文章指出,尽管组织在网络安全方面投入巨大,但SaaS应用及其连接的第三方工具仍存在重大风险。配置错误和过度授权的API访问成为主要威胁。传统安全措施难以应对这些动态环境中的问题。 2026-1-9 18:1:57 Author: www.guidepointsecurity.com(查看原文) 阅读量:4 收藏
Organizations have spent years hardening endpoints, tightening identity controls, and investing in next-generation defenses across on-prem and cloud environments. Yet one of the most pervasive risks in today’s operating landscape is also one of the least visible: the silent, sprawling, constantly shifting ecosystem of Software as a Service (SaaS) applications and everything connected to them. So then, what are organizations doing about SaaS security? The answer is… most likely, not enough.
SaaS has become the backbone of modern business. Customer Relationship Management (CRM) tools run revenue pipelines. Collaboration tools run global communication. Human Resources platforms run workforce operations. But as organizations push mission-critical workflows into SaaS, two risk layers have grown faster than most security teams can track: misconfigurations hidden deep inside SaaS applications, and third-party integrations that extend far beyond them. Each represents a major, and often underestimated and overlooked, attack surface.
The result is a new class of cybersecurity exposure: one that doesn’t show up in malware alerts, vulnerability scans, or network logs. It hides in permissions, scopes, tokens, automation rules, and API connections. And threat actors know it.
The Misconfiguration Crisis: SaaS Settings as the New Shadow IT
SaaS platforms are known for being exceptionally flexible, which is useful, but also can introduce complexity. And complexity means risk. While traditional security controls have matured, SaaS configurations remain largely under-monitored and inconsistently governed. The most damaging vulnerabilities in SaaS often stem from those very settings that make the tools so flexible and useful.
Hidden misconfigurations are now functionally equivalent to shadow IT. They bypass oversight, expose sensitive information, and often persist for months or years because no one is looking in the right place.
Misconfigurations frequently go undetected because:
- SaaS platforms evolve continuously atop rapid feature delivery schedules and automated self-updates. Each update has the potential of introducing new settings, new permissions, and new default behaviors. Sometimes, updates can even undo or reset configurations regardless of previous tuning.
- Manual configuration audits are time-consuming, inconsistent, and error-prone across dozens of apps. Meanwhile, organizations often lack a comprehensive list of SaaS apps across their IT network, let alone the configurations of each. The lack of automation and control compounds the security issues that multiply with each new and updated SaaS app.
- The complexity of fine-grained access controls makes it easy for misalignments to slip through unnoticed. Additionally, SaaS apps that are not integrated into an organization’s RBAC and/or SSO platforms require additional oversight that they most likely are not getting.
The business impact is anything but invisible. Misconfigurations drive data exposure, compliance violations, operational disruptions, and reputational damage. And because SaaS platforms are so deeply woven into corporate workflows, exploitation of even a minor misconfiguration can cascade across teams, processes, and partners. It introduces a systemic risk that cannot be ignored.
The Integration Layer: The Largest Attack Surface No One Is Watching
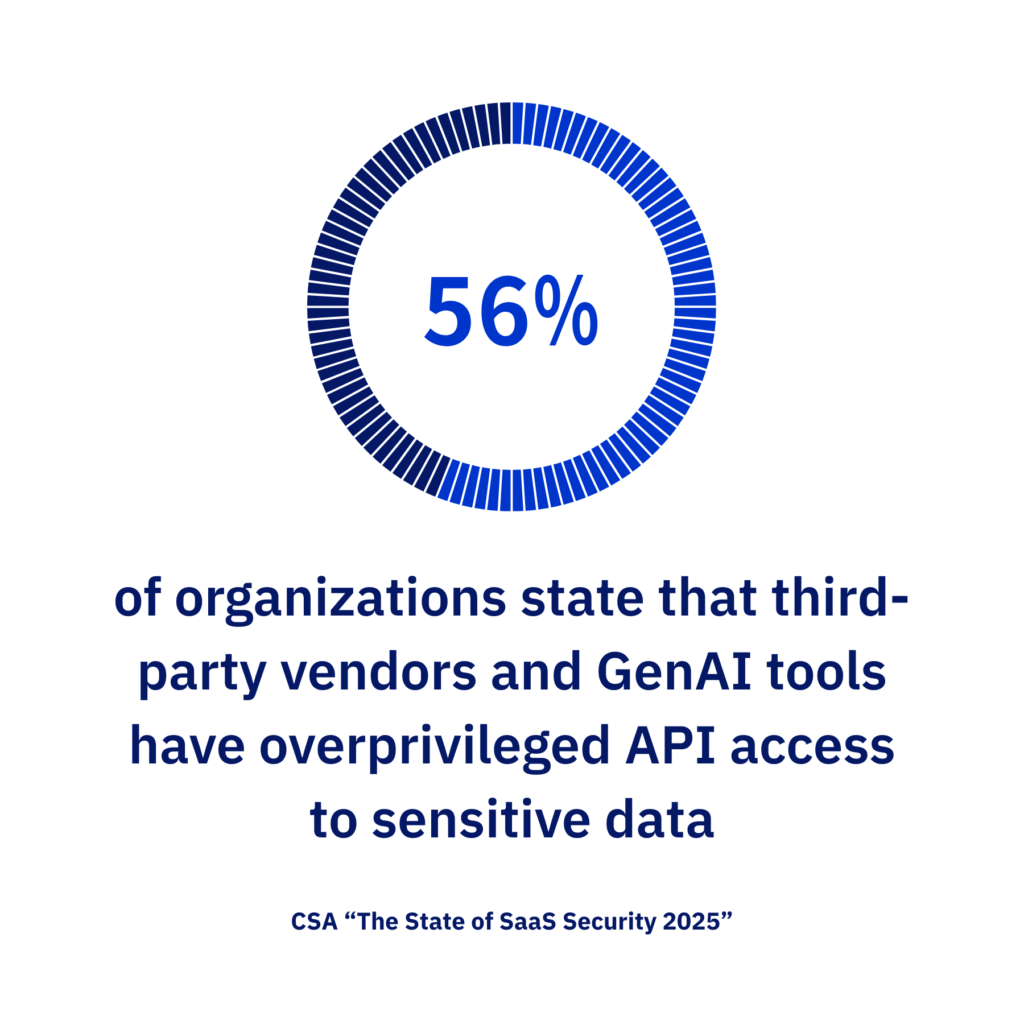
Even when organizations secure SaaS platforms, many make the mistake of overlooking the broader ecosystem. SaaS tools are typically hubs that connect to dozens, or even hundreds, of other tools through APIs, OAuth tokens, browser extensions, data pipelines, automation platforms, and partner integrations. And every one of those connections represents a trust relationship. According to The State of SaaS Security 2025, a report by the Cloud Security Alliance (CSA), 46% of organizations cite the monitoring of non-human identities as the greatest SaaS security risk, and 56% of organizations report that third-party vendors and GenAI tools have overprivileged API access to sensitive data.

Integrations introduce risk because they:
- Extend sensitive data beyond the boundaries of the core app (Once it’s beyond the organization’s control, risk compounds).
- Create persistent access pathways that rarely undergo security review (Also known as highly exploitable security gaps).
- Operate outside traditional monitoring and logging (Giving threat actors the perfect screen to pass through unnoticed).
OAuth tokens, for example, often carry broad read/write permissions. They don’t appear in SIEM logs, they don’t require user credentials, and they often persist until manually revoked. That means an unused automation tool, an abandoned browser extension, or a retired vendor system may still have access to live production data.
This has given rise to “shadow integrations.” These are the third-party connections added quietly by power users, never inventoried, and rarely reviewed for risk or compliance. They can remain active long after they are needed. Attackers have learned to target these connections because compromising them is easier than compromising the SaaS platform itself.
In other words, attackers don’t need to break in. They just connect.
The Visibility Gap: Why Traditional Security Models Fall Short
Another challenge in SaaS security today is the absence of visibility. And not just into the applications themselves, but into the sprawling integration layer that surrounds them. Traditional security models were built for environments with clear perimeter boundaries, predictable system ownership, and well-defined change windows. SaaS breaks those assumptions.
SaaS ecosystems behave very differently from traditional IT. They are:
- Decentralized: End users and line-of-business teams routinely authorize new integrations without security involvement, creating hundreds of untracked trust relationships.
- Dynamic: Application settings, role structures, and permission scopes change frequently, and in some platforms, automatically, as vendors release new features or update defaults.
- Distributed: Data moves across dozens of interconnected apps, APIs, and automation tools. There is no single gateway or log source that provides a complete picture of activity.
This opacity makes it exceedingly difficult for security teams to answer questions that should be foundational to risk management:
- Who has access to what data, where did those entitlements come from, and are they valid each time the user requests access?
- What integrations and OAuth tokens are active across core platforms today?
- Which configuration changes have occurred across SaaS environments this week, and why?
- Where is sensitive information flowing once it leaves the primary application?
The problem only compounds at scale. Large organizations may rely on hundreds of SaaS tools, each with its own permission models, data ownership, logging behaviors, and visibility limitations. Even “simple” applications can host dozens of third-party extensions, connectors, and workflow automations that operate silently in the background. These elements rarely feed into SIEMs, asset inventories, or identity governance systems. As a result, entire categories of activity remain effectively invisible to security controls designed for more static environments.
This gap is precisely where modern attackers are focusing.
Adversaries no longer need to rely primarily on compromised user accounts or exploiting application vulnerabilities. Instead, they target misaligned permissions, over-scoped tokens, forgotten integrations, and configuration drift. As discussed, these are the weak areas where organizations have little to no monitoring. A single over-permissioned automation tool or an abandoned integration can provide access to production data without triggering a single alert.
The industry often responds by adding more tools, yet visibility is not a tooling deficit. It is a fundamental governance, process, and operational challenge. Without dedicated oversight of configuration baselines, integration inventories, access scopes, and data flows, even the most advanced security stack will struggle to detect issues that arise from within the SaaS ecosystem itself.
Gain Control Over SaaS Security
If you feel like your SaaS attack surface is expanding faster than you can keep up, contact GuidePoint Security. We help organizations establish SaaS Security Security Programs by helping them gain visibility, securing the integration layer, and stopping misconfigurations before they become invisible entry points for threat actors.
如有侵权请联系:admin#unsafe.sh