenses.
2. Continuously train your organization to be more cybersecure.
This includes building organizational resilience against the psychological tactics ransomware groups deploy—particularly the guilt and blame narratives designed to isolate technical staff and delay escalation. Create an environment where security teams can surface incidents early without fear of personal repercussions.
3. Augment your vulnerability management program with intelligence on actively exploited vulnerabilities.
When facing thousands of CVEs and millions of security alerts, security teams need a prioritization framework grounded in real-world threat activity. By leveraging threat intelligence that identifies which specific vulnerabilities ransomware groups are exploiting in current campaigns—for example, “Group X is actively exploiting CVE-2024-1234 and CVE-2025-5678”—teams can focus remediation efforts on the attack vectors ransomware operators are actually using to gain initial access, rather than attempting to address everything at once.
4. Prioritize configuration audits based on attack vectors actively exploited by ransomware groups.
The MongoDB example illustrates a critical principle: threat actors don't exploit infinite misconfiguration permutations—they systematically target predictable, high-yield patterns like internet-exposed databases without authentication. Rather than attempting to audit every possible configuration risk, security teams should use threat intelligence to identify which specific misconfigurations ransomware operators are exploiting at scale in current campaigns, then conduct targeted audits of internet-facing assets for those high-risk patterns. This approach transforms configuration management from an overwhelming checklist into a focused defensive strategy.
What to Know About Modern Ransomware
Modern ransomware is no longer defined by encryption—it's defined by the leverage threat actors have over organizations. Since 2017, and accelerating sharply after 2024, threat actors have shifted toward double extortion models that weaponize stolen data, regulatory exposure, and psychological pressure.
From industrial-scale operations like SafePay to low-tech MongoDB campaigns, the pattern is consistent: attackers optimize for speed, scale, and psychological coercion over technical complexity.
For security teams, this means defense strategies must evolve beyond traditional recovery-focused playbooks. Visibility into external exposure, disciplined configuration management, and monitoring for leaked credentials are no longer optional—they're foundational.
Today's ransomware problem is fundamentally about human and legal pressure, not just malware. Recognizing this distinction is what separates reactive crisis management from proactive risk mitigation.
Learn more by signing up for our free trial.
Sponsored and written by Flare.
如有侵权请联系:admin#unsafe.sh