嗯,用户让我帮忙总结一篇文章的内容,控制在一百个字以内,而且不需要用“文章内容总结”或者“这篇文章”这样的开头,直接写描述。好的,我先看看用户给的文章内容。 文章主要讲的是Gootloader恶意软件的新变化,它现在使用一个畸形的ZIP存档来逃避检测。这个ZIP存档是通过拼接多达1000个存档来实现的。这样做导致很多分析工具崩溃,因为它们无法处理这么大的文件或者结构异常。 然后,文章提到这个恶意软件是一个JScript文件,虽然Windows自带的工具可以解压它,但依赖7-Zip和WinRAR的工具就失败了。攻击者还用了其他技巧,比如随机化磁盘号、添加元数据不匹配、生成独特的样本等等。 执行后,恶意软件会在启动文件夹中添加快捷方式来保持持久性,并通过Windows Script Host和PowerShell来执行后续操作。研究人员建议修改默认应用来打开JScript文件,并阻止wscript.exe和cscript.exe执行下载的内容。 用户的需求是总结这篇文章,控制在100字以内。我需要抓住关键点:Gootloader的新方法、使用畸形ZIP、逃避检测、导致工具崩溃、以及防御建议。 现在开始组织语言:Gootloader恶意软件通过拼接多达1000个ZIP存档形成畸形文件,导致分析工具崩溃。虽然Windows能解压,但7-Zip和WinRAR不行。攻击者还用了其他反解析技巧。一旦执行,会在启动文件夹中添加快捷方式以保持持久性,并通过脚本和PowerShell执行操作。研究人员建议修改默认应用和阻止特定可执行文件。 检查字数:大概在100字左右。确保没有使用“文章内容总结”之类的开头。 </think> Gootloader恶意软件通过拼接多达1,000个ZIP存档形成畸形文件以逃避检测,导致分析工具崩溃。该恶意软件利用Windows默认解压工具运行JScript代码,并在启动文件夹中添加快捷方式以保持持久性。研究人员建议修改默认应用以防止JScript执行,并阻止wscript.exe和cscript.exe运行下载内容。 2026-1-15 23:0:19 Author: www.bleepingcomputer.com(查看原文) 阅读量:0 收藏

The Gootloader malware, typically used for initial access, is now using a malformed ZIP archive designed to evade detection by concatenating up to 1,000 archives.
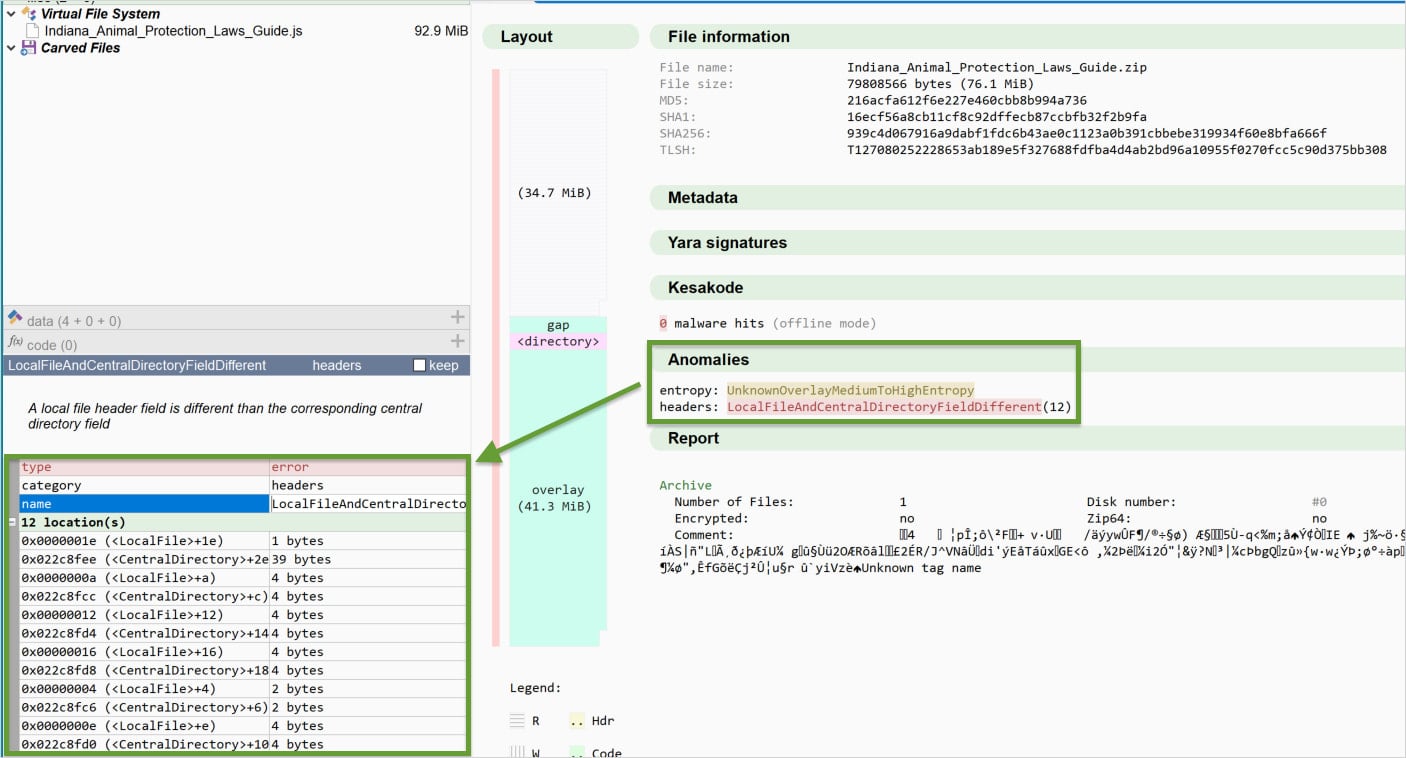
In doing so, the malware, which is an archived JScript file, causes many tools to crash when trying to analyze it.
According to researchers, the malicious file is successfully unpacked using the default utility in Windows, but tools relying on 7-Zip and WinRAR fail.
To achieve this, the threat actor behind the malware concatenates between 500 and 1,000 ZIP archives, but also uses other tricks to make parsing from analysis tools more difficult.
The Gootloader malware loader has been active since 2020 and is used by various cybercriminal operations, including ransomware deployments.
After a seven-month break, the operation returned last November, as reported by security researchers at Huntress Labs and the DFIR Report.
While malformed ZIP archives were present back then, they came with minimal modifications, and there were filename mismatches when trying to extract the data.
To further strengthen the anti-analysis of this stage, Gootloader operators have now implemented far more extensive obfuscation mechanisms, according to Expel researchers analyzing more recent samples.
Specifically, the following mechanisms are now used to evade detection and analysis:
- Concatenate up to a thousand ZIP archives, exploiting the fact that parsers read from the end of the file.
- Use a truncated End of Central Directory (EOCD) that misses two mandatory bytes, breaking the parsing by most tools.
- Randomize disk number fields, causing tools to expect non-existent multi-disk archives.
- Add metadata mismatches between the Local File Headers and Central Directory entries.
- Generate unique ZIP and JScript samples for each download to evade static detection.
- Deliver the ZIP as an XOR-encoded blob, which is decoded and repeatedly appended client-side until it reaches the desired size, evading network-based detection.
Source: Expel
Once executed on the host, the malware’s JScript activates via Windows Script Host (WScript) from a temporary directory and establishes persistence by adding shortcut (.LNK) files to the Startup folder that point to a second JScript file.
This payload is executed upon first launch, and with every system boot, triggering CScript with NTFS shortnames, followed by PowerShell spawning PowerShell.
While Gootloader’s authors added multiple corruption techniques to evade detection without breaking functionality, Expel researchers used the structural anomalies that allow defenders to spot the threat. The team also shared a YARA rule that "can consistently identify the current ZIP archives."
The detection relies on spotting a specific combination of ZIP header features, hundreds of repeating Local File Headers, and EOCD records.
The researchers recommend that defenders change the default application for opening JScript files to Notepad instead of Windows Script Host, to prevent their execution.
To reduce the attack surface, Expel advises blocking wscript.exe and cscript.exe from executing downloaded content if JScript files are not needed.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you're cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
如有侵权请联系:admin#unsafe.sh

