A coworker shared this suspicious SMS where AT&T supposedly warns the recipient that their reward points are about to expire.
Phishing attacks are growing increasingly sophisticated, likely with help from AI. They’re getting better at mimicking major brands—not just in look, but in behavior. Recently, we uncovered a well-executed phishing campaign targeting AT&T customers that combines realistic branding, clever social engineering, and layered data theft tactics.
In this post, we’ll walk you through the investigation, screen by screen, explaining how the campaign tricks its victims and where the stolen data ends up.
This is the text message that started the investigation.
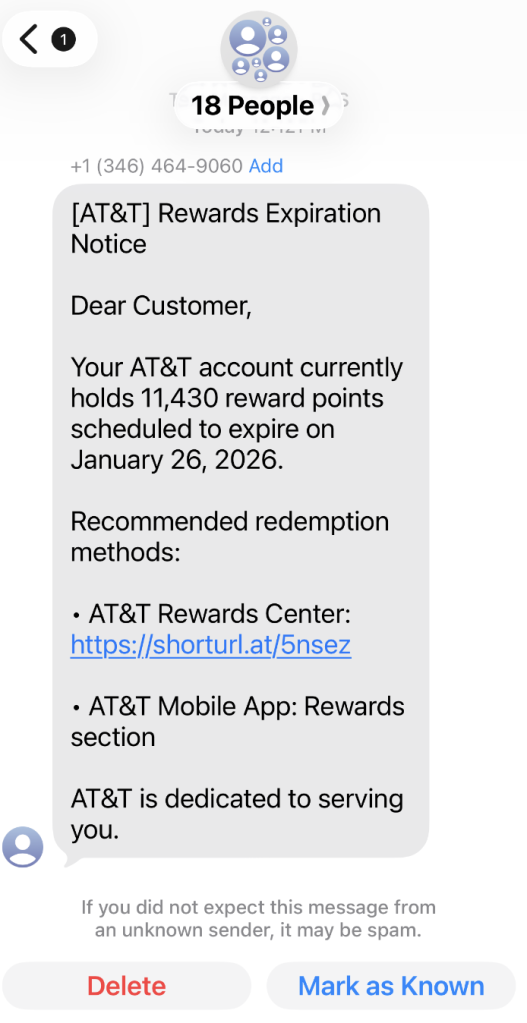
“Dear Customer,
Your AT&T account currently holds 11,430 reward points scheduled to expire on January 26, 2026.
Recommended redemption methods:
– AT&T Rewards Center: {Shortened link}
– AT&T Mobile App: Rewards section
AT&T is dedicated to serving you.”
The shortened URL led to https://att.hgfxp[.]cc/pay/, a website designed to look like an AT&T site in name and appearance.
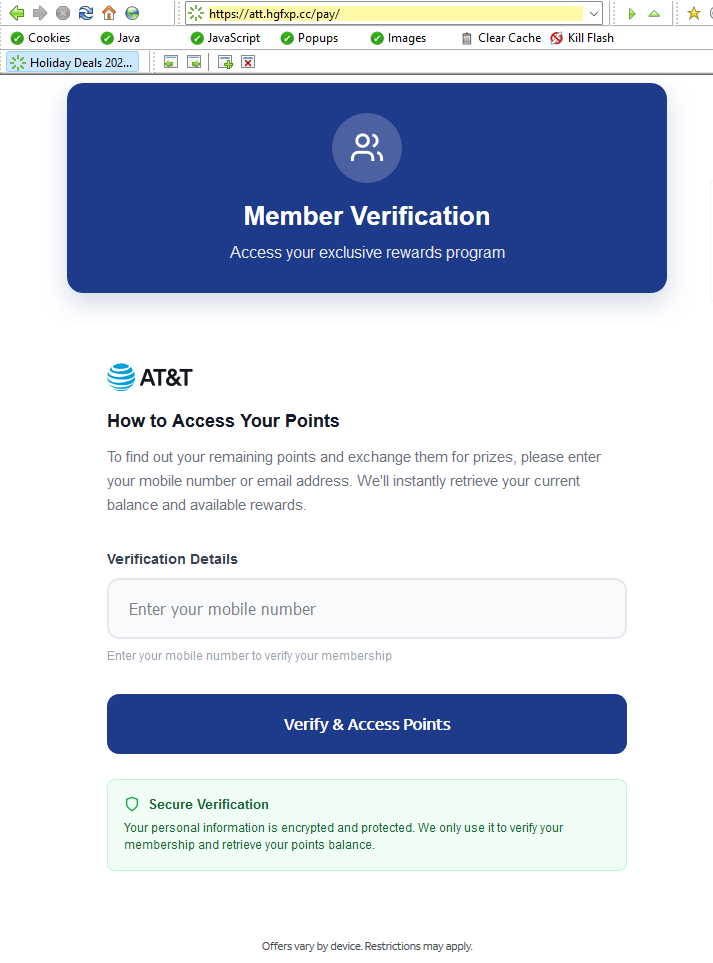
All branding, headers, and menus were copied over, and the page was full of real links out to att.com.
But the “main event” was a special section explaining how to access your AT&T reward points.
After “verifying” their account with a phone number, the victim is shown a dashboard warning that their AT&T points are due to expire in two days. This short window is a common phishing tactic that exploits urgency and FOMO (fear of missing out).
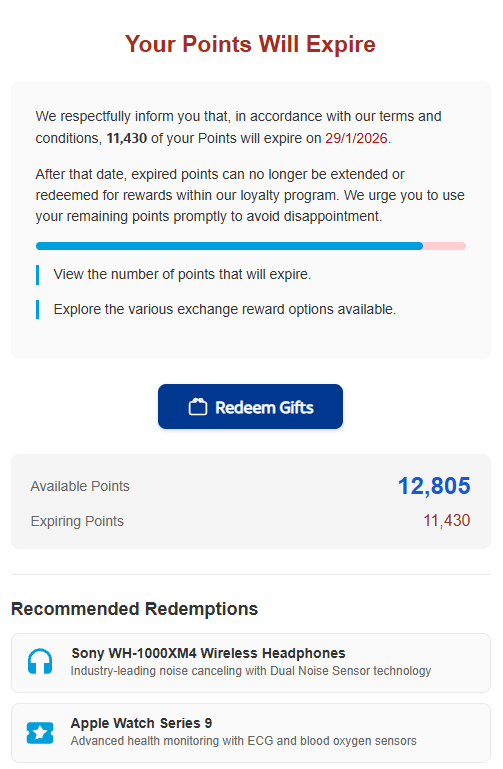
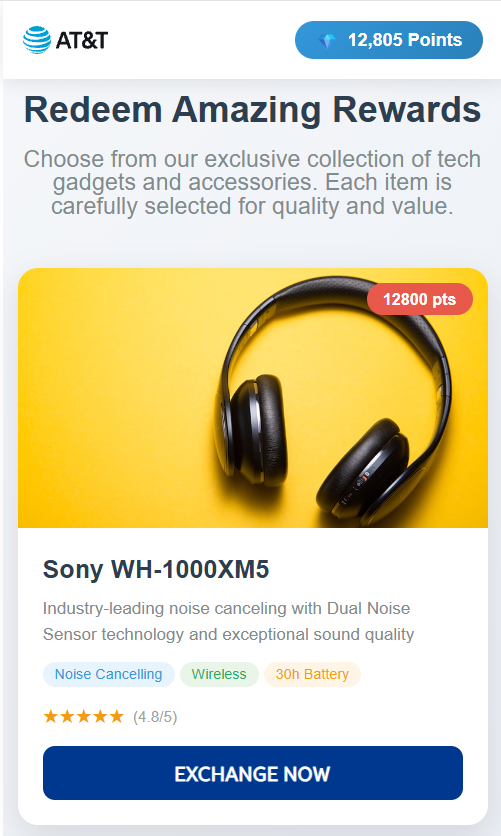
The rewards on offer—such as Amazon gift cards, headphones, smartwatches, and more—are enticing and reinforce the illusion that the victim is dealing with a legitimate loyalty program.
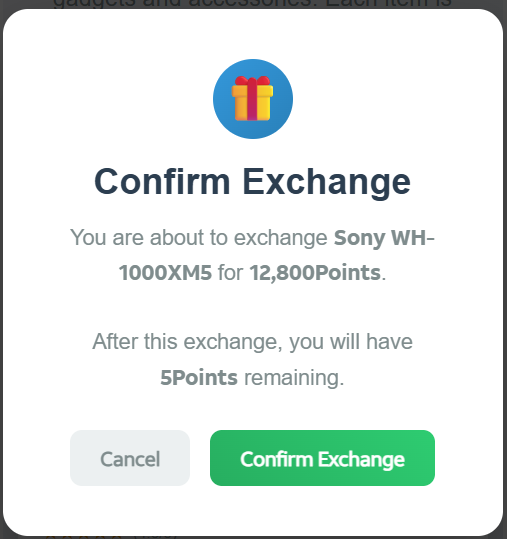
To add even more credibility, after submitting a phone number, the victim gets to see a list of available gifts, followed by a final confirmation prompt.
At that point, the target is prompted to fill out a “Delivery Information” form requesting sensitive personal information, including name, address, phone number, email, and more. This is where the actual data theft takes place.
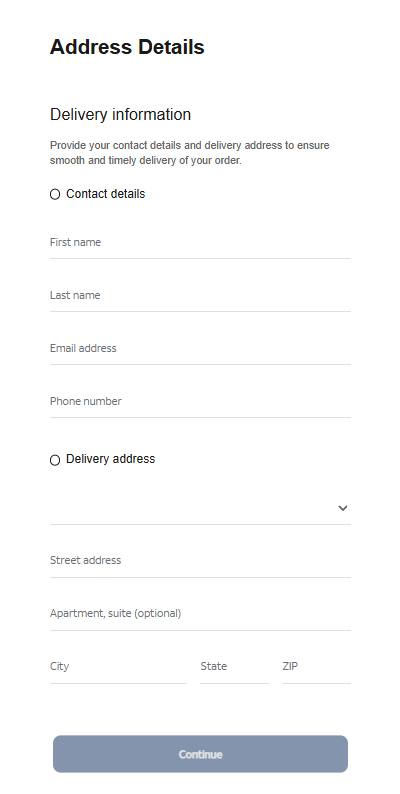
The form’s visible submission flow is smooth and professional, with real-time validation and error highlighting—just like you’d expect from a top brand. This is deliberate. The attackers use advanced front-end validation code to maximize the quality and completeness of the stolen information.
Behind the slick UI, the form is connected to JavaScript code that, when the victim hits “Continue,” collects everything they’ve entered and transmits it directly to the attackers. In our investigation, we deobfuscated their code and found a large “data” section.
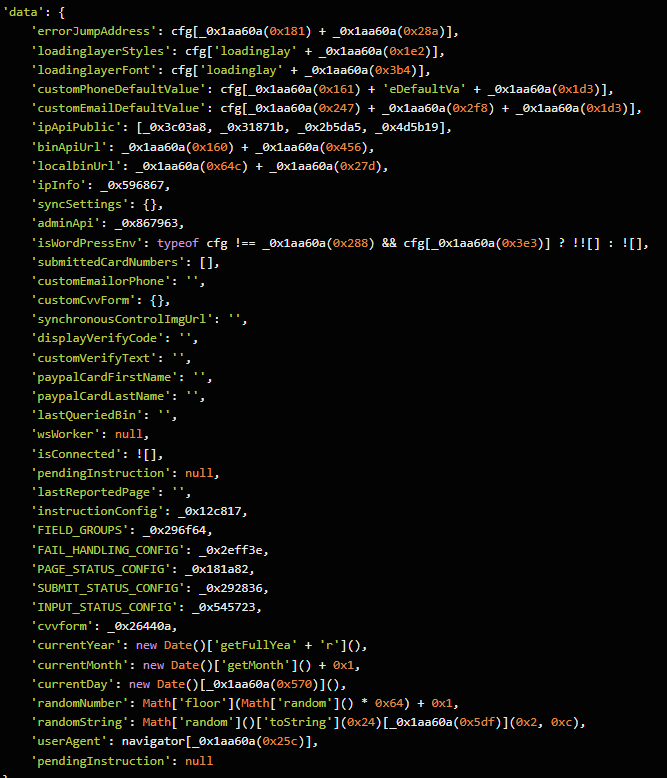
The stolen data gets sent in JSON format via POST to https://att.hgfxp[.]cc/api/open/cvvInterface.
This endpoint is hosted on the attacker’s domain, giving them immediate access to everything the victim submits.
What makes this campaign effective and dangerous
- Sophisticated mimicry: Every page is an accurate clone of att.com, complete with working navigation links and logos.
- Layered social engineering: Victims are lured step by step, each page lowering their guard and increasing trust.
- Quality assurance: Custom JavaScript form validation reduces errors and increases successful data capture.
- Obfuscated code: Malicious scripts are wrapped in obfuscation, slowing analysis and takedown.
- Centralized exfiltration: All harvested data is POSTed directly to the attacker’s command-and-control endpoint.
How to defend yourself
A number of red flags could have alerted the target that this was a phishing attempt:
- The text was sent to 18 recipients at once.
- It used a generic greeting (“Dear Customer”) instead of personal identification.
- The sender’s number was not a recognized AT&T contact.
- The expiration date changed if the victim visited the fake site on a later date.
Beyond avoiding unsolicited links, here are a few ways to stay safe:
- Only access your accounts through official apps or by typing the official website (att.com) directly into your browser.
- Check URLs carefully. Even if a page looks perfect, hover over links and check the address bar for official domains.
- Enable multi-factor authentication for your AT&T and other critical accounts.
- Use an up to date real-time anti-malware solution with a web protection module.
Pro tip: Malwarebytes Scam Guard recognized this text as a scam.
We don’t just report on scams—we help detect them
Cybersecurity risks should never spread beyond a headline. If something looks dodgy to you, check if it’s a scam using Malwarebytes Scam Guard, a feature of our mobile protection products. Submit a screenshot, paste suspicious content, or share a text or phone number, and we’ll tell you if it’s a scam or legit. Download Malwarebytes Mobile Security for iOS or Android and try it today!