
好的,我现在需要帮用户总结这篇文章的内容,控制在100字以内,并且不需要特定的开头。首先,我得通读全文,抓住主要信息。 文章讲的是Shadowserver发现超过6000个SmarterMail服务器暴露在线上,可能容易受到攻击。这个漏洞是CVE-2026-23760,属于关键级别,允许未经认证的攻击者劫持管理员账户并执行远程代码。watchTowr公司在1月8日报告了这个问题,SmarterTools在1月15日发布了修复补丁。此外,CISA已经将此漏洞加入到被积极利用的列表中,并要求美国政府机构在三周内修复。 接下来,我需要把这些关键点浓缩到100字以内。要确保包含漏洞名称、影响、发现和修复时间,以及CISA的行动。同时避免使用复杂的术语,让总结简洁明了。 可能的结构是:Shadowserver发现大量服务器暴露,存在关键漏洞CVE-2026-23760,允许攻击者控制服务器。watchTowr报告后已修复。CISA敦促政府机构尽快处理。 这样应该能覆盖所有重要信息,并且符合用户的要求。 </think> Shadowserver发现超6,000个SmarterMail服务器暴露在线并易受攻击。该漏洞(CVE-2026-23760)为关键级别,允许攻击者劫持管理员账户并远程控制服务器。修复补丁已发布,CISA敦促政府机构在三周内完成修复以应对潜在威胁。 2026-1-27 14:15:19 Author: www.bleepingcomputer.com(查看原文) 阅读量:16 收藏

Nonprofit security organization Shadowserver has found over 6,000 SmarterMail servers exposed online and likely vulnerable to attacks exploiting a critical authentication bypass vulnerability.
Cybersecurity company watchTowr reported the security flaw to developer SmarterTools on January 8, which released a fix on January 15 without assigning an identifier.
The vulnerability was later assigned CVE-2026-23760 and rated critical severity, as it allows unauthenticated attackers to hijack admin accounts and gain remote code execution on the host, enabling them to take control of vulnerable servers.
"SmarterTools SmarterMail versions prior to build 9511 contain an authentication bypass vulnerability in the password reset API," according to an advisory added to the NIST national vulnerability database on Thursday.
"The force-reset-password endpoint permits anonymous requests and fails to verify the existing password or a reset token when resetting system administrator accounts. An unauthenticated attacker can supply a target administrator username and a new password to reset the account, resulting in full administrative compromise of the SmarterMail instance."
watchTowr discovered this auth bypass flaw two weeks after finding another critical pre-auth vulnerability in SmarterMail (CVE-2025-52691) that can allow attackers to gain remote code execution on unpatched servers.
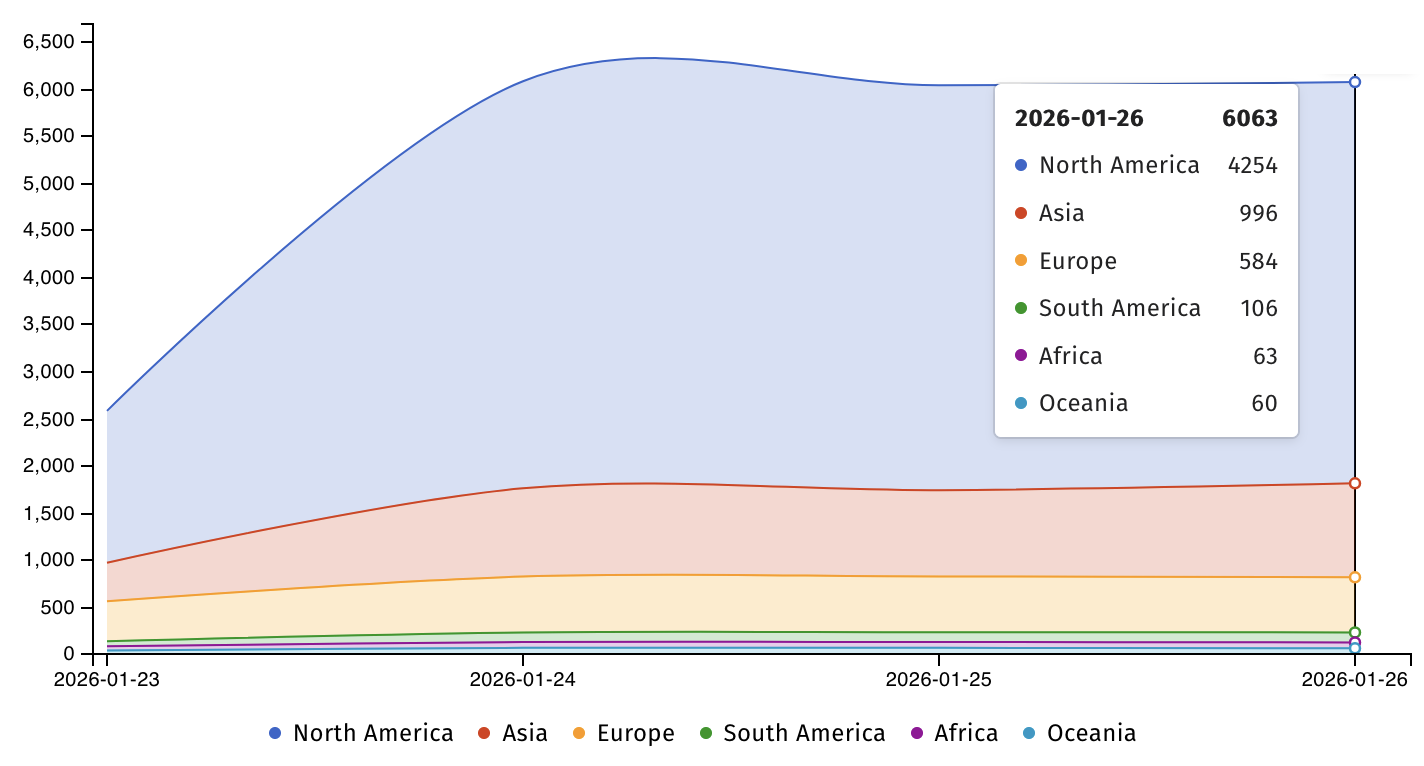
On Monday, Shadowserver revealed that it's tracking over 6,000 SmarterMail servers (more than 4,200 across North America and nearly 1,000 in Asia) flagged as "likely vulnerable" to ongoing CVE-2026-23760 attacks.
Macnica threat researcher Yutaka Sejiyama has also told BleepingComputer that his scans returned over 8,550 SmarterMail instances still vulnerable to CVE-2026-23760 attacks.
watchTowr, who shared a proof-of-concept exploit that only requires prior knowledge of the administrator account's username, noted that it was tipped off about the flaw being exploited in the wild on January 21. Cybersecurity firm Huntress confirmed their report the next day, noting malicious attacks suggesting mass, automated exploitation.
On Monday, CISA added CVE-2026-23760 to its list of actively exploited vulnerabilities, ordering U.S. government agencies to secure their servers within three weeks, by February 16.
"These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise," CISA warned. "Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable."
Yesterday, Shadowserver also reported finding almost 800,000 IP addresses with Telnet fingerprints amid ongoing attacks targeting a critical authentication bypass security flaw in the GNU Inetutils telnetd server.
The 2026 CISO Budget Benchmark
It's budget season! Over 300 CISOs and security leaders have shared how they're planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.
如有侵权请联系:admin#unsafe.sh

