好的,我现在需要帮用户总结一篇文章的内容,控制在100字以内。用户给的文章是关于Fortinet发现了一个新的严重漏洞CVE-2026-24858,这个漏洞允许攻击者绕过FortiCloud单点登录(SSO)认证,从而获得对FortiOS、FortiManager和FortiAnalyzer设备的管理访问权限。攻击者利用这个漏洞创建了新的管理员账户,并下载了配置文件。Fortinet已经采取措施缓解了攻击,包括在全球范围内禁用FortiCloud SSO,并正在开发补丁。 首先,我需要确定文章的主要信息点:漏洞名称、影响范围、攻击者的行为、Fortinet的应对措施以及建议用户采取的行动。接下来,我要把这些信息浓缩成简洁的句子,确保不超过100字。 可能会遇到的问题是如何在有限的字数内涵盖所有关键点而不遗漏重要信息。我需要选择最重要的部分,比如漏洞的影响、攻击方式以及缓解措施。同时,要避免使用复杂的术语,保持语言简洁明了。 最后,检查字数是否符合要求,并确保总结准确传达文章的核心内容。 </think> Fortinet发现并修复了 FortiCloud SSO 认证绕过漏洞(CVE-2026-24858),该漏洞允许攻击者通过 FortiCloud SSO 获得对其他客户设备的管理访问权限。尽管设备已修补先前漏洞,攻击者仍能利用此新路径创建管理员账户并下载配置文件。Fortinet 已采取措施阻止此类攻击,并建议用户限制管理访问或禁用 FortiCloud SSO 以降低风险。 2026-1-27 23:30:22 Author: www.bleepingcomputer.com(查看原文) 阅读量:2 收藏

Fortinet has confirmed a new, actively exploited critical FortiCloud single sign-on (SSO) authentication bypass vulnerability, tracked as CVE-2026-24858, and says it has mitigated the zero-day attacks by blocking FortiCloud SSO connections from devices running vulnerable firmware versions.
The flaw allows attackers to abuse FortiCloud SSO to gain administrative access to FortiOS, FortiManager, and FortiAnalyzer devices registered to other customers, even when those devices were fully patched against a previously disclosed vulnerability.
The confirmation comes after Fortinet customers reported compromised FortiGate firewalls on January 21, with attackers creating new local administrator accounts via FortiCloud SSO on devices running the latest available firmware.
The attacks were initially thought to be through a patch bypass for CVE-2025-59718, a previously exploited critical FortiCloud SSO authentication bypass flaw that was patched in December 2025.
Fortinet admins reported that the hackers were logging into FortiGate devices via FortiCloud SSO using the email address [email protected], then creating new local admin accounts.
Logs shared by impacted customers showed similar indicators observed during December exploitation.
On January 22, cybersecurity firm Arctic Wolf confirmed the attacks, saying the attacks appeared automated, with new rogue admin and VPN-enabled accounts created and firewall configurations exfiltrated within seconds. Arctic Wolf said the attack appeared similar to a previous campaign exploiting CVE-2025-59718 in December.
Fortinet confirms alternate attack path
On January 23, Fortinet confirmed that attackers were exploiting an alternate authentication path that remained even on fully patched systems.
Fortinet CISO Carl Windsor said the company had observed cases in which devices running the latest firmware were compromised, indicating that a new attack path was being exploited.
While Fortinet said exploitation had only been seen through FortiCloud SSO, it warned that the issue also applies to other SAML-based SSO implementations.
"It is important to note that while, at this time, only exploitation of FortiCloud SSO has been observed, this issue is applicable to all SAML SSO implementations," explained Fortinet.
At the time, Fortinet advised customers to restrict administrative access to their devices and disable FortiCloud SSO as a mitigation.
The advisory states that Fortinet took actions to mitigate the attacks while patches are being developed.
- On January 22, Fortinet disabled FortiCloud accounts that were being abused by the attackers.
- On January 26, Fortinet disabled FortiCloud SSO globally on the FortiCloud side to prevent further abuse.
- On January 27, FortiCloud SSO access was restored but restricted so that devices running vulnerable firmware can no longer authenticate via SSO.
Fortinet says this server-side change effectively blocks exploitation even if FortiCloud SSO remains enabled on affected devices, so there is nothing that needs to be done client-side until patches are released.
On January 27, Fortinet also published a formal PSIRT advisory assigning CVE-2026-24858 to the flaw, rating it critical with a CVSS score of 9.4.
The vulnerability is "Authentication Bypass Using an Alternate Path or Channel," caused by improper access control in FortiCloud SSO.
According to the advisory, attackers with a FortiCloud account and a registered device could authenticate to other customers' devices if FortiCloud SSO was enabled.
While FortiCloud SSO is not enabled by default, Fortinet says it will automatically turn on when a device is registered with FortiCare, unless it is manually disabled afterward.
Fortinet confirmed the vulnerability was exploited in the wild by the following two malicious FortiCloud SSO accounts, which were locked out on January 22.
[email protected]
[email protected]Fortinet says that once a device was breached, they would download customer config files and create one of the following admin accounts:
audit
backup
itadmin
secadmin
support
backupadmin
deploy
remoteadmin
security
svcadmin
systemConnections were seen made from the following IP addresses:
104.28.244.115
104.28.212.114
104.28.212.115
104.28.195.105
104.28.195.106
104.28.227.106
104.28.227.105
104.28.244.114
Additional IPs observed by a third party, not Fortinet:
37[.]1.209.19
217[.]119.139.50The company says patches are still in development, including for FortiOS, FortiManager, and FortiAnalyzer.
Until then, FortiCloud SSO is blocking logins from vulnerable devices, so administrators do not need to disable the feature to prevent exploitation.
However, Fortinet said this could be abused with other SAML SSO implementations, admins may want to disable the SSO feature for the time being with the following command:
config system global
set admin-forticloud-sso-login disable
endFortinet also said it still investigating whether FortiWeb and FortiSwitch Manager are affected by the flaw.
The company warns that customers who detect the above indicators of compromise in their logs should treat their devices as fully compromised.
Fortinet recommends reviewing all administrator accounts, restoring configurations from known-clean backups, and rotating all credentials.
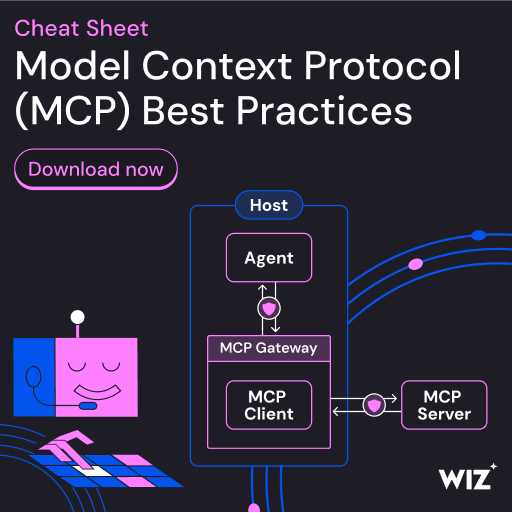
7 Security Best Practices for MCP
As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
如有侵权请联系:admin#unsafe.sh

