好的,我现在需要帮用户总结一篇文章的内容,控制在100字以内。首先,我得仔细阅读文章,理解其主要内容和重点。 文章主要讲述了2026年1月印度计算机应急响应小组(CERT-In)发布的三个高危安全公告,分别涉及SAP、微软和Atlassian的产品。这些漏洞包括SQL注入、远程代码执行、特权提升等多种类型,可能导致数据泄露、系统被接管等严重后果。文章还提到了每个受影响的产品,并给出了缓解措施,如立即安装补丁。 接下来,我需要将这些信息浓缩到100字以内。首先确定关键点:时间(2026年1月)、发布机构(CERT-In)、漏洞数量(三个)、涉及公司(SAP、微软、Atlassian)、漏洞类型及其影响、建议措施。 然后,组织语言,确保信息完整且简洁。可能的结构是:时间+机构+公告数量+涉及公司+漏洞类型+影响+建议措施。 最后,检查字数是否在限制内,并确保语句通顺。 </think> 2026年1月,CERT-In发布三个高危公告,涉及SAP、微软和Atlassian产品。漏洞包括SQL注入、远程代码执行等,可能引发数据泄露或系统接管。企业需立即安装补丁以应对威胁。 2026-1-27 06:47:16 Author: securityboulevard.com(查看原文) 阅读量:2 收藏
January 2026 was a wake-up month for enterprise security teams. In a single week, CERT-In released three high-severity advisories exposing critical flaws across SAP, Microsoft, and Atlassian, the very platforms that run finance systems, identity layers, developer pipelines, and collaboration tools inside most enterprises. These weren’t theoretical bugs. One Windows vulnerability was already being exploited in the wild. While others enabled remote code execution, privilege escalation, data theft, and full system takeover. If your organization runs SAP S/4HANA, Windows, Azure, Jira, Confluence, or Bitbucket, this wasn’t a patch cycle you could afford to ignore. This article breaks down what was affected, how attackers could abuse these flaws, and exactly what security teams must do to stay ahead before these vulnerabilities turn into breaches.
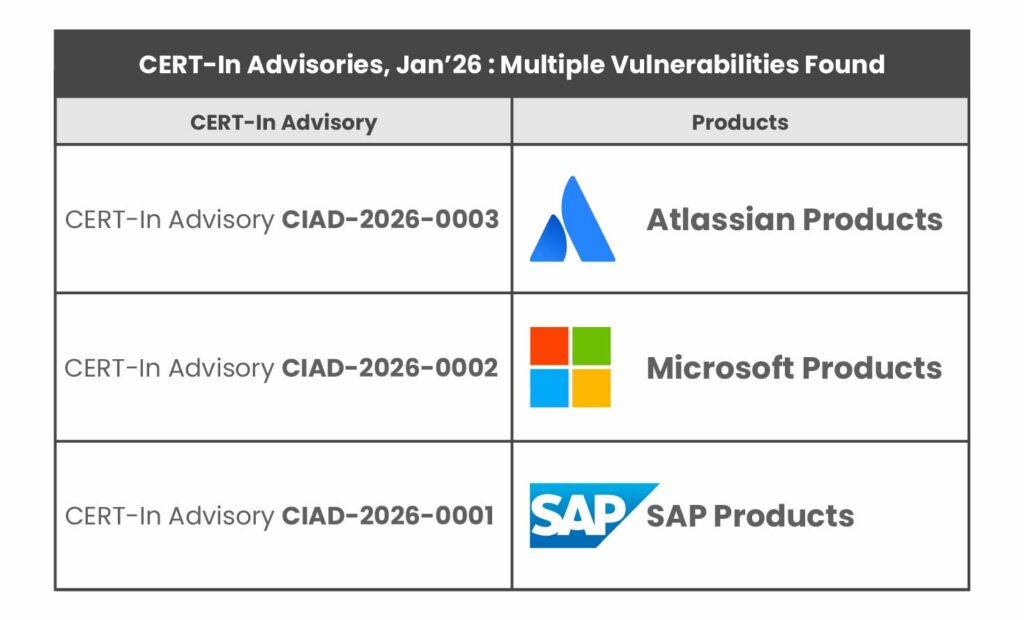
Advisory CIAD-2026-0001: Multiple Vulnerabilities in SAP Products
Summary: On January 13, 2026, CERT-In released an advisory (CIAD-2026-0001) detailing multiple vulnerabilities in various SAP products. These flaws are rated High severity and span a range of attack types including SQL injection, cross-site scripting (XSS), privilege escalation, arbitrary code injection, security bypass, open URL redirection, sensitive information disclosure, and cross-site request forgery (CSRF). In effect, an attacker exploiting these vulnerabilities could perform unauthorized database operations, inject malicious scripts or code, bypass authentication checks, redirect users to malicious sites, or otherwise manipulate SAP systems in unintended ways.
Affected Products
The advisory lists a broad set of SAP components affected by these vulnerabilities. Key affected systems include:
- SAP S/4HANA (Private Cloud and On-Premise) – Financials General Ledger module
- SAP Wily Introscope Enterprise Manager (WorkStation)
- SAP Landscape Transformation
- SAP HANA Database
- SAP Application Server for ABAP and SAP NetWeaver RFC SDK
- SAP Fiori App (Intercompany Balance Reconciliation)
- SAP NetWeaver Application Server ABAP and ABAP Platform
- SAP ERP Central Component / SAP S/4HANA (Enterprise Health Services Management)
- SAP NetWeaver Enterprise Portal
- SAP Business Connector
- SAP Supplier Relationship Management (SRM, SICF Handler in SRM Catalog)
- Business Server Pages (BSP) Application – Product Designer Web UI
- SAP Identity Management
- SAP NetWeaver AS Java (User Management Engine User Mapping)
Mitigation – Immediate remediation:
- SAP administrators should promptly apply the official patches and Security Notes that SAP released as part of its January 2026 update bundle.
- The CERT-In advisory directs organizations to SAP’s January 2026 security advisory page, which contains the necessary fixes for each listed CVE and affected product.
- Ensuring all the above SAP components are updated to their patched versions is critical. In practice, this means installing the relevant SAP Security Notes for each affected module and verifying that the fixes are applied across the SAP landscape.
- Regularly check SAP’s support portal for any additional patches or instructions, and test and deploy these updates on an urgent basis to mitigate the vulnerabilities.
Potential Impact if Unaddressed:
- If left unpatched, these SAP vulnerabilities pose a high risk of system compromise and data breach.
- Attackers could potentially execute arbitrary commands or code on SAP servers, leading to complete takeover of the affected systems. This might result in unauthorized access to sensitive business data (financial records, customer information, etc.), alteration or destruction of critical information, and abuse of legitimate user privileges.
- The advisory explicitly warns of “high risk of data breach” if these issues are not addressed.
In summary, unmitigated SAP vulnerabilities could have severe operational and financial consequences, underscoring the need for immediate remediation.
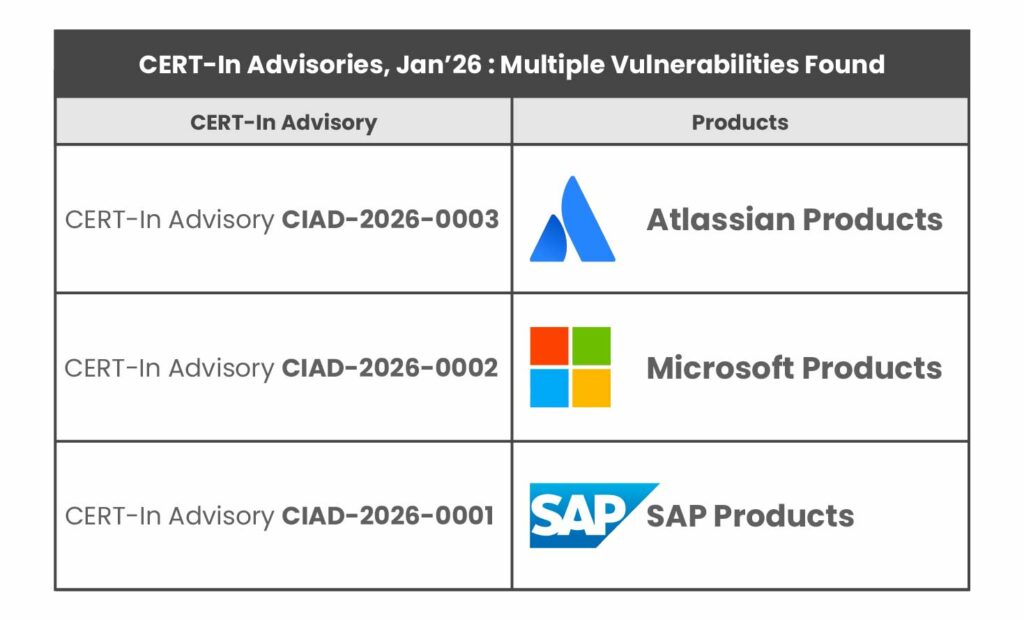
Advisory CIAD-2026-0002: Multiple Vulnerabilities in Microsoft Products
Summary: CERT-In’s advisory CIAD-2026-0002 (issued January 14, 2026) covers multiple vulnerabilities across a spectrum of Microsoft software and cloud services. The advisory notes a High severity rating for these issues. The vulnerabilities could allow attackers to gain elevated privileges, obtain sensitive information, execute remote code, perform spoofing attacks, or cause denial-of-service (DoS) on targeted Microsoft systems.
In essence, an attacker exploiting the most severe of these flaws might completely compromise affected Windows platforms or applications,for example, by running malware with system-level permissions, stealing confidential data, or knocking critical services offline.
Affected Products
A wide range of Microsoft products are affected, reflecting January 2026’s monthly patch release. The advisory specifically mentions:
- Microsoft Office (productivity suite)
- Microsoft Windows (operating system, various versions)
- Extended Security Updates (ESU) for legacy Windows systems
- Microsoft Azure services
- Microsoft Developer Tools (e.g., Visual Studio, .NET components)
- Microsoft SQL Server (database platform)
Mitigation – Immediate remediation:
Apply Microsoft patches immediately: The primary remediation is to install all security updates released by Microsoft in January 2026 as soon as possible. CERT-In’s advisory points to Microsoft’s January 2026 Security Update Guide (MSRC release notes) which contains details on patches for each vulnerability. Given the breadth of products affected, organizations should expedite patch deployment across endpoints, servers, and cloud services. Notably, one of the Windows vulnerabilities (CVE-2026-20805 in the Desktop Window Manager) is actively exploited in the wild, according to the advisory. This means attackers are already targeting unpatched systems, making it critical to patch without delay. In practical terms, IT teams should:
- Ensure Windows OS patches, including those for kernel, driver, and component vulnerabilities, are applied through Windows Update or WSUS.
- Update Microsoft Office applications via Office Update or deployment tools.
- Apply any available fixes to Azure cloud services and verify cloud configurations if advised by Microsoft.
- Update developer tools and SQL Server installations to their patched versions.
Potential Impact if Unaddressed:
- CERT-In’s risk assessment warns of remote code execution, system instability, and sensitive data exposure if these issues are not fixed. In practical terms, an attacker could potentially gain the same privileges as a legitimate user or even SYSTEM privileges on a Windows machine. This could lead to scenarios such as: installing malicious programs or backdoors; viewing, modifying, or exfiltrating confidential data; or creating new accounts with full user rights.
- The advisory explicitly mentions the possibility of ransomware attacks or system crashes resulting from these flaws. For example, a remote code execution vulnerability could be leveraged to deploy ransomware that encrypts critical data and disrupts business operations. An information disclosure bug might silently leak sensitive information, paving the way for targeted attacks or fraud. If a spoofing or privilege escalation vulnerability is left open, threat actors could impersonate users or move laterally through the network, expanding the breach.
Advisory CIAD-2026-0003: Multiple Vulnerabilities in Atlassian Products
Summary: The third advisory (CIAD-2026-0003), dated January 23, 2026, focuses on critical vulnerabilities in Atlassian’s on-premises Data Center and Server product line. Like the others, it carries a High severity rating. These vulnerabilities cover a broad spectrum of issues: the advisory explicitly cites XML External Entity (XXE) injection, Server-Side Request Forgery (SSRF), remote code execution (RCE), man-in-the-middle (MitM), cross-site scripting (XSS), and denial-of-service (DoS) vulnerabilities in various Atlassian applications.
In effect, an attacker could exploit these flaws to inject malicious XML and read restricted files, send crafted requests to internal networks via vulnerable servers, execute arbitrary code on the host, intercept or alter communications, inject malicious scripts in web pages, or overwhelm the system to disrupt service.
Affected Products
CERT-In indicates that the following self-hosted Atlassian products are affected (generally those in Data Center or Server editions):
- Atlassian Bamboo (Data Center & Server) – Continuous integration/build server
- Atlassian Bitbucket (Data Center & Server) – Source code management platform
- Atlassian Confluence (Data Center & Server) – Collaboration wiki platform
- Atlassian Crowd (Data Center & Server) – Identity management SSO system
- Atlassian Jira (Data Center & Server) – Issue and project tracking software
- Atlassian Jira Service Management (Data Center & Server) – IT service management/helpdesk platform
Each of the above may have multiple vulnerabilities addressed in Atlassian’s January 2026 updates. Therefore, organizations using any of these Atlassian products in on-prem or data center deployments should assume they are impacted and review the specific versions and patches required.
Mitigation – Immediate remediation:
Update Atlassian applications:
- The recommended remediation is to apply the fixes provided by Atlassian in their security bulletin dated January 20, 2026.
- Administrators should upgrade each affected Atlassian product to the patched version detailed in that bulletin.
- CERT-In’s advisory provides a reference to Atlassian’s official security advisory, which contains version-specific patch information. It is crucial to follow those instructions promptly.
- Given the severity of RCE and injection vulnerabilities, aim to schedule emergency maintenance windows to update these systems.
- If immediate patching is not possible, consider interim steps such as: disabling or restricting any vulnerable plugins or features if advised by Atlassian, limiting external network access to these applications, and intensifying monitoring on Atlassian servers for any suspicious activity.
- Backup all critical data before applying patches, and verify the integrity of those backups.
Potential Impact if Unaddressed:
- According to CERT-In, there is potential for unauthorized access to Atlassian instances, data manipulation, service disruption, and even compromise of systems integrated with Atlassian products.
- Concretely, a successful exploit could allow attackers to execute arbitrary code on servers hosting tools like Jira or Confluence, effectively giving them control over those systems. This means confidential project data, software source code, and user information stored in these platforms could be accessed or stolen.
- Attackers could modify issues or pages or inject malicious content. A DoS vulnerability could be abused to crash an issue-tracking system or wiki, hampering team productivity and possibly violating service-level agreements for uptime.
- The man-in-the-middle flaws suggest that an attacker might intercept credentials or session tokens if they can position themselves on the network, leading to credential compromise.
- Perhaps most concerning, Atlassian tools are widely integrated into enterprise environments, so a breach in one of these could serve as a stepping stone to infiltrate other connected systems.
The message is clear: today’s most damaging breaches don’t start with obscure systems; they start with trusted enterprise software and one missed patch window. In 2026, patch speed and exposure visibility decide whether advisories become incidents.
Join our weekly newsletter and stay updated
How Kratikal Helps
Kratikal’s AI-powered vulnerability management platform, AutoSecT, continuously identifies exploitable vulnerabilities, correlates them into real-world attack paths, and prioritizes risks that matter most. Backed by VAPT and compliance services, Kratikal accelerates security and intelligent remediation across cloud, application, infrastructure, and human attack surfaces; closing gaps before attackers can exploit them.
FAQs
- What are the most critical CERT-In advisories released in January 2026?
CERT-In released three high-severity advisories in January 2026, CIAD-2026-0001 (SAP), CIAD-2026-0002 (Microsoft), and CIAD-2026-0003 (Atlassian), thus covering vulnerabilities that allow remote code execution, privilege escalation, data theft, spoofing, and denial-of-service across enterprise-critical platforms.
- Which enterprise products are affected by the January 2026 CERT-In advisories?
The advisories impact major platforms including SAP S/4HANA, SAP NetWeaver, Microsoft Windows, Office, Azure, SQL Server, and Atlassian Jira, Confluence, Bitbucket, Bamboo, and Crowd, primarily in on-premise and data-center deployments.
- What should organizations do immediately after a CERT-In critical vulnerability advisory?
Organizations must apply vendor security patches immediately, verify all affected systems are updated, monitor for active exploitation, restrict external access where needed, and review logs for compromise, especially since at least one Windows vulnerability is already being exploited in the wild.
The post Critical CERT-In Advisories – January 2026: SAP, Microsoft, and Atlassian Vulnerabilities appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Puja Saikia. Read the original post at: https://kratikal.com/blog/critical-cert-in-advisories-january-2026/
如有侵权请联系:admin#unsafe.sh