好的,我现在需要帮用户总结这篇文章的内容,控制在100字以内。首先,我得通读整篇文章,抓住主要信息。 文章讲的是一个恶意活动,名为“Bizarre Bazaar”,目标是利用暴露的大型语言模型(LLM)服务端点进行非法商业化。研究人员记录了超过35,000次攻击,涉及窃取计算资源用于加密货币挖掘、转售API访问权限、窃取数据以及尝试入侵内部系统。攻击者利用配置错误的端点,如未认证的Ollama和OpenAI兼容API。整个活动涉及三个威胁参与者,通过Telegram和Discord推广服务。 接下来,我需要将这些要点浓缩到100字以内。要确保涵盖攻击名称、目标、主要行动和影响。同时,避免使用“文章内容总结”之类的开头词。 可能的结构:恶意活动名称+目标+主要行动+影响+攻击者手段+涉及的参与者。 现在组织语言: 恶意活动“Bizarre Bazaar”针对暴露的大型语言模型服务端点进行非法商业化。攻击者窃取计算资源用于加密货币挖掘、转售API访问权限、窃取数据,并尝试入侵内部系统。他们利用配置错误的端点,如未认证的Ollama和OpenAI兼容API。整个活动涉及三个威胁参与者,并通过Telegram和Discord推广服务。 检查字数是否在100字以内,并调整用词使其更简洁。 </think> 恶意活动“Bizarre Bazaar”针对暴露或配置不当的人工智能基础设施进行攻击,窃取计算资源用于加密货币挖矿、转售API访问权限并窃取数据。攻击者利用未认证的LLM端点,在短时间内迅速展开行动,并通过Telegram和Discord推广相关服务。 2026-1-28 13:15:29 Author: www.bleepingcomputer.com(查看原文) 阅读量:0 收藏

A malicious campaign is actively targeting exposed LLM (Large Language Model) service endpoints to commercialize unauthorized access to AI infrastructure.
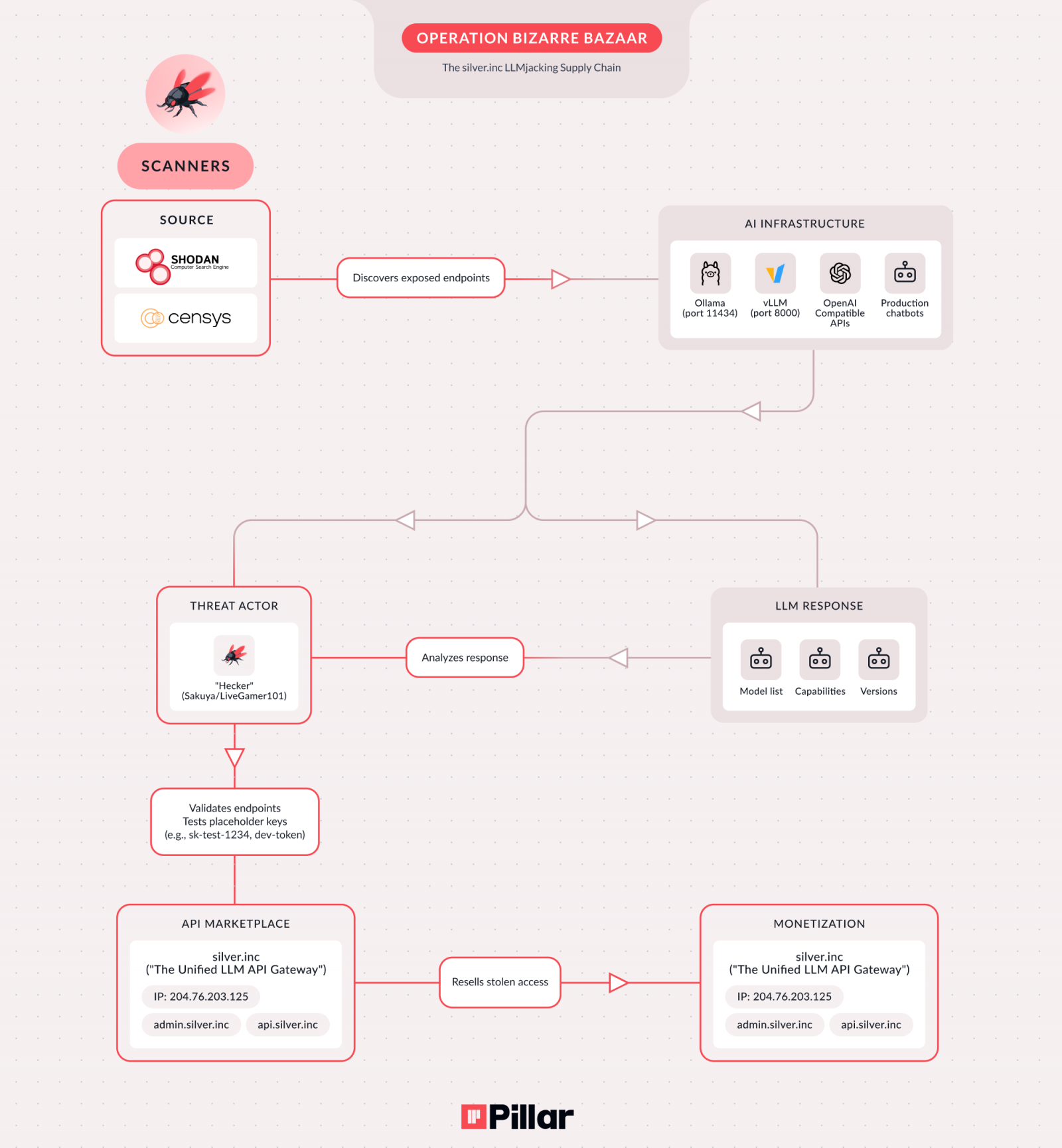
Over a period of 40 days, researchers at Pillar Security recorded more than 35,000 attack sessions on their honeypots, which led to discovering a large-scale cybercrime operation that monetizes and exploits access to exposed or poorly authenticated AI endpoints.
They call the campaign 'Bizarre Bazaar' and highlight that it is one of the first examples of ‘LLMjacking’ attacks attributed to a specific threat actor.
In a report shared with BleepingComputer, Bizarre Bazaar involves unauthorized access to weakly protected LLM infrastructure endpoints to:
- Steal computing resources for cryptocurrency mining
- Resell API access on darknet markets
- Exfiltrate data from prompts and conversation history,
- Attempt to pivot into internal systems via Model Context Protocol (MCP) servers
Common attack vectors include self-hosted LLM setups, exposed or unauthenticated AI APIs, publicly accessible MCP servers, and development or staging AI environments with public IP addresses.
Typically, attackers exploit misconfigurations such as unauthenticated Ollama endpoints on port 11434, OpenAI-compatible APIs on port 8000, and unauthenticated production chatbots.
The researchers note that the attacks begin within hours of a misconfigured endpoint appearing in Shodan or Censys internet scans.
"The threat differs from traditional API abuse because compromised LLM endpoints can generate significant costs (inference is expensive), expose sensitive organizational data, and provide lateral movement opportunities," Pillar Security says.
At the beginning of the month, a report from GreyNoise highlighted similar activity, where attackers targeted commercial LLM services, mainly for enumeration.
Pillar Security’s findings indicate a criminal supply chain involving three threat actors who likely work together as part of the same operation.
The first one uses bots to systematically scan the internet for LLM and MCP endpoints. The second validates the findings and tests access. The third operates a commercial service at ‘silver[.]inc’ marketed on Telegram and Discord, that resells access in exchange for cryptocurrency or PayPal payments.
SilverInc promotes a project called NeXeonAI, which is advertised as a "unified AI infrastructure" that provides access to more than 50 AI models from leading providers.
source: Pillar Security
The researchers have also attributed the operation to a specific threat actor using the aliases “Hecker,” “Sakuya,” and “LiveGamer101.”
Pillar Security reports that, while Bizarre Bazaar focuses on LLM API abuse, they track a separate campaign that focuses on MCP endpoint reconnaissance.
This targeting gives more opportunities for lateral movement via Kubernetes interactions, cloud service access, and shell command execution, which are often more valuable than resource-consumption-based monetization tactics.
This second campaign has not been linked to Bizarre Bazaar, although a connection may exist.
As of writing, the campaign is ongoing, and the SilverInc service continues to be operational. BleepingComputer has contacted the platform for a comment about Pillar’s findings, but we have not heard back by publication time.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you're cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
如有侵权请联系:admin#unsafe.sh

