好的,我现在需要帮用户总结一篇文章的内容,控制在100字以内。用户的要求很明确,不需要以“文章内容总结”或“这篇文章”开头,直接写描述即可。 首先,我仔细阅读了用户提供的文章。文章主要讲的是一个严重的安全漏洞CVE-2026-24061,影响GNU InetUtils的telnetd服务器。这个漏洞允许攻击者绕过身份验证,直接以root权限登录。Shadowserver追踪了近80万暴露在互联网上的Telnet实例,其中大部分来自亚洲、南美洲和欧洲。攻击者利用这个漏洞进行有限的攻击,GreyNoise已经检测到相关活动。 接下来,我需要提取关键信息:漏洞名称、影响范围、攻击方式、受影响设备数量及分布、攻击情况以及建议的应对措施。 然后,我要把这些信息浓缩成一句话,确保不超过100字。需要注意的是,要直接描述内容,不使用开头模板。 最后,检查是否有遗漏的重要信息,并确保语言简洁明了。 </think> 文章指出GNU InetUtils telnetd服务器存在严重认证绕过漏洞(CVE-2026-24061),攻击者可利用该漏洞以root权限登录。Shadowserver追踪到近80万暴露的Telnet实例,其中38万来自亚洲。GreyNoise检测到针对该漏洞的有限攻击活动。建议管理员升级设备或禁用telnetd服务以应对威胁。 2026-1-26 15:30:25 Author: www.bleepingcomputer.com(查看原文) 阅读量:1 收藏

Internet security watchdog Shadowserver tracks nearly 800,000 IP addresses with Telnet fingerprints amid ongoing attacks exploiting a critical authentication bypass vulnerability in the GNU InetUtils telnetd server.
The security flaw (CVE-2026-24061) impacts GNU InetUtils versions 1.9.3 (released 11 years ago in 2015) through 2.7 and was patched in version 2.8 (released on January 20).
"The telnetd server invokes /usr/bin/login (normally running as root) passing the value of the USER environment variable received from the client as the last parameter," explained open-source contributor Simon Josefsson, who reported it.
"If the client supply a carefully crafted USER environment value being the string "-f root", and passes the telnet(1) -a or --login parameter to send this USER environment to the server, the client will be automatically logged in as root bypassing normal authentication processes."
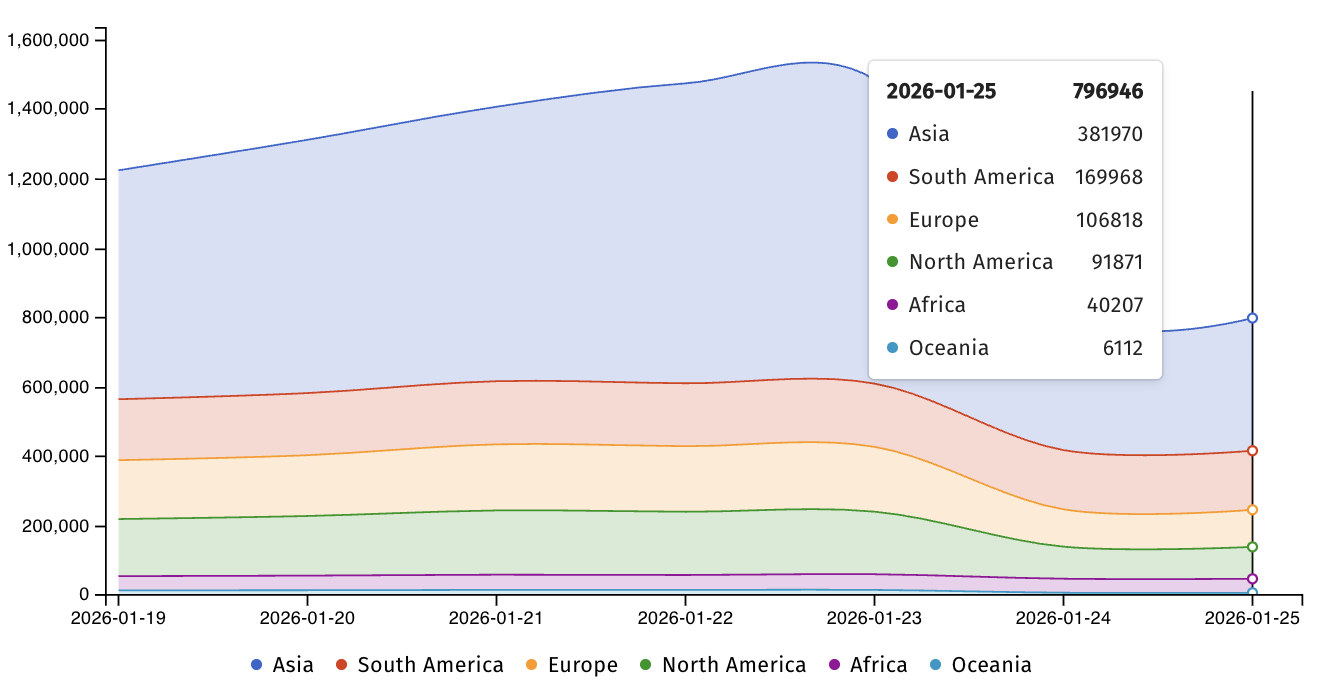
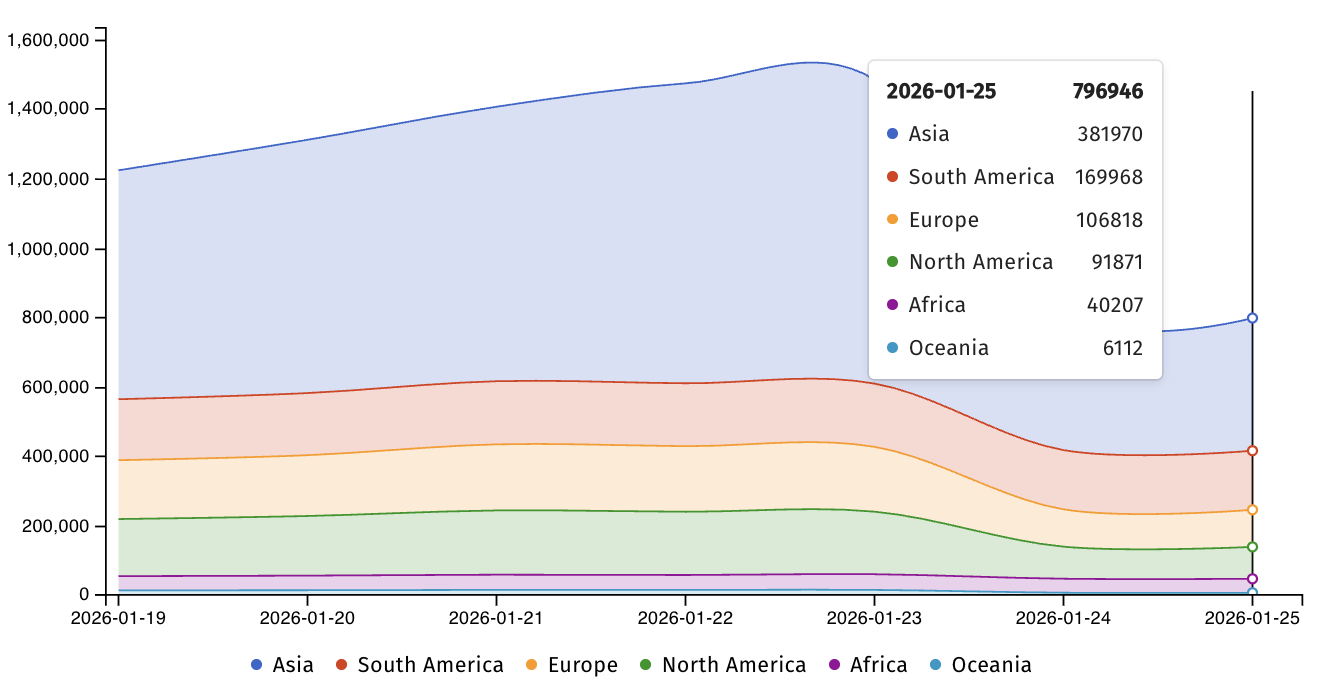
Today, Shadowserver said that it's tracking nearly 800,000 IP addresses with Telnet fingerprints, over 380,000 from Asia, almost 170,000 from South America, and just over 100,000 from Europe. However, there is no information regarding how many of these devices have been secured against CVE-2026-24061 attacks.
"We are ~800K telnet instances exposed globally - naturally, they should not be. [..] Telnet should not be publicly exposed, but often is especially on legacy iot devices," said Shadowserver Foundation CEO Piotr Kijewski.
GNU InetUtils is a collection of network utilities (including telnet/telnetd, ftp/ftpd, rsh/rshd, ping, and traceroute) used across multiple Linux distributions that can run without updates for more than a decade on many legacy and embedded devices. This explains its presence in IoT devices, as noted by Kijewski.
On Thursday, days after CVE-2026-24061 was disclosed, cybersecurity company GreyNoise reported that it had already detected exploits for CVE-2026-24061 being used in limited attacks.
The malicious activity started on January 21 (one day after the vulnerability was patched) and originated from 18 IP addresses across 60 Telnet sessions, abusing the Telnet IAC option negotiation to inject 'USER=-f <user>' and grant attackers' shell access to compromised devices without authentication.
While these attacks varied in terminal speed and X11 DISPLAY values, they targeted the 'root' user in 83.3% of the cases. Also, even though most of them appear automated, GreyNoise observed some "human-at-keyboard" cases.
After gaining access, the attackers also attempted to deploy Python malware following automated reconnaissance, but these attempts failed due to missing directories and binaries.
Admins who can't immediately upgrade their devices to the patched release are advised to disable the vulnerable telnetd service or block TCP port 23 on all firewalls.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you're cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
如有侵权请联系:admin#unsafe.sh

