好的,我现在需要帮用户总结一篇文章的内容,控制在100个字以内。用户已经提供了文章的详细内容,所以我得先仔细阅读并理解文章的主要观点。 文章主要讨论了以.eu.org结尾的电子邮件地址看似可信,但实际上被欺诈者滥用的情况。作者指出,虽然.eu.org看起来像是官方或非营利组织的域名,但许多 disposable email服务利用这个域名来绕过安全检查。文章还提到了检测和阻止这些滥用的方法,比如分析邮件基础设施和行为模式。 接下来,我需要将这些关键点浓缩成一个简短的总结。要注意不要使用“文章内容总结”之类的开头,直接描述内容即可。同时,控制在100字以内,确保信息准确且简洁。 可能的结构是:首先指出.eu.org看似可信却被滥用,然后说明欺诈者如何利用它绕过安全措施,最后提到检测方法的重要性。 现在,把这些点整合成一个流畅的句子: 以.eu.org结尾的电子邮件看似可信,常被误认为官方或非营利组织域名。然而,欺诈者利用其外观可信度绕过安全检查。文章指出识别和阻止这些滥用需关注基础设施和行为模式。 这样大约有75个字左右,符合要求。 </think> 以.eu.org结尾的电子邮件看似可信,常被误认为官方或非营利组织域名,但欺诈者利用其外观可信度绕过安全检查。文章指出识别和阻止这些滥用需关注基础设施和行为模式。 2026-1-27 13:31:45 Author: securityboulevard.com(查看原文) 阅读量:4 收藏

At first glance, an email address ending in .eu.org looks trustworthy. It feels institutional, maybe even official. Many people implicitly associate it with Europe, nonprofits, or established organizations.
That assumption is wrong more often than you might expect.
Because the domain looks legitimate, it has become attractive to fraudsters. Over the past months, we have observed multiple disposable and temporary email services offering addresses under the .eu.org namespace. These services leverage the perceived credibility of the domain to bypass basic email reputation checks and human scrutiny.
To be clear, the problem is not disposable email addresses themselves. Temporary email services are well understood, and we have covered them extensively before. If you want a broader overview of how disposable emails work and why they are frequently abused, you can also refer to this article.
In short, a disposable email address allows anyone to create inboxes instantly, without identity verification, and often without long-term persistence. This makes them convenient for testing, but also appealing for abuse. Fraudsters routinely rely on them to create fake accounts, automate signups, and evade controls that depend on email uniqueness or reputation.
What makes .eu.org interesting is the extra layer of trust it inherits from its appearance. Many systems treat it differently from obviously throwaway domains. Some manual reviewers do too.
In this article, we look at how .eu.org is being used in the wild by disposable email providers, why this matters for fraud and abuse prevention, and how these services can be detected and blocked using concrete technical signals, rather than assumptions based on how an email address looks.
What’s the eu.org domain?
The .eu.org domain is not a standard top-level domain like .com, .org, or .eu. It is a public subdomain service operated by the EU.org organization, available at https://nic.eu.org/. The service allows individuals and organizations to request free subdomains under eu.org.
For example:
example.eu.orgproject-name.eu.organything.eu.org
EU.org presents this as a way to support non-commercial or community projects, particularly for users who cannot afford traditional domain registration. Once a subdomain is granted, it is delegated via DNS, and the requester has full control over how it is used.
From a technical perspective, this means that anyone can operate websites, APIs, or email infrastructure under a .eu.org subdomain, without the commercial onboarding, payment, or verification processes commonly associated with most registrars.
Acceptable use policy and practical limits
EU.org does publish an acceptable use policy. According to their documentation, subdomain owners are required:
“not to spam (issue mass unsolicited email or news postings, including link-spam for SEO) or phish (fake sites to steal authentication data), not to provide tools to help spamming or phishing, not to distribute malware.”
Source: https://nic.eu.org/policy.html
On paper, the policy is unambiguous. Abuse is explicitly forbidden. In practice, however, low-friction domain services face the same challenge: enforcement happens after abuse, not before. Fraudsters do not rely on long-lived domains. They optimize for speed, volume, and disposability. That gap between stated policy and real-world usage is what makes .eu.org attractive in abusive workflows.
Why this matters for fraud detection
An email address ending in .eu.org often looks benign and does not immediately stand out as disposable, especially compared to well-known throwaway domains.
But structurally, .eu.org behaves like a free subdomain provider, not an institutional domain. The reputation of the suffix does not reflect the behavior of the subdomains underneath it.
Assuming legitimacy based on the suffix alone creates blind spots. Fraudsters exploit those blind spots by hosting disposable inboxes behind domains that appear more trustworthy than they actually are.
In the next section, we’ll look at concrete examples of disposable email services actively using .eu.org subdomains, and how this shows up at the infrastructure level.
eu.org disposable email domains in the wild
In this section, we look at concrete examples of disposable email services that actively use .eu.org subdomains.
This is not an exhaustive list. These are services we encountered in real traffic and investigated further. The goal is to show how the .eu.org namespace is used in practice to host temporary inboxes, and how these services can be identified using simple, reliable infrastructure signals rather than static domain lists.
A disposable email service hiding in plain sight
One of the most straightforward examples is:
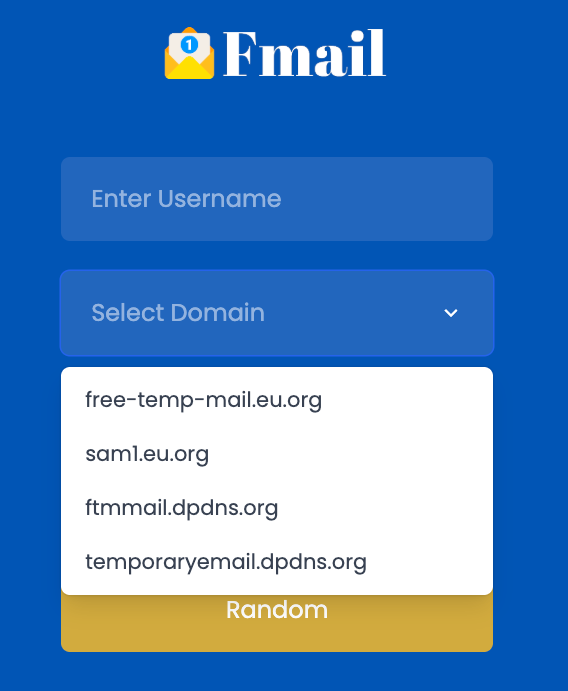
https://free-temp-mail.eu.org/
The intent of the service is explicit. It advertises itself as a temporary email provider and exposes multiple domains, including several under .eu.org.
At the time of writing, the service offered inboxes on the following domains:
free-temp-mail.eu.orgsam1.eu.orgftmmail.dpdns.org
From a fraud perspective, there is nothing ambiguous here. This is a disposable email service using .eu.org to host inboxes that can be created instantly and abandoned just as quickly.
Infrastructure signal: shared mail backend
While the domains look different, their mail infrastructure is not.
Resolving the MX records shows that emails are handled by a dedicated mail host under the same provider-controlled namespace:
host sam1.eu.org
sam1.eu.org has address 188.114.96.2
sam1.eu.org has address 188.114.97.2
sam1.eu.org has IPv6 address 2a06:98c1:3121::2
sam1.eu.org has IPv6 address 2a06:98c1:3120::2
sam1.eu.org mail is handled by 10 mail.sam1.eu.org.
Resolving that mail host:
host mail.sam1.eu.org
mail.sam1.eu.org has address 199.188.203.149
This IP address is shared across all domains operated by this service. Blocking or flagging the backend mail infrastructure is far more effective than reacting to individual domains as they rotate.
When a well-known disposable provider uses eu.org
Yopmail is one of the oldest and most widely used disposable email providers. It regularly rotates and experiments with alternate domains, which it publicly lists here: https://yopmail.com/alternate-domains
Among those domains is the following .eu.org address: mail.nuox.eu.org
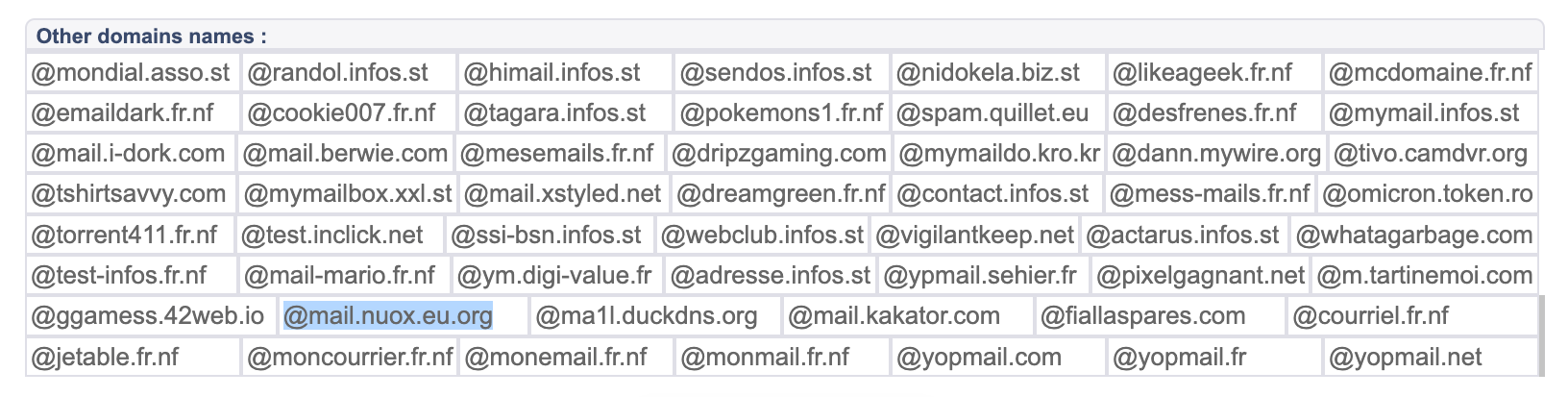
This is a good example of why suffix-based assumptions fail. Even well-known disposable email providers sometimes rely on domains that look less obviously throwaway.
Infrastructure signal: stable SMTP identity
Despite the changing domain names, Yopmail’s mail infrastructure is highly consistent.
Resolving the domain:
host mail.nuox.eu.org
mail.nuox.eu.org has address 87.98.164.155
Reverse DNS immediately reveals the operator:
host 87.98.164.155
155.164.98.87.in-addr.arpa domain name pointer smtp.yopmail.com.
This pattern holds across Yopmail domains. While domain names rotate, the SMTP infrastructure remains stable. This makes MX records and reverse DNS far more reliable signals than domain-level blocklists.
Short-lived eu.org domains backed by tempm.com
Another example is tempm.com, which also provides disposable inboxes through .eu.org subdomains.
Examples observed in the wild include:
huysfd.eu.orghyhta.eu.org
These domains are intentionally generic and short-lived, designed to blend in with legitimate-looking addresses.
Infrastructure signal: MX records pointing to the provider
Here again, MX records immediately expose the backend service:
host huysfd.eu.org
huysfd.eu.org mail is handled by 1 tempm.com.
host hyhta.eu.org
hyhta.eu.org mail is handled by 1 tempm.com.
In this case, blocking or flagging mail servers associated with tempm.com is significantly more robust than chasing individual .eu.org subdomains as they appear and disappear.
Conclusion
An email address that looks institutional or legitimate is not necessarily safe.
The .eu.org examples in this article highlight a broader pattern: fraudsters actively exploit visual trust cues. When a domain suffix sounds European, educational, or official, it becomes a convenient way to bypass both automated checks and human intuition.
This is not specific to .eu.org.
We routinely see the same tactic with fake educational domains. The example below shows a disposable email service issuing addresses that resemble academic emails, such as a fake ohm.edu.pl domain generated by a temporary email provider.
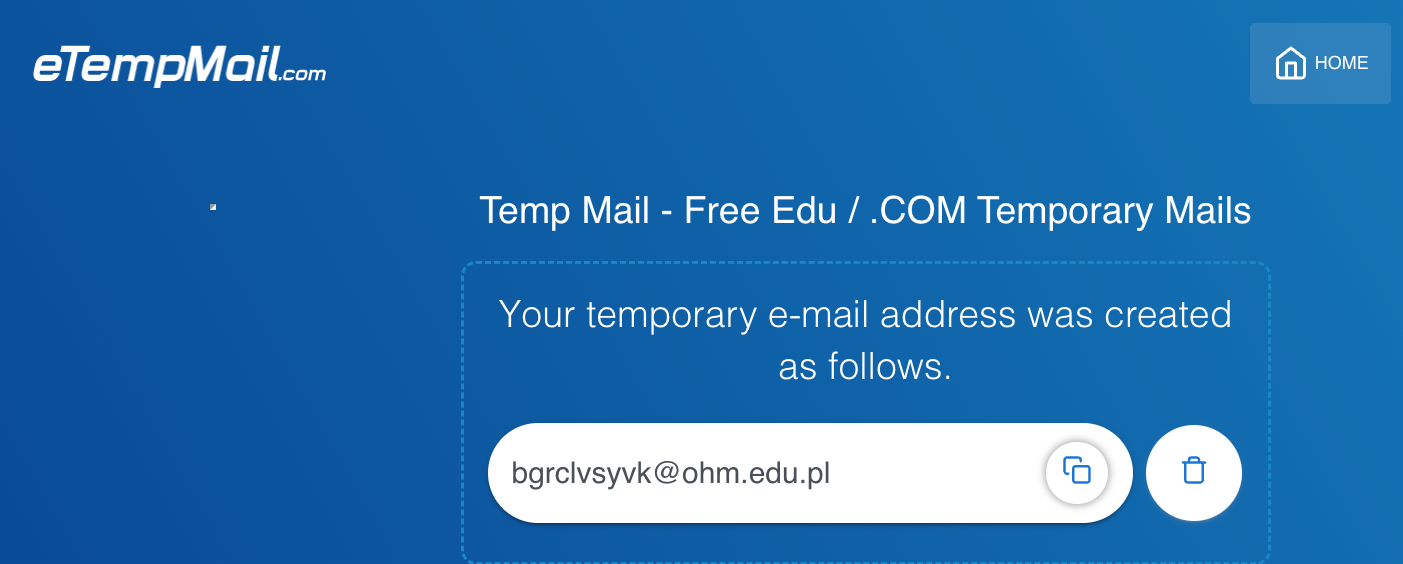
The behavior is always the same. The domain looks legitimate. The infrastructure behind it is disposable.
The practical takeaway is simple: trust should not be inferred from appearance. Email domains need to be evaluated based on infrastructure, behavior, and historical usage, not on how credible they seem at first glance.
For teams protecting signup flows or fighting fake account creation, .eu.org is a useful reminder that legitimacy is something to verify, not something to assume.
*** This is a Security Bloggers Network syndicated blog from The Castle blog authored by Antoine Vastel. Read the original post at: https://blog.castle.io/you-see-an-email-ending-in-eu-org-must-be-legit-right/
如有侵权请联系:admin#unsafe.sh