好的,我现在需要帮用户总结这篇文章的内容,控制在100字以内。首先,我得通读整篇文章,抓住主要信息。 文章讲的是BreachForums黑客论坛的数据泄露事件。这个论坛以前被执法部门查封过,现在又出现了新的泄露。泄露的内容包括用户的数据库表和PGP私钥。用户数据有32万多条记录,其中大部分IP地址是127.0.0.9,没什么用处,但有7万多条是真实的公共IP地址,这对执法机构有价值。此外,泄露的PGP私钥虽然被保护了密码,但如果密码被破解,可能会被滥用。 管理员回应说这是个旧备份文件被临时暴露了,并且否认了论坛是执法部门 honeypot 的说法。他们建议用户使用一次性邮箱来降低风险。 总结的时候要包括:BreachForums的数据泄露、泄露内容、数据量、IP地址情况、PGP私钥的情况以及管理员的回应。同时要保持简洁,控制在100字以内。 可能的结构:BreachForums黑客论坛的数据泄露事件导致用户数据库和PGP私钥泄露。32万条记录中部分IP有效,对执法有帮助。管理员称是旧备份意外暴露,并否认论坛为honeypot。 </think> BreachForums黑客论坛遭遇数据泄露,用户数据库表及PGP私钥外泄。323,988条记录中部分IP地址可追踪至真实位置,对执法有价值。管理员称系旧备份意外暴露,并否认论坛为执法部门陷阱。 2026-1-10 18:30:23 Author: www.bleepingcomputer.com(查看原文) 阅读量:5 收藏

The latest incarnation of the notorious BreachForums hacking forum has suffered a data breach, with its user database table leaked online.
BreachForums is the name of a series of hacking forums used to trade, sell, and leak stolen data, as well as sell access to corporate networks and other illegal cybercrime services.
The site was launched after the first of these forums, RaidForums, was seized by law enforcement, with the owner, "Omnipotent", arrested.
While BreachForums has suffered data breaches and police actions in the past, it has been repeatedly relaunched under new domains, with some accusing it of now being a honeypot for law enforcement.
Yesterday, a website named after the ShinyHunters extortion gang released a 7Zip archive named breachedforum.7z.
This archive contains three files named:
- shinyhunte.rs-the-story-of-james.txt
- databoose.sql
- breachedforum-pgp-key.txt.asc
A representative of the ShinyHunters extortion gang told BleepingComputer they are not affiliated with the site that distributed this archive.
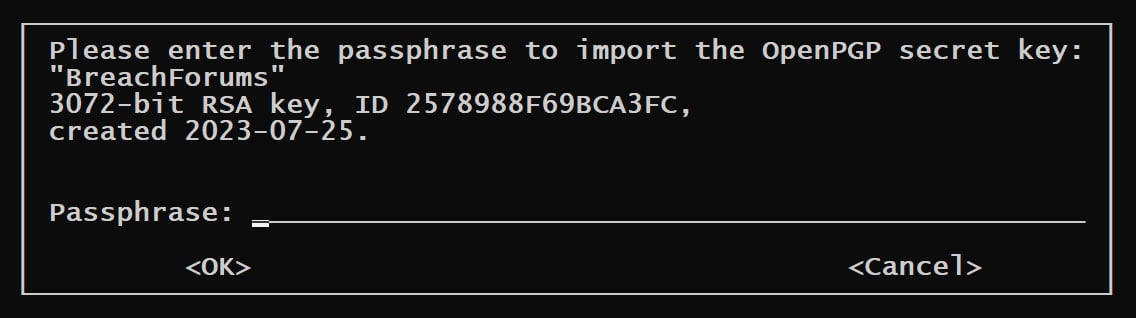
The archive's 'breachedforum-pgp-key.txt.asc' file is the PGP private key created on July 25, 2023, and used by BreachForums to sign official messages from the administrators. While the key has been leaked, it is passphrase-protected, and without the password, it can't be abused to sign messages.
Source: BleepingComputer
The "databoose.sql" file is a MyBB users database table (mybb_users) containing 323,988 member records that include member display names, registration dates, IP addresses, and other internal information.
BleepingComputer's analysis of the table shows that most of the IP addresses map back to a local loopback IP address (0x7F000009/127.0.0.9), so they are not of much use.
However, 70,296 records do not contain the 127.0.0.9 IP address, and the records we tested map to a public IP address. These public IP addresses could be an OPSEC concern for those people and valuable to law enforcement and cybersecurity researchers.
The last registration date in the newly leaked user database is from August 11, 2025, which is the same day that the previous BreachForums at breachforums[.]hn was closed. This shutdown followed the arrest of some of its alleged operators.
That same day, a member of the ShinyHunters extortion gang posted a message on the "Scattered Lapsus$ Hunters" Telegram channel, claiming the forum was a law-enforcement honeypot. The BreachForums administrators subsequently denied these allegations.
The breachforums[.]hn domain was later seized by law enforcement in October 2025 after it was repurposed to extort companies impacted by the widespread Salesforce data theft attacks conducted by the ShinyHunters extortion group.
The current BreachForums administrator, known as "N/A," has acknowledged the new breach, stating that a backup of the MyBB user database table was temporarily exposed in an unsecured folder and downloaded only once.
"We want to address recent discussions regarding an alleged database leak and clearly explain what happened," N/A wrote on BreachForums.
"First of all, this is not a recent incident. The data in question originates from an old users-table leak dating back to August 2025, during the period when BreachForums was being restored/recovered from the .hn domain."
"During the restoration process, the users table and the forum PGP key were temporarily stored in an unsecured folder for a very short period of time. Our investigation shows that the folder was downloaded only once during that window," continued the administrator.
While the administrator said that BreachForums members should use disposable email addresses to reduce risk and that most IP addresses mapped to local IPs, the database still contains information that could be of interest to law enforcement.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you're cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
如有侵权请联系:admin#unsafe.sh

