Cybersecurity teams increasingly want to move beyond looking at threats and vulnerabilities in isolation. It's not only about what could go wrong (vulnerabilities) or who might attack (threats), but where they intersect in your actual environment to create real, exploitable exposure.
Which exposures truly matter? Can attackers exploit them? Are our defenses effective?
Continuous Threat Exposure Management (CTEM) can provide a useful approach to the cybersecurity teams in their journey towards unified threat/vulnerability or exposure management.
What CTEM Really Means
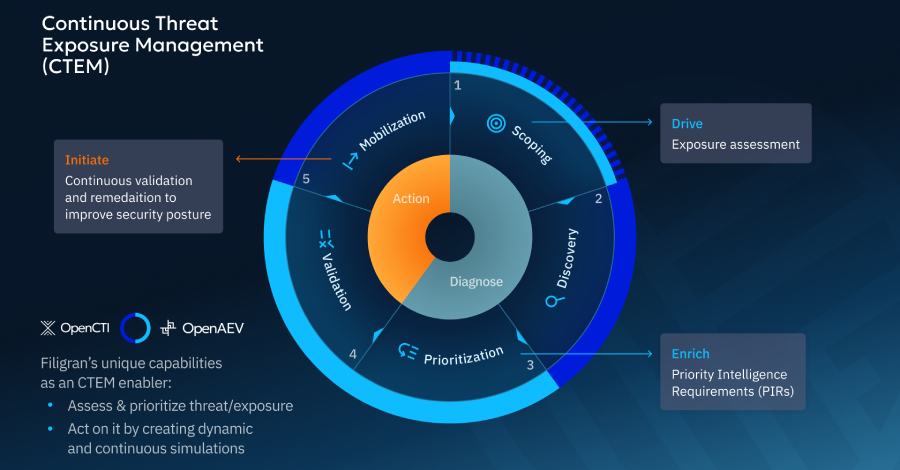
CTEM, as defined by Gartner, emphasizes a 'continuous' cycle of identifying, prioritizing, and remediating exploitable exposures across your attack surface, which improves your overall security posture as an outcome. It's not a one-off scan and a result delivered via a tool; it's an operational model built on five steps:
- Scoping – assess your threats and vulnerabilities and identify what's most important: assets, processes, and adversaries.
- Discovery – Map exposures and attack paths across your environment to anticipate an adversary's actions.
- Prioritization – Focus on what attackers can realistically exploit, and what you need to fix.
- Validation – Test assumptions with safe, controlled attack simulations.
- Mobilization – Drive remediation and process improvements based on evidence
What is the Real Benefit of CTEM
CTEM shifts the focus to risk-based exposure management, integrating lots of sub-processes and tools like vulnerability assessment, vulnerability management, attack surface management, testing, and simulation. CTEM unifies exposure assessment and exposure validation, with the ultimate objective for security teams to be able to record and report potential impact to cyber risk reduction. Technology or tools have never been an issue; in fact, we have a problem of plenty in the cybersecurity space. At the same time, with more tools, we have created more siloes, and this is exactly what CTEM sets out to challenge - can we unify our view into threats/vulnerabilities/attack surfaces and take action against truly exploitable exposure to reduce overall cyber risk?
Role of Threat Intelligence in CTEM
Thousands of vulnerabilities are reported every year (the number was more than 40,000 in 2024), but less than 10% are actually ever exploited. Threat Intelligence can significantly help you zero in on the ones that matter for your organization by connecting vulnerabilities to adversary tactics, techniques, and procedures (TTPs) observed in active campaigns. Threat intelligence is no longer a good-to-have but is a need-to-have. It can help you specify Priority Intelligence Requirements (PIRs): the context, the threat landscape that matters most in your environment. This prioritized threat intelligence tells you which flaws are being weaponized, against which targets, and under what conditions, so you can focus remediation on what's exploitable in your environment, not what's theoretically possible.
The question you should ask your threat intelligence team is: Are you optimizing the value from the threat data you are collecting today? This is your first area of improvement/ change.
Validation Driven Risk Reduction
Prioritized threat intelligence needs to be followed by testing and validation to see how your security controls hold against the most probable exploitables and attack paths, and how it could impact your organization. An important factor here is that your security validation program must go beyond technology; it should also include processes and people. A perfectly tuned EDR, SIEM, or WAF offers limited protection if your incident workflows are unclear, playbooks are outdated, or escalation paths break under pressure. This is where we expect to see a convergence of breach & attack simulation, tabletop exercises, automated pen-testing, etc., towards Adversarial Exposure Validation (AEV).
Avoid the Buzzwords
CTEM isn't a product; it's a strategic approach using outcome-driven metrics for exposure management. Implementation of it doesn't fall on a single security team/function either. It needs to be driven from the top, breaking siloes and improving security workflows across teams. Start with the 'Scoping' stage to decide what to include in your exposure management program and where to focus first:
- What are our top business risks that cybersecurity can directly influence?
- Which environment (on-prem, cloud, IT/OT, subsidiaries…) and asset types (crown jewels, endpoints, identity systems, data stores…) are in scope?
- Do you have an accurate view of this inventory?
- Which threat actors and attack methods are most relevant to our industry and tech stack?
- How will we incorporate existing threat intel and incident data to refine the scope?
- How will we define 'critical exposure' (based on exploitability, business impact, data sensitivity, blast radius, etc.)?
- Are we able to validate tools, people, processes, and tools today?
- What's our initial capacity to remediate issues within this scope (people, tooling, SLAs)?
This is not an exhaustive list, but these questions help define a realistic, risk‑aligned CTEM scope that can be executed and measured, instead of an overly broad but unmanageable effort.
Bottom line:
CTEM works when it answers the questions that matter, with evidence:
What can hurt us? How would it happen? Can we stop it?
For more resources on exposure management, threat intelligence, and validation practices, visit Filigran.
Found this article interesting? This article is a contributed piece from one of our valued partners. Follow us on Google News, Twitter and LinkedIn to read more exclusive content we post.