
嗯,用户让我总结一下这篇文章的内容,控制在一百个字以内。首先,我需要快速浏览文章,抓住主要信息。 文章讲的是中国间谍组织Mustang Panda更新了他们的CoolClient后门程序。这个新版本可以窃取浏览器的登录数据,还能监控剪贴板。此外,他们还部署了一个新的rootkit,并且利用了Sangfor公司的合法软件作为攻击载体。 用户要求直接写描述,不需要开头语。所以我要把重点放在恶意软件的新功能和攻击目标上。确保内容简洁明了,不超过一百字。 可能的结构是:组织名称、恶意软件名称、新功能、攻击目标和方法。这样既全面又符合字数限制。 最后检查一下是否涵盖了所有关键点:更新后门、窃取数据、监控剪贴板、部署rootkit、利用合法软件攻击政府机构。是的,这样应该可以。 </think> 中国间谍组织Mustang Panda更新其CoolClient后门程序,新增浏览器登录数据窃取和剪贴板监控功能,并通过合法软件分发攻击多国政府机构。 2026-1-27 22:30:18 Author: www.bleepingcomputer.com(查看原文) 阅读量:5 收藏

The Chinese espionage threat group Mustang Panda has updated its CoolClient backdoor to a new variant that can steal login data from browsers and monitor the clipboard.
According to Kaspersky researchers, the malware has also been used to deploy a previously unseen rootkit. However, a technical analysis will be provided in a future report.
CoolClient has been associated with Mustang Panda since 2022, deployed as a secondary backdoor alongside PlugX and LuminousMoth.
The updated malware version has been observed in attacks targeting government entities in Myanmar, Mongolia, Malaysia, Russia, and Pakistan and were deployed via legitimate software from Sangfor, a Chinese company specialized in cybersecurity, cloud computing, and IT infrastructure products.
Previously, CoolClient operators launched the malware via DLL side-loading by abusing signed binaries from Bitdefender, VLC Media Player, and Ulead PhotoImpact.
Kaspersky researchers say that the CoolClient backdoor gathers details about the compromised system and its users, like computer name, version of the operating system, RAM, network information, and the descriptions and versions of loaded driver modules.
CoolClient uses encrypted .DAT files in a multi-stage execution and achieves persistence via Registry modifications, the addition of new Windows services, and scheduled tasks. It also supports UAC bypassing and privilege escalation.
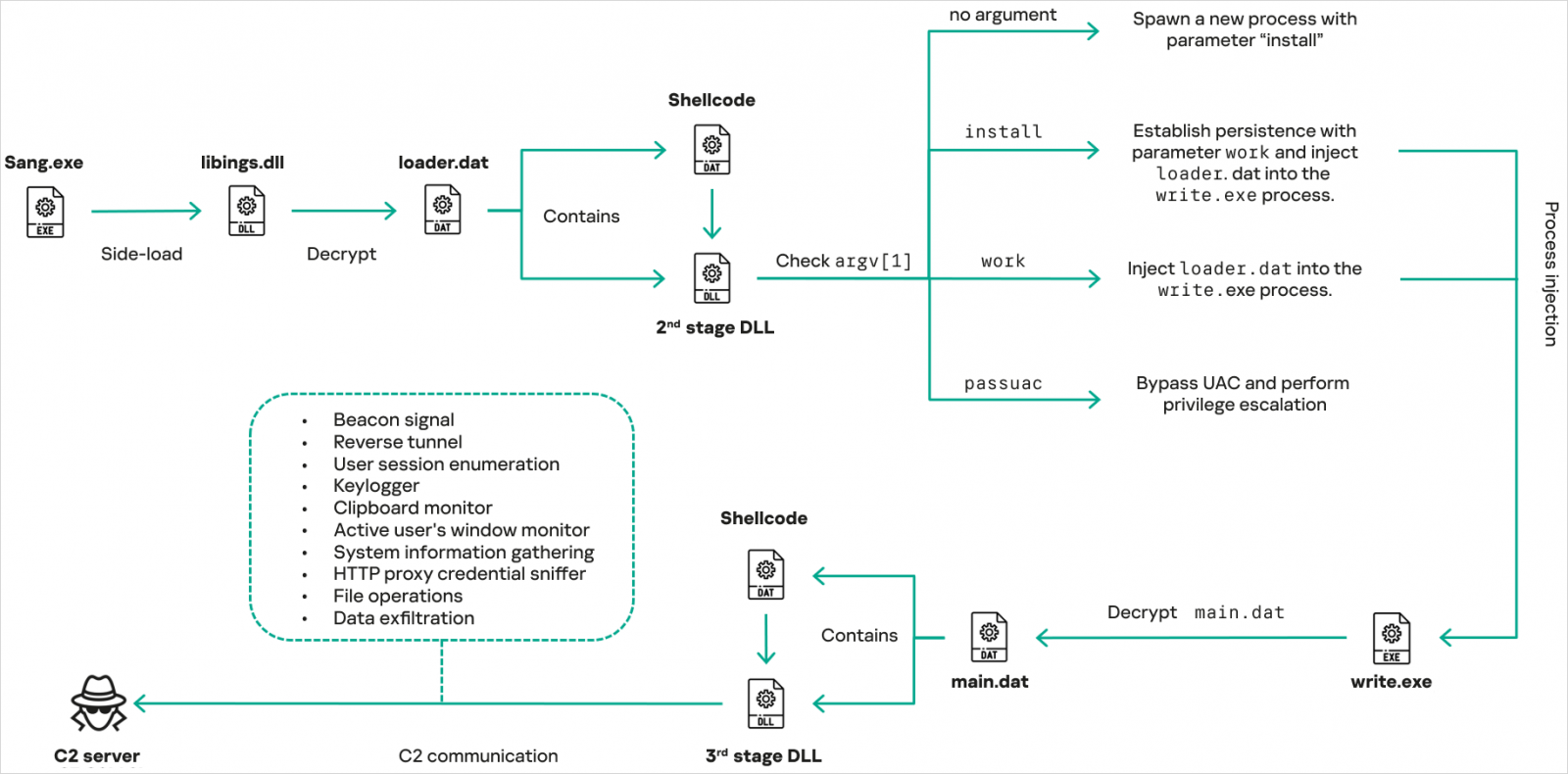
Source: Kaspersky
CoolClient's core features are integrated in a DLL embedded in a file called main.dat. "When launched, it first checks whether the keylogger, clipboard stealer, and HTTP proxy credential sniffer are enabled," the researchers say.
New CoolClient capabilities
The malware’s core functions, including system and user profiling, file operations, keylogging, TCP tunneling, reverse-proxying, and in-memory execution of dynamically fetched plugins, are available in both old and new versions, but are refined in the most recent variants.
What is entirely new in the latest CoolClient is a clipboard monitoring module, the ability to perform active window title tracking, and HTTP proxy credential sniffing that relies on raw packet inspection and headers extraction.
Additionally, the plugin ecosystem has been expanded with a dedicated remote shell plugin, a service management plugin, and a more capable file management plugin.
The service management plugin allows the operators to enumerate, create, start, stop, delete, and modify the startup configuration of Windows services, while the file management plugin provides extended file operations, including drive enumeration, file search, ZIP compression, network drive mapping, and file execution.
Remote shell functionality is implemented via a separate plugin that spawns a hidden cmd.exe process and redirects its standard input and output through pipes, enabling interactive command execution over the command-and-control (C2) channel.
A novelty in CoolClient’s operation is the deployment of infostealers to collect login data from browsers. Kaspersky documented three distinct families targeting Chrome (variant A), Edge (variant B), and a more versatile variant C that targets any Chromium-based browser.
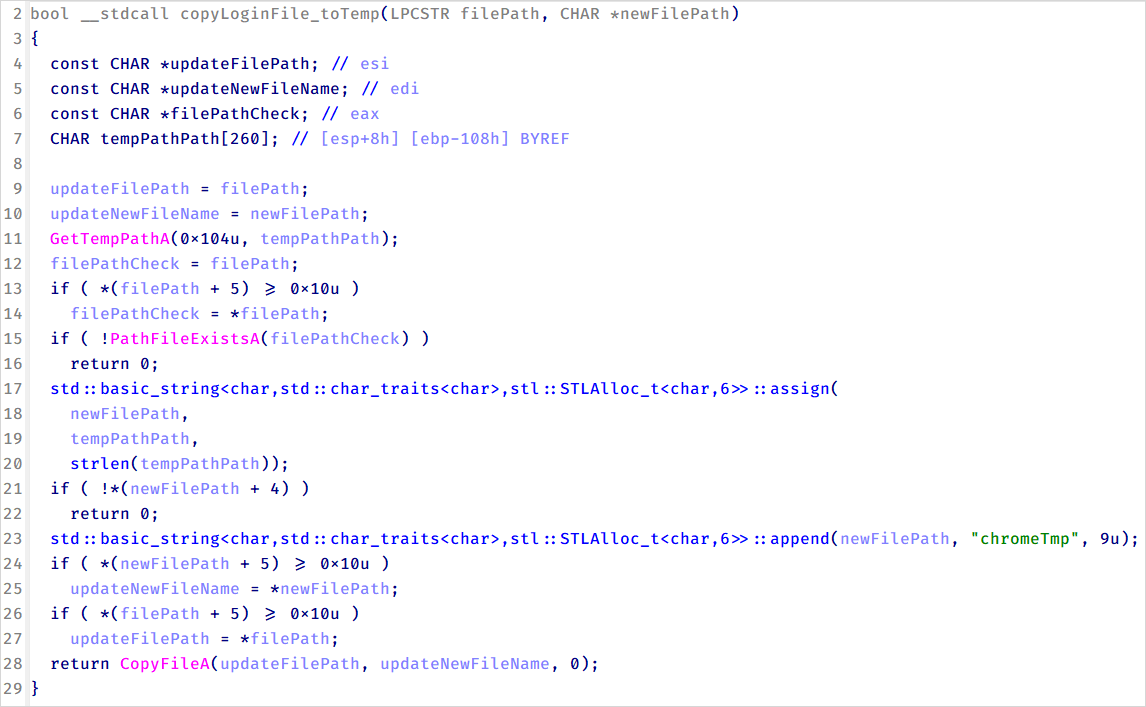
Source: Kaspersky
Another notable operational shift is that browser data theft and document exfiltration now leverage hardcoded API tokens for legitimate public services like Google Drive or Pixeldrain to evade detection.
Mustang Panda continues to evolve its toolset and operational characteristics. Last month, Kaspersky reported about a new kernel-mode loader that deployed a variant of the ToneShell backdoor on government systems.
Earlier this month, Taiwan's National Security Bureau ranked Mustang Panda among the most prolific and high-volume threats targeting its critical infrastructure.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you're cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
如有侵权请联系:admin#unsafe.sh

