
好的,我现在需要帮用户总结这篇文章的内容,控制在100字以内。首先,我得仔细阅读文章,抓住关键点。 文章主要讲的是一个新的恶意软件GoBruteforcer攻击加密货币和区块链项目的数据库。这个恶意软件基于Golang,通常攻击暴露的FTP、MySQL等服务。它利用被黑的Linux服务器进行随机IP扫描和暴力破解攻击。 Check Point的研究人员估计有超过5万的服务器可能被攻击。攻击者通过XAMPP的FTP服务器获取初始访问权限,因为配置中常使用弱密码。一旦进入,他们会上传网络壳,继续感染链,下载IRC机器人和暴力破解模块。 恶意软件在延迟后启动多个线程,扫描随机IP,避开特定网络。密码列表是硬编码的22对用户名密码,常见于XAMPP等配置中。 最近的攻击利用了AI生成的配置示例导致弱默认用户名和密码。建议管理员避免使用AI生成指南,使用强密码,并检查暴露服务,替换旧软件栈。 总结时要涵盖恶意软件的目标、攻击方式、感染链、AI配置的影响以及防御建议。控制在100字以内,直接描述内容。 </think> 一种名为GoBruteforcer的恶意软件正针对暴露服务器上的加密货币和区块链项目数据库发起攻击。该恶意软件基于Golang语言开发,主要通过暴力破解手段攻击暴露的FTP、MySQL、PostgreSQL和phpMyAdmin服务。研究人员发现超过5万台互联网暴露服务器可能易受此类攻击影响。攻击者通常利用弱默认密码或AI生成配置中的漏洞进入系统,并上传网络壳进行进一步感染。建议管理员避免使用AI生成部署指南,并加强服务安全配置以防范此类威胁。 2026-1-7 23:30:26 Author: www.bleepingcomputer.com(查看原文) 阅读量:5 收藏
A new wave of GoBruteforcer botnet malware attacks is targeting databases of cryptocurrency and blockchain projects on exposed servers believed to be configured using AI-generated examples.
GoBrutforcer is also known as GoBrut. It is a Golang-based botnet that typically targets exposed FTP, MySQL, PostgreSQL, and phpMyAdmin services.
The malware often relies on compromised Linux servers to scan random public IPs and carry out brute-force login attacks.
Preying on weak defenses
Check Point researchers estimate that there are more than 50,000 internet-facing servers that may be vulnerable to the GoBrut attacks.
They say that initial compromise is often obtained through the FTP servers on servers running XAMPP because many times the configuration has a weak default password, unless the administrator goes through the security configuration.
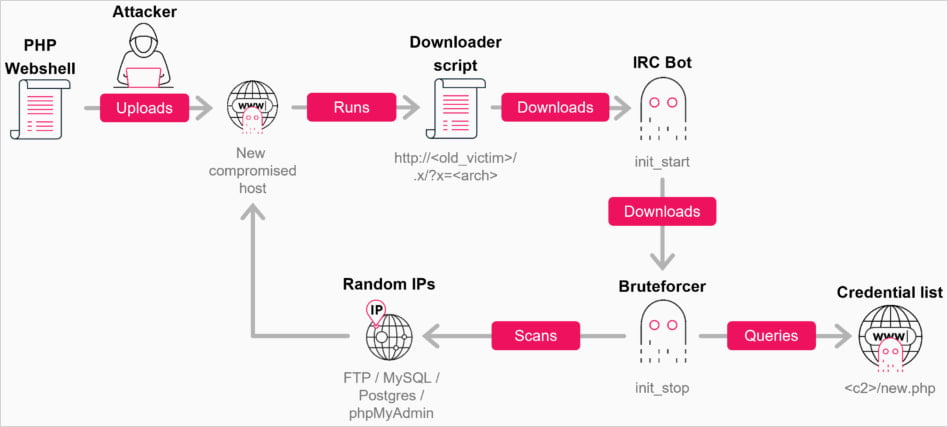
"When attackers obtain access to XAMPP FTP using a standard account (commonly daemon or nobody) and a weak default password, the typical next step is to upload a web shell into the webroot," Check Point
The attacker may upload the web shell through other means, such as a misconfigured MySQL server or phpMyAdmin panel. The infection chain continues with a downloader, fetching an IRC bot, and the bruteforcer module.
The malware activity starts after a 10-400-second delay, launching up to 95 brute-forcing threads on x86_64 architectures, scanning random public IP ranges, while skipping private networks, AWS cloud ranges, and U.S. government networks.
Each worker generates a single random public IPv4 address, probes the relevant service port, goes through the supplied credential list, and then exits. New workers are spawned continuously to maintain the set concurrency level.
The FTP module relies on a hardcoded list of 22 username-password pairs embedded directly in the binary. These credentials map closely to default or commonly deployed accounts in web-hosting stacks such as XAMPP.
Source: Check Point
Check Point says that in recent campaigns, GoBruteforcer activity is fueled by the reuse of common server configuration snippets generated by large language models (LLMs), which leads to a proliferation of weak, predictable default usernames, such as appuser, myuser, and operator.
These usernames frequently appear in AI-generated Docker and DevOps instructions, leading the researchers to believe that the configurations were added to real-world systems, thus making them vulnerable to password-spraying attacks.
The second trend fueling the botnet’s recent campaign is outdated server stacks like XAMPP that continue to ship with default credentials and open FTP services. These deployments expose vulnerable webroot directories, enabling attackers to drop web shells.
Check Point's report highlights a campaign where a compromised host was infected with TRON wallet-scanning tools that perform sweeps across TRON and Binance Smart Chain (BSC). The attackers used a file containing approximately 23,000 TRON addresses, targeting them with automated utilities to identify and drain wallets with non-zero balances.
Admins defending against GoBruteforcer should avoid using AI-generated deployment guides and rely on non-default usernames with strong, unique passwords.
It is also recommended to check FTP, phpMyAdmin, MySQL, and PostgreSQL for exposed services, and replace outdated software stacks like XAMPP with more secure alternatives.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you're cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
如有侵权请联系:admin#unsafe.sh

