What Is CVE-2026-21962?
CVE-2026-21962 is a critical (CVSS 10.0) vulnerability in the Oracle HTTP Server and the WebLogic Server Proxy Plug-in for Apache HTTP Server and Microsoft IIS. An unauthenticated attacker with HTTP access can exploit this flaw by sending crafted requests to the affected proxy components and bypass security controls. Successful exploitation can result in unauthorized creation, deletion, or modification of critical data, or full compromise of all data accessible through the affected servers.
The vulnerability affects multiple supported versions, including:
- Oracle HTTP Server and WebLogic Server Proxy Plug-in (Apache): 12.2.1.4.0, 14.1.1.0.0, 14.1.2.0.0
- WebLogic Server Proxy Plug-in for IIS: 12.2.1.4.0
Key aspects of the vulnerability include:
- Unauthenticated network access: Exploitation does not require credentials or user interaction.
- Low attack complexity: Attackers can exploit the issue with standard HTTP traffic.
- Maximum severity: With a CVSS score of 10.0, this is a top-tier risk for confidentiality and integrity impact.
Observations from Our Data
Since this CVE’s release, we’ve seen:
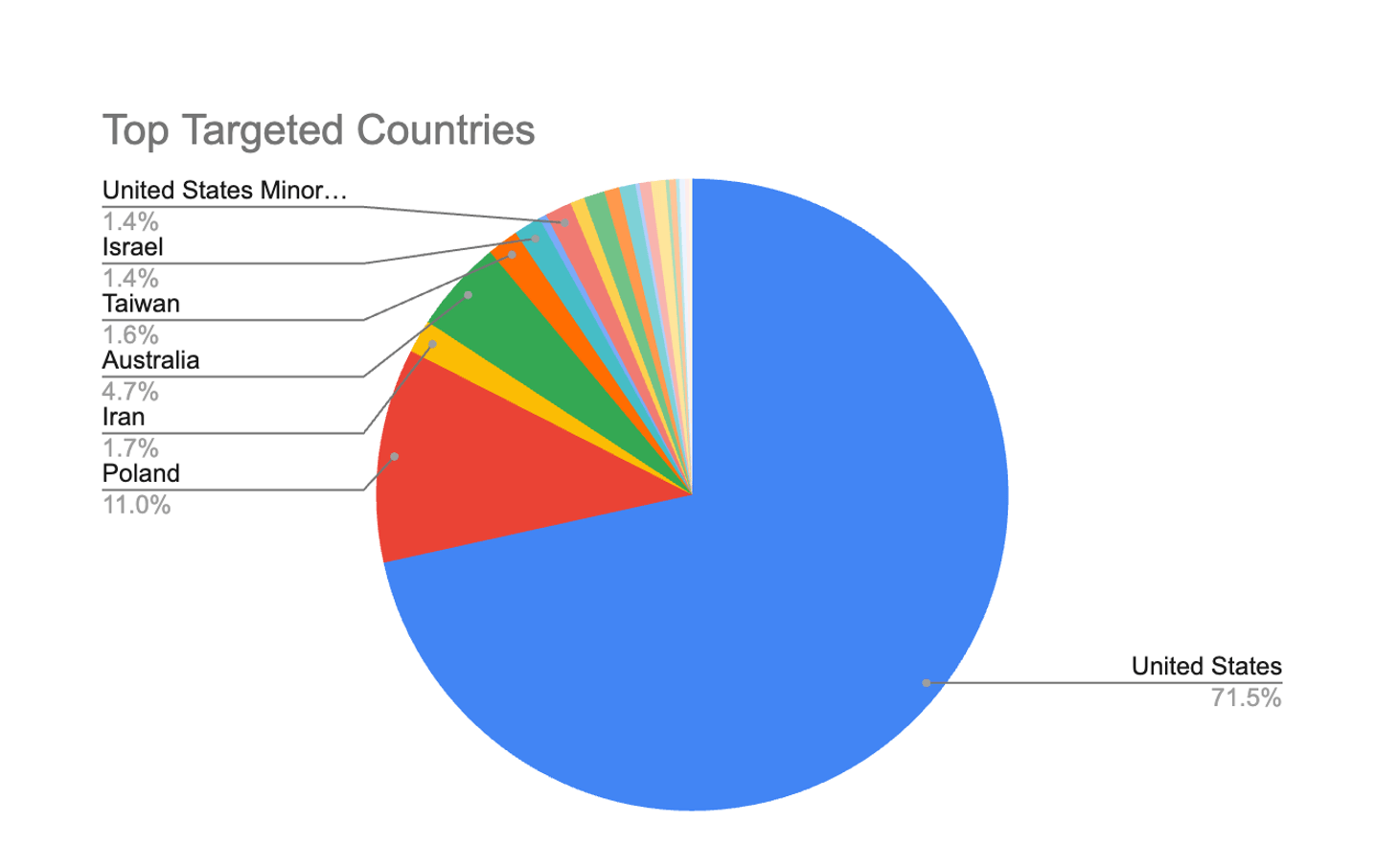
- Over 140,000 attack attempts, targeting 21 countries globally. Almost 75% of attacks target US-based sites, followed by Poland.
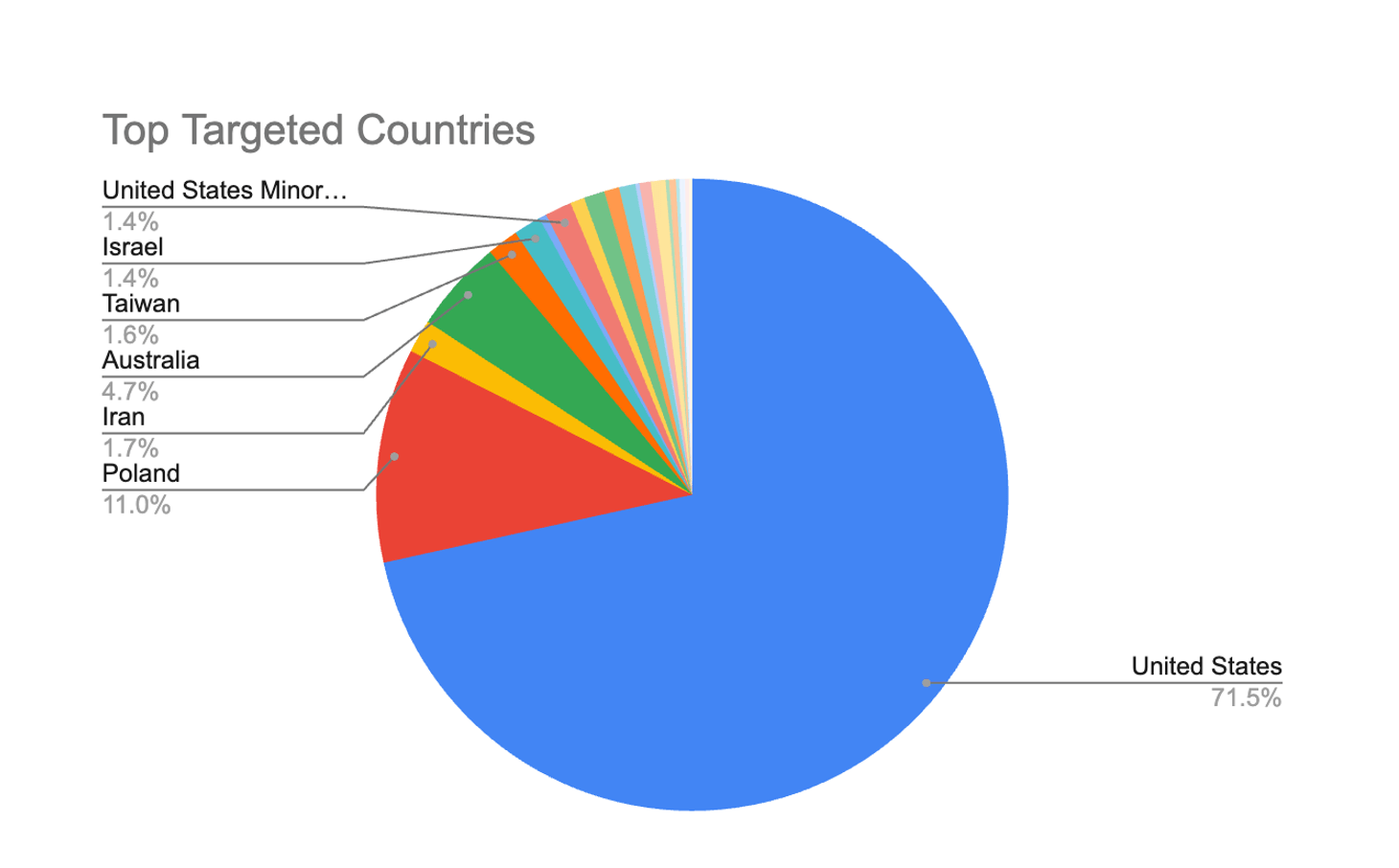
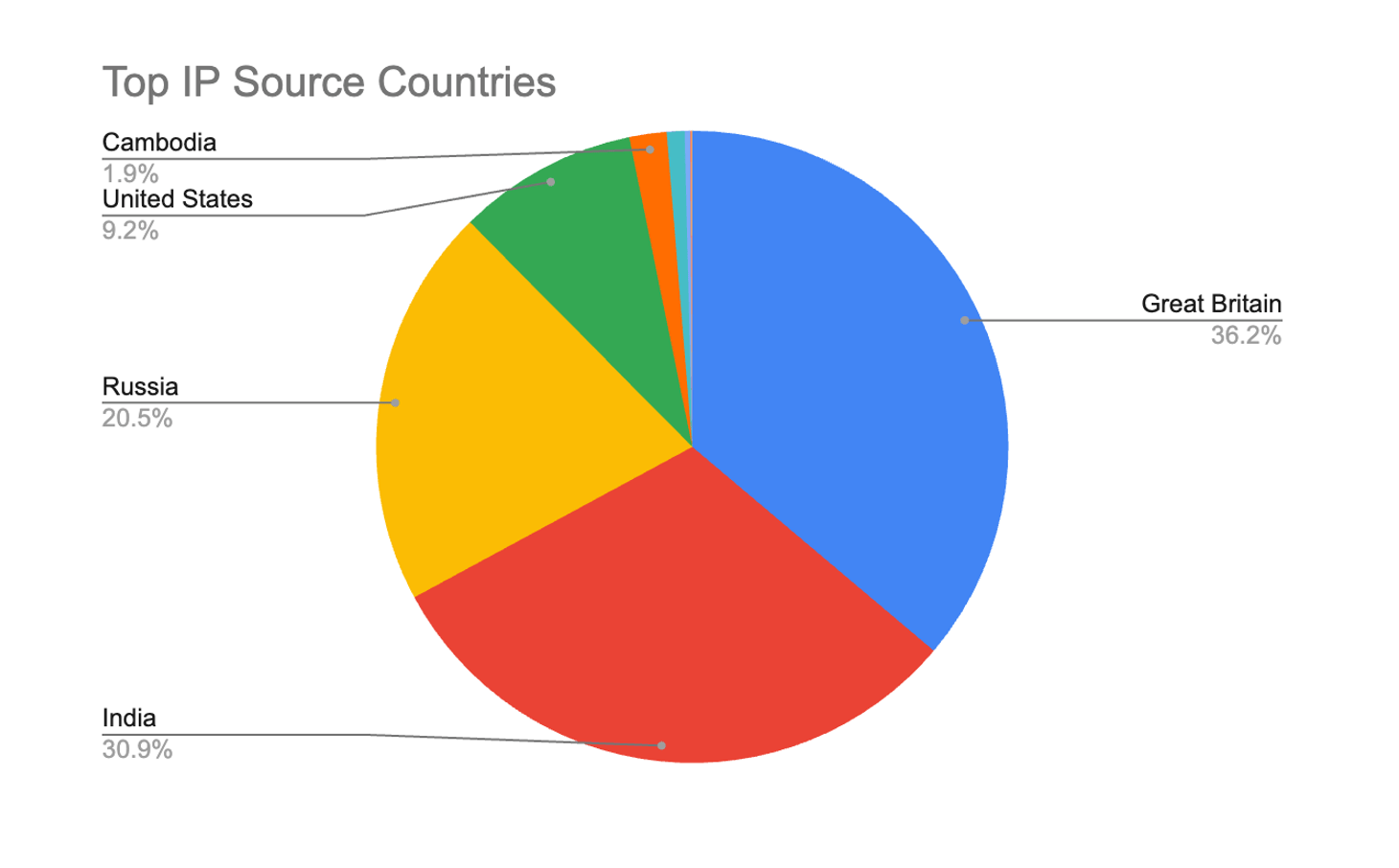
- Attacks from 9 source countries.
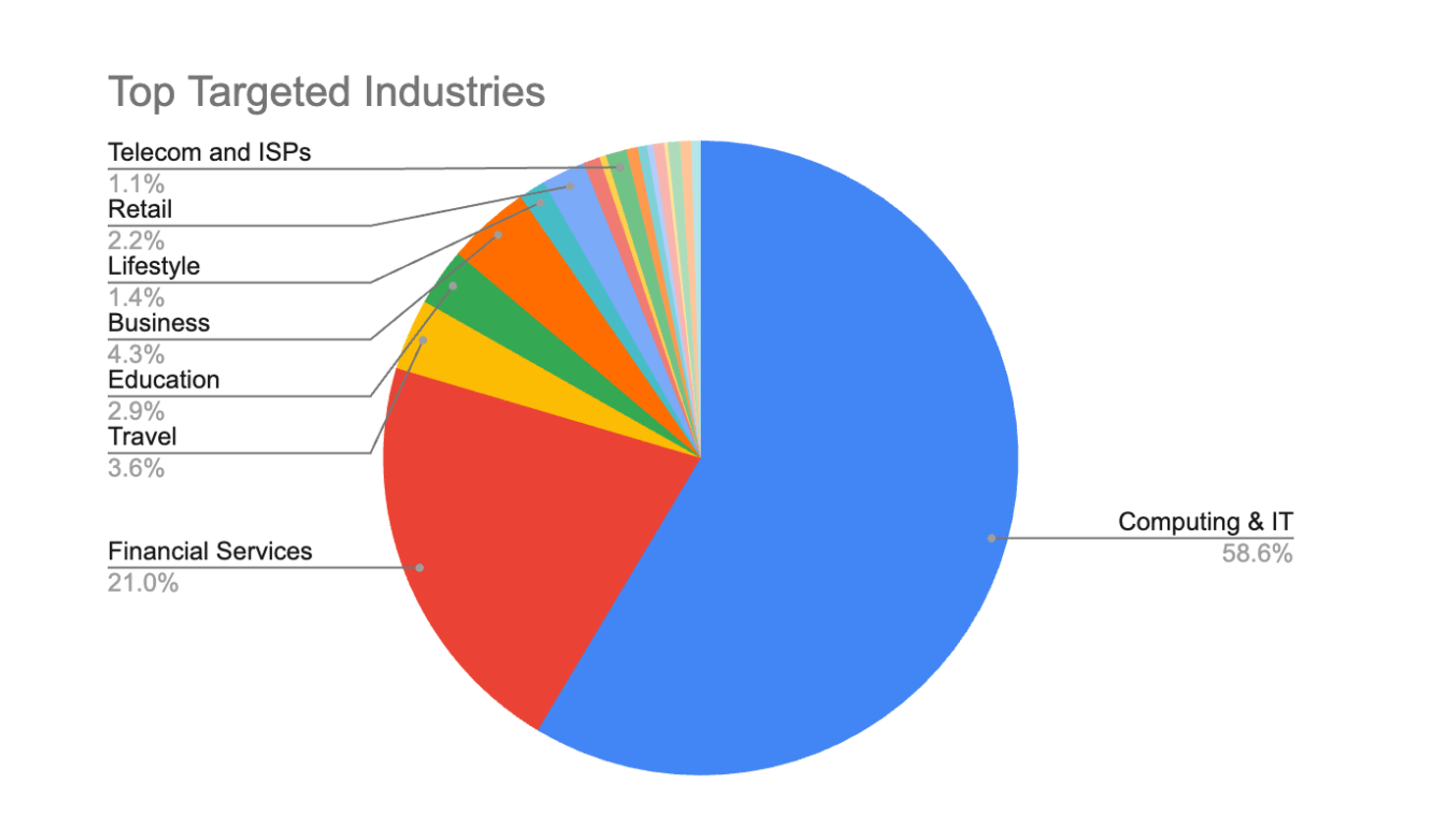
- Attacks targeting sites across 18 industries, primarily Computing and IT.
Mitigation and Protection
The definitive remediation for CVE-2026-21962 is applying Oracle’s January 2026 Critical Patch Update for all affected versions. Administrators should prioritize this patch given the severity of the issue.
Imperva customers using both CWAF and WAF Gateway are protected out-of-the-box.
Conclusion
CVE-2026-21962 represents a critical perimeter security risk for organizations running Oracle HTTP Server and WebLogic Proxy Plug-in components. Its combination of unauthenticated access, low attack complexity, and maximum CVSS rating makes it a high-priority patching and detection concern.
Imperva customers are protected against exploitation techniques associated with this vulnerability through our web application firewall and advanced HTTP traffic inspection capabilities. For any Oracle HTTP Server and WebLogic Proxy Plug-in users still running legacy proxy deployments, we strongly advise accelerating patch deployment and reviewing exposure based on your internal telemetry.
The post Imperva Customers Protected Against CVE-2026-21962 in Oracle HTTP and WebLogic appeared first on Blog.
*** This is a Security Bloggers Network syndicated blog from Blog authored by Gabi Sharadin. Read the original post at: https://www.imperva.com/blog/imperva-customers-protected-against-cve-2026-21962-in-oracle-http-and-weblogic/