嗯,用户让我帮忙总结一下这篇文章的内容,控制在100字以内,而且不需要用“文章内容总结”这样的开头。首先,我需要通读整篇文章,抓住主要信息。 文章讲的是WinRAR的一个高危漏洞CVE-2025-8088被多个威胁行为者利用。这些行为者包括国家支持的和出于财务动机的。漏洞是路径遍历问题,利用ADS写入恶意文件到任意位置。研究人员发现RomCom在零日攻击中使用了这个漏洞。Google Threat Intelligence Group报告说,利用开始于2025年7月18日,并持续到现在。攻击者将恶意文件隐藏在存档中的诱饵文件的ADS里,用户打开后提取恶意负载,导致各种恶意软件传播。 接下来,我需要把这些信息浓缩到100字以内。要涵盖漏洞名称、被利用的情况、漏洞类型、攻击者类型、研究人员发现以及影响范围。 可能的结构是:多个威胁行为者利用WinRAR的CVE-2025-8088漏洞进行初始访问和传播恶意负载。该漏洞是路径遍历问题,利用ADS写入恶意文件。研究人员发现RomCom在零日攻击中使用该漏洞。Google报告称自2025年7月起被广泛利用,导致各种恶意软件传播。 检查一下字数是否符合要求,并确保没有使用禁止的开头。 </think> 多个威胁行为者利用WinRAR的CVE-2025-8088高危漏洞进行初始访问和传播恶意负载。该漏洞为路径遍历问题,可借助Alternate Data Streams (ADS)写入恶意文件至任意位置。研究人员发现俄罗斯相关组织RomCom在零日攻击中使用此漏洞。Google报告称自2025年7月起被广泛利用,导致多种恶意软件传播。 2026-1-27 19:45:16 Author: www.bleepingcomputer.com(查看原文) 阅读量:3 收藏

Multiple threat actors, both state-sponsored and financially motivated, are exploiting the CVE-2025-8088 high-severity vulnerability in WinRAR for initial access and to deliver various malicious payloads.
The security issue is a path traversal flaw that leverages Alternate Data Streams (ADS) to write malicious files to arbitrary locations. Attackers have exploited this in the past to plant malware in the Windows Startup folder, for persistence across reboots.
Researchers at cybersecurity company ESET discovered the vulnerability and reported in early August 2025 that the Russia-aligned group RomCom had been exploiting it in zero-day attacks.
In a report today, the Google Threat Intelligence Group (GTIG) says that exploitation started as early as July 18, 2025, and continues to this day from both state-backed espionage actors and lower-tier, financially motivated cybercriminals.
"The exploit chain often involves concealing the malicious file within the ADS of a decoy file inside the archive.
"While the user typically views a decoy document, such as a PDF, within the archive, there are also malicious ADS entries, some containing a hidden payload while others are dummy data," Google researchers explain.
When opened, WinRAR extracts the ADS payload using directory traversal, often dropping LNK, HTA, BAT, CMD, or script files that execute on user login.
Among the state-sponsored threat actors that Google researchers observed exploiting CVE-2025-8088 are:
- UNC4895 (RomCom/CIGAR) delivering NESTPACKER (Snipbot) via spearphishing to Ukrainian military units.
- APT44 (FROZENBARENTS) using malicious LNK files and Ukrainian-language decoys for follow-on downloads.
- TEMP.Armageddon (CARPATHIAN) dropping HTA downloaders into Startup folders (activity ongoing into 2026).
- Turla (SUMMIT) delivering the STOCKSTAY malware suite using Ukrainian army themes.
- China-linked actors using the exploit to deploy POISONIVY, dropped as a BAT file that downloads additional payloads.
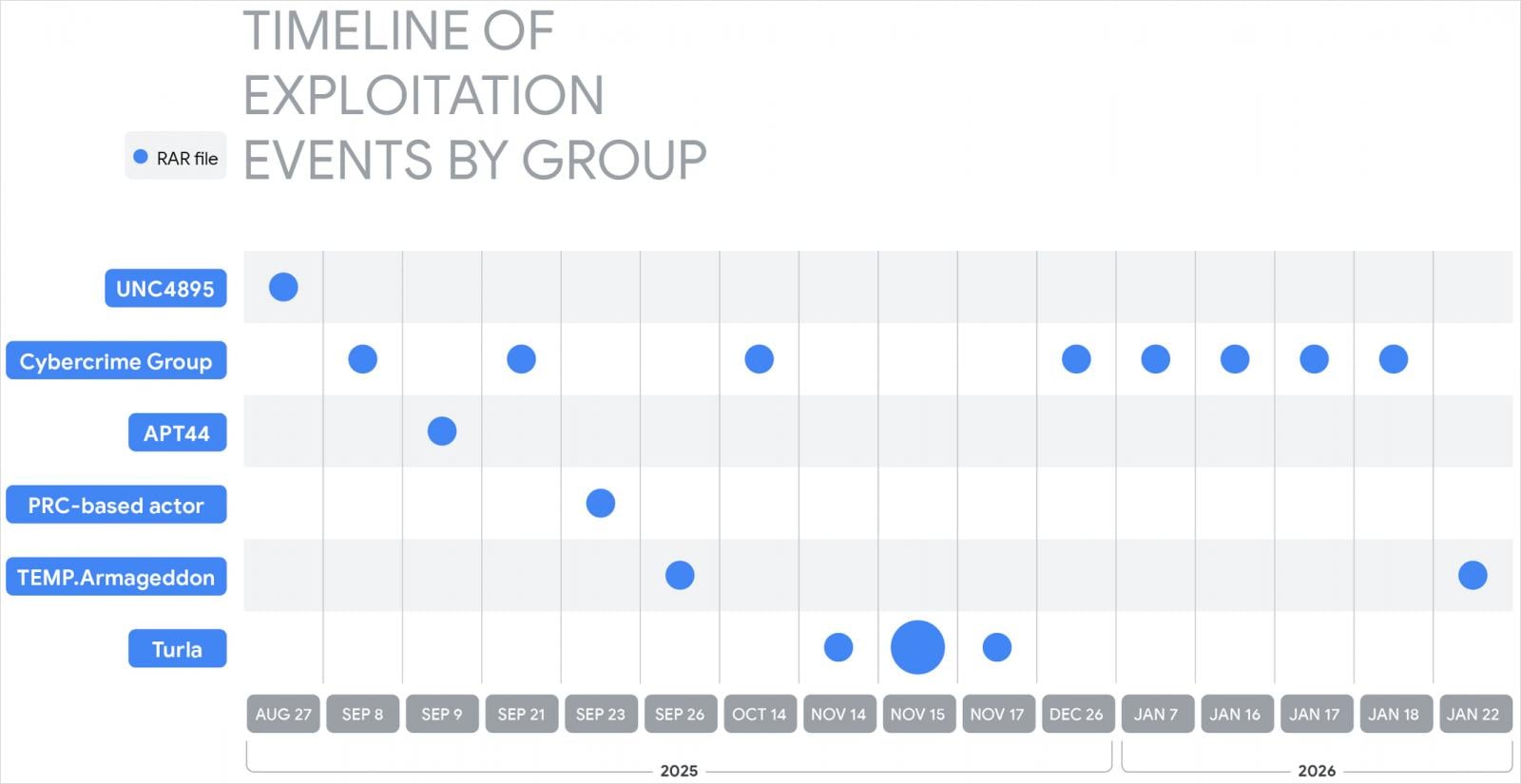
Source: Google
Google also observed financially motivated actors exploiting the WinRAR path-traversal flaw to distribute commodity remote access tools and information stealers such as XWorm and AsyncRAT, Telegram bot-controlled backdoors, and malicious banking extensions for the Chrome browser.
All these threat actors are believed to have sourced working exploits from specialized suppliers, such as one using the alias “zeroplayer,” who advertised a WinRAR exploit last July.
The same threat actor has also marketed multiple high-value exploits last year, including alleged zero-days for Microsoft Office sandbox escape, corporate VPN RCE, Windows local privilege escalation, and bypasses for security solutions (EDR, antivirus), selling them for prices between $80,000 and $300,000.
Google comments that this reflects the commoditization of exploit development, which is crucial in the cyberattacks lifecycle, reducing the friction and complexity for attackers and enabling them to target unpatched systems in a short time.
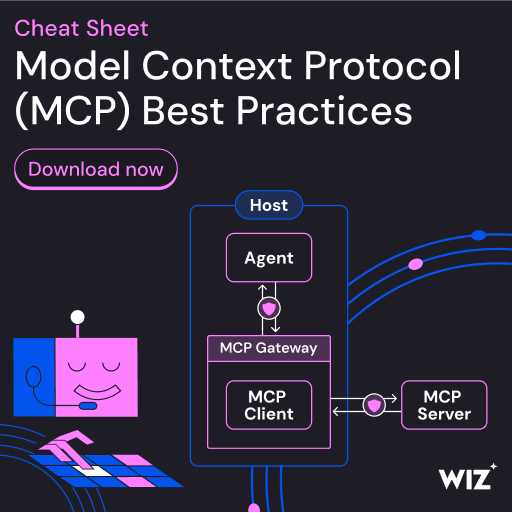
7 Security Best Practices for MCP
As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
如有侵权请联系:admin#unsafe.sh

