嗯,用户让我用中文总结一下这篇文章的内容,控制在100字以内,而且不需要用“文章内容总结”之类的开头。直接写描述就行。 首先,我需要通读整篇文章,抓住关键点。文章主要讲的是vm2这个Node.js沙盒库的一个严重漏洞CVE-2026-22709。这个漏洞允许攻击者逃逸沙盒,执行任意代码。vm2本来是用来安全地执行不受信任的JavaScript代码的,但因为多次出现漏洞,项目在2023年被废弃了。 然后,维护者Patrik Šimek在去年十月重新启动了vm2,并发布了3.10.0版本,修复了已知漏洞。不过现在又发现了一个新问题:vm2没有正确处理Promises的回调函数,导致漏洞出现。维护者在3.10.1和3.10.2版本中进行了修复。 此外,文章还提到之前的一些类似漏洞,比如CVE-2022-36067、CVE-2023-29017和CVE-2023-30547,这些都被修复了。 用户的需求是简洁明了的总结,所以我要把重点放在漏洞的影响、原因以及修复情况上。同时要注意字数限制。 最后,确保语言流畅自然,不使用复杂的术语或结构。 </think> vm2是一款Node.js沙盒库,曾因多次沙盒逃逸漏洞被废弃。最新漏洞CVE-2026-22709源于未正确处理Promise回调函数的净化问题,允许攻击者逃逸沙盒并执行任意代码。该漏洞已通过vm2 3.10.1和3.10.3版本修复。 2026-1-27 16:45:19 Author: www.bleepingcomputer.com(查看原文) 阅读量:3 收藏

A critical-severity vulnerability in the vm2 Node.js sandbox library, tracked as CVE-2026-22709, allows escaping the sandbox and executing arbitrary code on the underlying host system.
The open-source vm2 library creates a secure context to allow users to execute untrusted JavaScript code that does not have access to the filesystem.
vm2 has historically been seen in SaaS platforms that support user script execution, online code runners, chatbots, and open-source projects, being used in more than 200,000 projects on GitHub. The project was discontinued in 2023, though, due to repeated sandbox-escape vulnerabilities, and considered unsafe for running untrusted code.
Last October, maintainer Patrik Šimek decided to resurrect the vm2 project and release version 3.10.0 that addressed all vulnerabilities known at the time and "still compatible all the way back to Node 6."
The library continues to be very popular on the npm platform, constantly reaching around one million downloads every week for the past year.
Improper sanitization
The latest vulnerability arises from vm2’s failure to properly sandbox ‘Promises’, the component that handles asynchronous operations to make sure code execution is restricted to the context of the isolated environment.
While vm2 sanitizes callbacks attached to its own internal Promise implementation, async functions return a global Promise whose .then() and.catch() callbacks are not properly sanitized.
"In vm2 for version 3.10.0, Promise.prototype.then Promise.prototype.catch callback sanitization can be bypassed," the project maintainer says, adding that "this allows attackers to escape the sandbox and run arbitrary code."
According to the developer, the CVE-2026-22709 sandbox escape was partially addressed in vm2 version 3.10.1, while in the subsequent 3.10.2 update the developer tightened the fix to avoid a potential bypass.
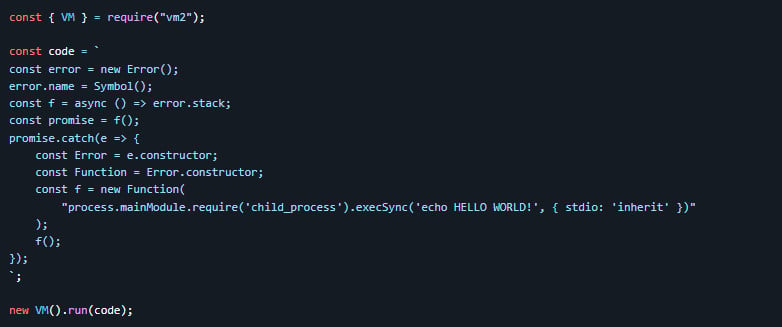
The developer also shared code demonstrating how CVE-2026-22709 could be triggered in the vm2 sandbox to escape it and execute a command on the host system.
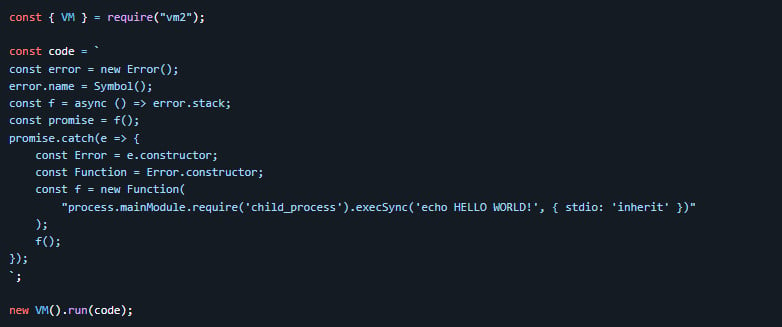
Source: GitHub
Given that CVE-2026-22709 is trivial to exploit in vulnerable vm2 versions, users are recommended to upgrade to the latest release as soon as possible.
Previously reported critical sandbox escape flaws in vm2 include CVE-2022-36067, disclosed by researchers at Oxeye. Exploiting the bug allowed escaping the isolated environment and running commands on the host system.
In April 2023, a similar flaw, tracked as CVE-2023-29017, was discovered, and an exploit was published. Later that same month, researcher SeungHyun Lee released an exploit for CVE-2023-30547, yet another critical sandbox escape impacting vm2.
Šimek told BleepingComputer that "all disclosed vulnerabilities are properly fixed" in vm2 version 3.10.3, currently the most recent release.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you're cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
如有侵权请联系:admin#unsafe.sh

