嗯,用户让我用中文帮他总结一下这篇文章,控制在一百个字以内,而且不需要以“文章内容总结”或“这篇文章”这样的开头,直接写描述。好的,我先看看这篇文章讲的是什么。 文章标题是“BGP Activity as an Enabling or Supporting Effect in Venezuela Power-Grid Disruption”,也就是关于BGP活动在委内瑞拉电网中断中的作用。看起来是分析BGP路由泄露是否导致了停电。 执行摘要里提到,委内瑞拉主要电信提供商CANTV的BGP路由泄露异常与基础设施中断时间接近。虽然BGP操作本身不能直接导致停电,但可能加剧了通信问题,影响了应对危机的能力。 确认观察部分指出,Cloudflare Radar检测到CANTV的路由泄露异常,涉及特定IP地址段,这些地址与关键基础设施相关。分析判断认为BGP活动没有直接导致停电,但可能恶化了通信。 假设部分讨论了可能是意外、通信降级、情报准备、干扰活动或综合多领域攻击。结论是BGP不稳定是压力倍增器而非根本原因,但是否故意仍不确定。 所以总结起来:文章分析委内瑞拉停电期间的BGP异常,指出这些异常可能加剧通信问题,并探讨是否为故意行为。结论是BGP可能作为助力因素,但非根本原因。 </think> 文章分析了委内瑞拉电网中断期间的BGP路由泄露异常现象及其潜在影响。观察表明,路由不稳定可能加剧了通信中断,但无法确定是否为故意行为。结论指出BGP活动可能作为压力倍增器而非根本原因。 2026-1-8 11:21:23 Author: krypt3ia.wordpress.com(查看原文) 阅读量:1 收藏
Analytic Note
Subject: BGP Activity as an Enabling or Supporting Effect in Venezuela Power-Grid Disruption
Classification: UNCLASSIFIED / OSINT
Date: January 2026
Analytic Confidence: Moderate (infrastructure telemetry is strong; intent attribution remains low confidence)
Executive Summary
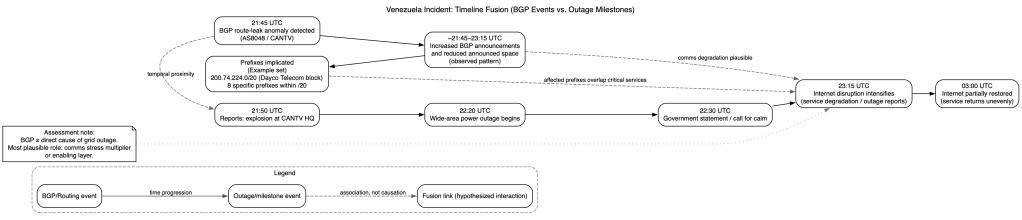
Observed BGP route-leak anomalies involving Venezuela’s primary telecom provider (CANTV, AS8048) occurred in temporal proximity to major infrastructure disruptions. While BGP manipulation alone cannot directly disable electrical generation or transmission, available evidence supports the assessment that routing instability plausibly functioned as an enabling or compounding effect, degrading communications, situational awareness, or coordination during a broader crisis.
At present, no conclusive evidence proves deliberate offensive use of BGP. However, the structure, scope, and timing of the anomalies justify continued investigation into whether routing manipulation was used intentionally as part of a multi-domain effects operation, rather than being a purely accidental misconfiguration.
Confirmed Observations (High Confidence)

- Cloudflare Radar and routing telemetry identified route-leak anomalies involving AS8048 (CANTV), with atypical AS-path behavior and announcements routed through external transit providers.
- A constrained prefix set was affected, notably eight prefixes within 200.74.224.0/20, registered to Dayco Telecom (Caracas).
- During the anomaly window, telemetry showed:
- A spike in BGP announcements, and
- A reduction in announced IP address space, consistent with partial withdrawal or instability.
- The affected address space overlaps with telecom, financial, ISP, and messaging infrastructure, which are operationally critical during power-grid incidents.
These observations establish routing instability, not intent.
Analytic Judgments
Judgment 1
BGP activity did not directly cause the Venezuelan power outage.
Confidence: High
Power-grid failures require physical, OT, or control-system disruptions. Internet routing manipulation alone cannot trip generators, destroy transformers, or collapse transmission networks.
Judgment 2
BGP instability likely degraded communications during the crisis.
Confidence: Moderate–High
Telecom networks underpin grid operations, emergency coordination, outage management, and restoration logistics. Partial reachability loss or routing asymmetry affecting Caracas-based infrastructure would materially hinder response efforts.
Judgment 3
The constrained and clustered nature of affected prefixes is atypical for random global BGP noise.
Confidence: Moderate
While accidental route leaks are common, tight geographic and organizational clustering raises the probability that the impact was selective, even if the trigger was misconfiguration rather than hostile intent.
Judgment 4
Deliberate BGP manipulation as part of a layered effects operation is plausible but unproven.
Confidence: Low–Moderate
Public statements referencing “layering different effects” conceptually align with BGP being used as a communications-shaping or intelligence-support layer, but no direct evidence ties the routing event to an offensive command decision.
Hypotheses (Not Mutually Exclusive)
H1 — Accidental Route Leak Under Crisis Conditions
Assessment:
A benign policy error or misconfiguration within AS8048 or a peer caused a route leak that coincided with broader instability.
Indicators Supporting H1
- Route leaks are globally frequent.
- No sustained interception or long-duration rerouting observed.
- Rapid normalization would favor this explanation.
H2 — Communications Degradation as a Shaping Effect
Assessment:
Routing instability—intentional or not—selectively impaired key Caracas networks, slowing coordination and situational awareness during the outage.
Indicators Supporting H2
- Tight prefix clustering.
- Impact on telecom-adjacent and institutional services.
- Observable reduction in announced IP space.
H3 — BGP-Enabled Intelligence Preparation or Traffic Observation
Assessment:
Short-lived routing anomalies were used to observe or map critical communications paths during a crisis window.
Indicators Supporting H3
- Unusual AS-path prepending behavior.
- Transit through major international carriers.
- Would likely be brief to avoid detection.
Key Caveat: No public evidence of TLS interception, credential compromise, or persistent MITM currently supports this hypothesis.
H4 Deliberate Noise or Decoy Activity
Assessment:
Routing anomalies functioned primarily as analytic distraction, drawing attention away from physical sabotage, OT compromise, or telecom infrastructure failure.
Indicators Supporting H4
- High visibility, low explanatory power.
- Lack of follow-on routing exploitation.
H5 Integrated Multi-Domain Effects
Assessment:
BGP activity was one component in a broader set of cyber, informational, telecom, or physical actions designed to constrain response options.
Indicators Supporting H5
- Alignment with known “effects-layering” doctrines.
- Requires corroboration from non-BGP domains (satcom, cellular core, OT logs).
Collection Gaps
To advance confidence, the following gaps must be addressed:
- Prefix-level reachability measurements from multiple global vantage points during the incident window.
- NetFlow / path data showing whether traffic was merely dropped or actually transited alternate AS paths.
- TLS / certificate telemetry indicating possible interception.
- Utility and telecom incident logs correlating comms loss with operational decision points.
- Historical baseline behavior for AS8048, including normal prepending patterns and peer relationships.
Priority Intelligence Requirements (PIRs)
- Did any utility, telecom, or government operator credentials show anomalous access during or immediately after the routing event?
- Were outage restoration timelines measurably delayed due to loss of IP-based communications?
- Did the affected prefixes host operator-facing services (VPNs, NOCs, dispatch systems) rather than public-facing content?
- Are similar BGP anomalies observable before or during other infrastructure crises in the region?
Bottom Line
The most defensible analytic position is that BGP instability acted as a stress/force multiplier, not a root cause. Whether that instability was accidental, opportunistic, or deliberately induced remains unresolved. However, the event demonstrates that internet routing is a viable enabling layer in modern infrastructure disruption scenarios, particularly when telecom resilience is weak and crisis coordination depends heavily on IP networks.
如有侵权请联系:admin#unsafe.sh