嗯,用户让我帮忙总结一篇文章的内容,控制在100字以内,而且不需要特定的开头。首先,我需要仔细阅读文章,抓住主要信息。 文章讲的是一个名为PHALT#BLYX的网络攻击活动,目标是欧洲的酒店业。攻击者使用了伪造的Booking.com邮件和BSoD(蓝屏错误)诱饵,诱骗员工执行恶意命令,最终安装DCRat远程访问木马。 我需要把这些关键点浓缩到100字以内。首先确定攻击者是谁,目标是什么,使用的手段和最终目的。然后用简洁的语言把这些信息连贯起来。 可能会遇到的问题是如何在有限的字数内涵盖所有重要信息而不遗漏关键点。可能需要合并一些细节,比如提到“恶意PowerShell命令”和“DCRat木马”,同时说明攻击的影响。 最后检查一下是否符合用户的要求:中文总结,100字以内,直接描述内容。确保没有使用“这篇文章”或“文章内容总结”这样的开头。 </think> 网络攻击活动PHALT#BLYX针对欧洲酒店业,利用伪造的Booking.com邮件和蓝屏错误诱饵诱导员工执行恶意PowerShell命令,最终部署DCRat远程访问木马以实现系统控制和持久化。 2026-1-7 07:31:1 Author: securityaffairs.com(查看原文) 阅读量:16 收藏
Fake Booking.com lures and BSoD scams spread DCRat in European hospitality sector

PHALT#BLYX targets European hotels with fake Booking emails and BSoD lures, tricking staff into installing the DCRat remote access trojan.
Researchers uncovered a late-December 2025 campaign, dubbed PHALT#BLYX, targeting European hotels with fake Booking-themed emails.
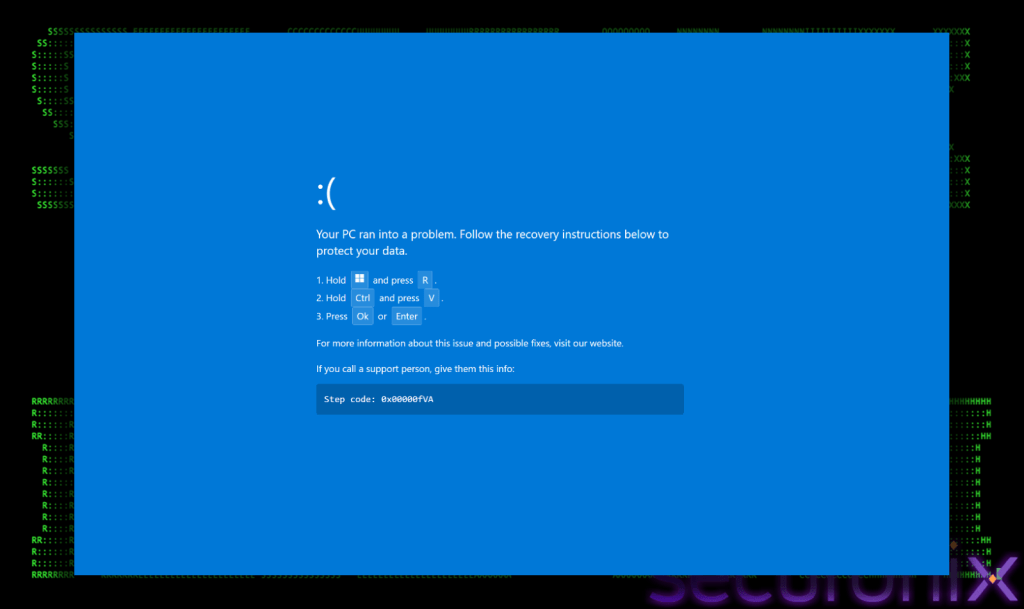
Victims are redirected to bogus BSoD pages using ClickFix-style lures that prompt them to apply “fixes.” The multi-stage attack ultimately installs the DCRat remote access trojan, enabling full remote control of infected systems, according to Securonix.
“An ongoing malware campaign tracked as PHALT#BLYX has been identified as a multi-stage infection chain that begins with the click-fix and fake captcha social engineering tactic and deploys a customized DCRat payload.” reads the report published by Securonix. “For initial access, the threat actors utilize a fake booking.com reservation cancellation lure to trick victims into executing malicious PowerShell commands, which silently fetch and execute remote code. This happens via multi-stages involving powershell, proj files and msbuild.”
The PHALT#BLYX campaign targets European hospitality firms using phishing emails themed as Booking.com.
Victims are lured to fake websites with CAPTCHA prompts that trigger a fake Blue Screen of Death (BSoD), tricking users into running malicious PowerShell commands (“ClickFix”).
“The email alerts the recipient to a “Reservation Cancellation” and prominently displays a significant financial charge (e.g., €1,004.38). This high-value charge creates a sense of urgency and panic, compelling the victim to investigate immediately.” continues the report. “Once they click the “See Details” button to verify the charge. The link does not lead to Booking.com. Instead, it routes the user through an intermediate redirector (`oncameraworkout[.com/ksbo`) before landing on the malicious domain `low-house[.com`.”
This downloads an MSBuild project file, compiled via MSBuild.exe to deploy a heavily obfuscated DCRat payload. DCRat enables remote access, keylogging, process hollowing, persistence, and secondary payload delivery. The campaign evolved from earlier, easier-to-detect HTA-based delivery to stealthier “living off the land” techniques using MSBuild. Emails reference euro-denominated bookings, and Russian-language artifacts link the activity to Russian-speaking threat actors.
Attackers use an XML-based MSBuild project file (v.proj) to abuse a trusted Windows tool, proxying execution and running an embedded PowerShell script.
In the final stage of the attack, the malware deploys DCRat through a packed .NET loader named staxs.exe. The loader decrypts its embedded configuration using strong encryption based on AES‑256 and PBKDF2. To survive reboots, it establishes persistence by creating a deceptive Internet Shortcut (.url) file in the Windows Startup folder. Once active, the malware connects to one of several command‑and‑control domains and begins profiling the infected system, collecting details about the user and environment. To evade detection, it injects its payload into legitimate Windows processes using process hollowing, allowing the attacker to maintain stealthy and long‑term remote control of the compromised machine.
“The PHALT#BLYX campaign represents a sophisticated evolution in commodity malware delivery, seamlessly blending high-pressure social engineering with advanced “Living off the Land” techniques The psychological manipulation, combined with the abuse of trusted system binaries like `MSBuild.exe`, allows the infection to establish a foothold deep within the victim’s system before traditional defenses can react.” concluders the report. “The technical complexity of the infection chain reveals a clear intent to evade detection and maintain long-term persistence.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, PHALT#BLYX)
如有侵权请联系:admin#unsafe.sh

