好的,我现在需要帮用户总结一篇文章的内容,控制在100字以内。首先,我得仔细阅读文章,抓住关键点。 文章主要讲的是n8n平台的一个严重漏洞,叫做Ni8mare,CVE编号是CVE-2026-21858,CVSS评分10.0。这个漏洞允许未经认证的攻击者完全接管受影响的实例。漏洞影响了所有版本到1.65.0的n8n,已经在1.121.0版本中修复。 漏洞的原因是n8n处理Webhooks上传数据的方式。当请求不是multipart/form-data时,攻击者可以构造req.body.files,导致文件路径被控制,进而读取任意文件。更严重的是,这可能导致远程代码执行。 总结时要包括:漏洞名称、CVE编号、CVSS评分、影响范围、漏洞原因、攻击后果以及修复版本。同时要简洁明了,不超过100字。 现在组织语言:先点出漏洞名称和评分,然后说明影响范围和攻击后果,最后提到修复版本。 </think> Ni8mare(CVE-2026-21858)是n8n平台的一个严重漏洞(CVSS 10.0),允许未经认证的攻击者完全接管受影响实例。该漏洞源于Webhooks处理文件上传时未验证Content-Type头信息,导致攻击者可构造恶意请求读取任意文件或执行远程代码。此漏洞影响所有版本至1.65.0的n8n,并于2025年11月通过升级至1.121.0修复。 2026-1-7 21:15:1 Author: securityaffairs.com(查看原文) 阅读量:5 收藏
Ni8mare flaw gives unauthenticated control of n8n instances

A critical n8n flaw (CVE-2026-21858, CVSS 10.0), dubbed Ni8mare, allows unauthenticated attackers to fully take over vulnerable instances.
Researchers uncovered a maximum severity n8n vulnerability, tracked as CVE-2026-21858 (CVSS score of 10.0). The flaw, dubbed Ni8mare by Cyera researchers who discovered the vulnerability, lets unauthenticated attackers fully compromise affected instances.
n8n is a workflow automation platform designed for technical teams that combines the flexibility of custom code with the speed and simplicity of no-code tools. It supports more than 400 integrations, includes native AI features, and uses a fair-code license, allowing organizations to build powerful automations while retaining full control over their data and deployment environments.
The flaw in n8n workflows can let unauthenticated attackers access server files, exposing sensitive data and potentially leading to further system compromise.
“A vulnerability in n8n allows an attacker to access files on the underlying server through execution of certain form-based workflows. A vulnerable workflow could grant access to an unauthenticated remote attacker. This could result in exposure of sensitive information stored on the system and may enable further compromise depending on deployment configuration and workflow usage.” reads the advisory.
The vulnerability affects all versions of n8n prior to and including 1.65.0, and it was fixed in n8n version 1.121.0 in November 2025.
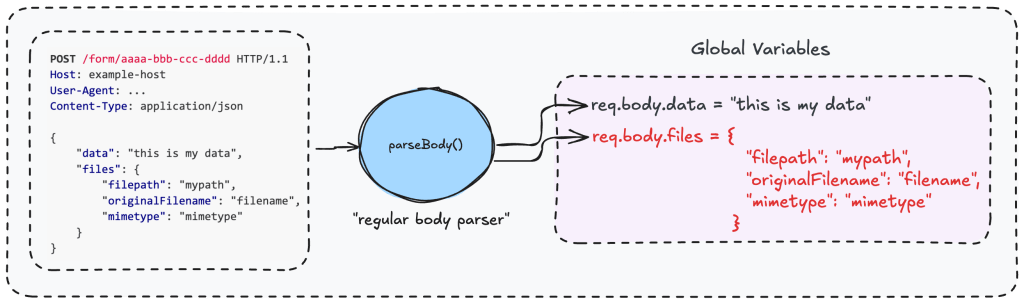
The issue stems from how n8n Webhooks handle uploaded data. Webhooks start workflows and parse incoming requests based on the Content-Type header. If the request is multipart/form-data, n8n uses a file upload parser (Formidable) that safely stores uploaded files in temporary locations and populates req.body.files. For other content types, a regular parser is used, which directly fills req.body with user-supplied data.
The vulnerability arises because some file-handling workflows do not verify the Content-Type before processing files. In the Form Webhook node, a file-handling function is called without checking that the request is actually multipart/form-data. This allows an attacker to send a request with a different Content-Type (e.g., JSON) and manually define req.body.files.

By doing this, the attacker can control file paths used by the workflow and trick n8n into copying any local system file instead of a legitimate upload. These files can then be processed by downstream nodes and exposed, for example through a chat or knowledge-base workflow.
In practice, this enables arbitrary file read attacks, such as retrieving /etc/passwd, potentially exposing sensitive system data and enabling further compromise.
The vulnerability enables escalation from arbitrary file read to full RCE in n8n. n8n stores auth sessions in an n8n-auth cookie, built from user data (ID, partial password hash) and signed with a local secret key. With arbitrary file read, an attacker can extract the local SQLite database (containing user records) and the config file holding the signing secret. Using these, they can forge a valid admin session cookie and bypass authentication. Once logged in as admin, the attacker can create a workflow using the “Execute Command” node, achieving remote code execution on the n8n instance.
“The blast radius of a compromised n8n is massive.” concludes the report. “A compromised n8n instance doesn’t just mean losing one system – it means handing attackers the keys to everything. API credentials, OAuth tokens, database connections, cloud storage – all centralized in one place. n8n becomes a single point of failure and a goldmine for threat actors.”
In December, researchers warned that another critical vulnerability, tracked as CVE-2025-68613 (CVSS score of 9.9), in the n8n workflow automation platform could allow attackers to achieve arbitrary code execution under certain circumstances.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, CVE-2026-21858)
如有侵权请联系:admin#unsafe.sh