嗯,用户让我总结一篇文章,控制在100字以内,而且不需要用“文章内容总结”之类的开头。我得先仔细阅读文章,抓住主要信息。 文章讲的是针对俄罗斯用户的多阶段钓鱼攻击,使用了Amnesia RAT和勒索软件。攻击者用假的商业文件作为诱饵,分阶段部署恶意软件。首先,受害者打开压缩包,里面有伪装成文本文件的快捷方式,点击后运行PowerShell脚本下载恶意软件。接着,恶意软件会禁用微软 defender,并通过GitHub和Dropbox分发ayloads。最终阶段部署Amnesia RAT和Hakuna Matata勒索软件,窃取数据并加密文件。 我需要把这些关键点浓缩到100字以内。重点包括:多阶段钓鱼攻击、目标用户、使用的工具、诱饵类型、恶意软件功能以及攻击手段。 可能的结构是:描述攻击类型、目标、诱饵、恶意软件部署过程及其影响。确保信息准确且简洁。 现在试着组织语言:“针对俄罗斯用户的多阶段钓鱼攻击利用假商业文档作为诱饵,分阶段部署Amnesia RAT和勒索软件。攻击者通过GitHub和Dropbox分发payloads,禁用安全软件,并窃取数据及加密文件。” 这样大约85字左右,符合要求。 </think> 针对俄罗斯用户的多阶段钓鱼攻击利用假商业文档作为诱饵,分阶段部署Amnesia RAT和勒索软件。攻击者通过GitHub和Dropbox分发payloads,禁用安全软件,并窃取数据及加密文件。 2026-1-27 09:50:53 Author: securityaffairs.com(查看原文) 阅读量:8 收藏
Amnesia RAT deployed in multi-stage phishing attacks against Russian users

A multi-stage phishing campaign targets users in Russia with ransomware and Amnesia RAT using fake business documents as lures.
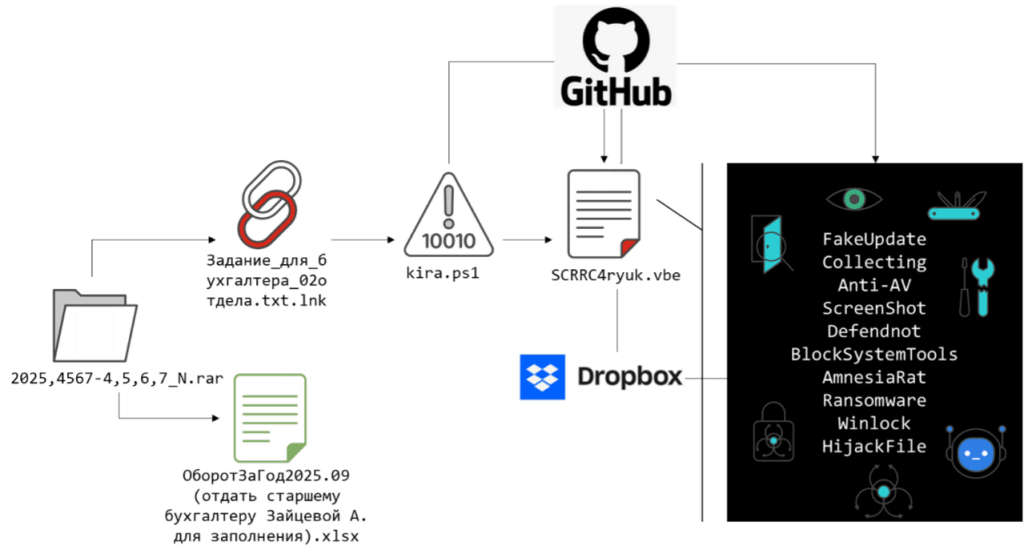
FortiGuard Labs researchers uncovered a multi-stage malware campaign mainly targeting users in Russia. The attack uses fake business documents as social engineering lures to distract victims while malware runs in the background. It escalates to full system compromise, deploying Amnesia RAT and ransomware, disabling Microsoft Defender via the Defendnot tool, and abusing GitHub and Dropbox to host payloads and evade detection.
“The threat actors further increase resilience by separating payload hosting across multiple public cloud services. GitHub is primarily used to distribute scripts, while Dropbox hosts binary payloads.” reads the report published by FortiGuard Labs. “This modular hosting approach allows attackers to update or rotate components independently, complicates takedown efforts, and helps malicious traffic blend into legitimate enterprise network activity.”

The attack chain starts when a victim opens a compressed archive that looks like normal business material. The archive contains fake accounting files with Russian names that match everyday work tasks. Inside, a shortcut file pretends to be a text document for accountants. When the user clicks it, the file launches PowerShell and downloads a script from GitHub. The threat actors do not use exploits; they rely entirely on user interaction, which makes it effective in corporate environments.
The PowerShell script, called kira.ps1, acts as a loader. It hides the PowerShell window to avoid suspicion and creates a fake accounting document on the system. The script opens this document to keep the user busy while malware runs in the background. It also sends a message to the attacker via Telegram to confirm the infection. After a short delay, it downloads and runs an obfuscated VBScript in hidden mode.
“Once written to disk, the decoy document is automatically opened. This reinforces the appearance of a legitimate business task and keeps the user engaged while malicious activity continues in the background.” continues the report. “After establishing this distraction, the script sends an execution confirmation to the attacker using the Telegram Bot API. The message includes user-context information, allowing the attacker to verify that the initial stage has been executed successfully on a live system.”
This second script works as the main controller. It stays encoded on disk and rebuilds the real malicious code only in memory using Base64 and RC4 decoding. This approach limits detection. The final stage initializes system objects, checks for administrator rights, and repeatedly triggers UAC prompts until it gains elevated privileges. Once ready, the malware moves to its final operational phase and continues the attack.
In the final phase, the malware launches its most damaging actions after disabling defenses and blocking recovery. It installs Amnesia RAT to maintain long-term control and steal data. The RAT hides as “svchost.scr”, gains persistence, and steals browser credentials, Telegram sessions, crypto wallets, Discord and Steam data, seed phrases, and detailed system information. It also enables screenshots, audio capture, remote commands, and data exfiltration through Telegram and file-hosting services.
“Amnesia RAT is designed for broad, multi-category data theft combined with real-time surveillance and system control.” continues the report.

Afterward, the attack deploys Hakuna Matata ransomware. This payload encrypts a wide range of files, adds a custom extension, drops ransom notes, changes the wallpaper, kills key processes, and replaces crypto addresses in the clipboard. In parallel, a WinLocker component fully blocks the desktop and shows messages that pressure victims to contact attackers quickly.
“The ransomware maintains a continuous execution loop that actively monitors and hijacks clipboard contents, replacing cryptocurrency wallet addresses with attacker-controlled values.” continues the report. “Combined with encryption, lockout mechanisms, and coercive visual messaging, these behaviors demonstrate an attack model built for maximum leverage, sustained control, and financial extraction.”
Together, these steps ensure maximum disruption, control, and financial leverage.
“This attack chain demonstrates how modern malware campaigns can achieve full system compromise without exploiting software vulnerabilities.” concludes the report. “Instead, the threat actor relies on social engineering, widely trusted platforms such as GitHub and Dropbox, and the abuse of legitimate operating system functionality to stage, deliver, and execute payloads while blending into normal enterprise traffic.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Amnesia RAT)
如有侵权请联系:admin#unsafe.sh