好的,我现在需要帮用户总结一篇文章的内容,控制在100字以内。首先,我得仔细阅读文章,抓住主要信息。 文章讲的是Kimwolf僵尸网络,它是Aisuru恶意软件的安卓变种,已经感染了超过200万台设备。主要通过利用家庭代理网络的漏洞来攻击内部网络设备。目标通常是安卓电视盒子和流媒体设备,因为它们暴露了ADB服务。 研究人员注意到自去年8月以来活动增加,最近一个月更是加强了对代理网络的扫描。感染的设备被用于DDoS攻击、代理转售和通过第三方SDK获利。最大的DDoS攻击达到了29.7 Tbps。 感染主要集中在越南、巴西、印度和沙特阿拉伯。大部分设备在购买前就被代理SDK感染了。Kimwolf的增长得益于滥用住宅代理网络,直接与内部网络设备交互。 文章还提到Synthient公司开发了一个在线扫描工具,并建议用户避免低价安卓电视盒子,选择经过认证的设备。 总结的时候要涵盖这些关键点:僵尸网络规模、传播方式、目标设备、用途、地理位置、增长原因以及防护建议。确保在100字以内简洁明了地表达出来。 </think> Kimwolf僵尸网络作为Aisuru恶意软件的安卓变种,已感染超200万台设备,主要通过家庭代理网络漏洞攻击内部安卓设备。其利用暴露的ADB服务感染电视盒子等设备,并用于DDoS攻击和牟利。感染集中在越南等国,多数设备因预装代理SDK而易受攻击。 2026-1-6 19:15:18 Author: www.bleepingcomputer.com(查看原文) 阅读量:3 收藏
The Kimwolf botnet, an Android variant of the Aisuru malware, has grown to more than two million hosts, most of them infected by exploiting vulnerabilities in residential proxy networks to target devices on internal networks.
Researchers observed increased activity for the malware since last August. Over the past month, Kimwolf has intensified its scanning of proxy networks, searching for devices with exposed Android Debug Bridge (ADB) services.
Common targets are Android-based TV boxes and streaming devices that allow unauthenticated access over ADB. Compromised devices are primarily used in distributed denial-of-service (DDoS) attacks, proxy resale, and monetizing app installations via third-party SDKs like Plainproxies Byteconnect.
The Aisuru botnet is currently responsible for the largest DDoS attack publicly disclosed, which peaked at 29.7 terabits per second as measured by Cloudflare.
A report from XLab notes that the Kimwolf Android botnet had more than 1.8 million compromised devices on December 4.
Researchers at threat intelligence and anti-fraud cybersecurity company Synthient have been tracking Kimwolf activity. They say that the number of compromised devices has climbed to nearly two million, and produced around 12 million unique IP addresses each week.
Most of the infected Android devices are in Vietnam, Brazil, India, and Saudi Arabia. In many cases, the systems were compromised by proxy SDKs before purchase, which was reported in the past.
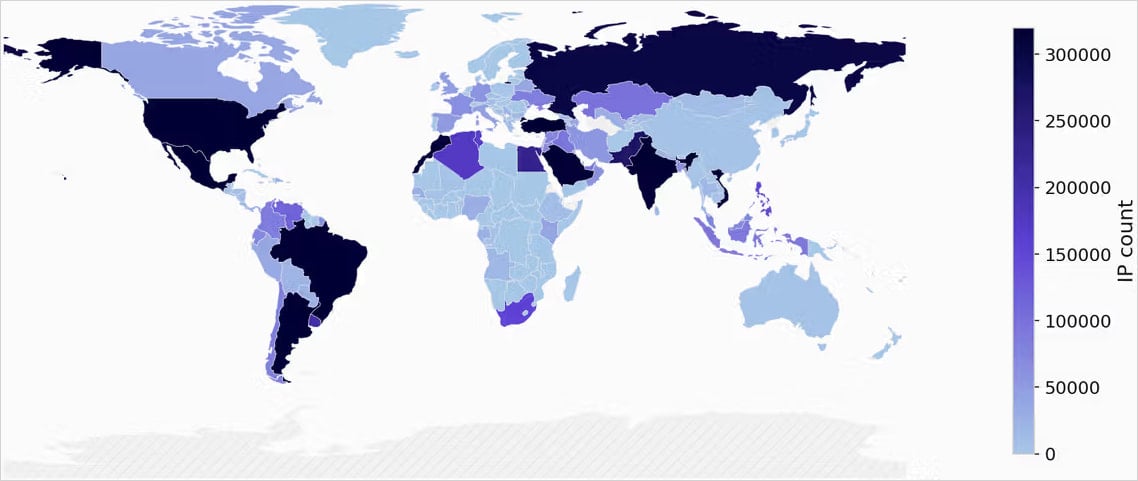
Source: Synthient
Abusing residential proxies
According to Synthient, Kimwolf’s rapid growth is largely due to its abuse of residential proxy networks to reach vulnerable Android devices. Specifically, the malware takes advantage of proxy providers that permit access to local network addresses and ports, allowing direct interaction with devices running on the same internal network as the proxy client.
Starting on November 12, 2025, Synthient observed elevated activity scanning for unauthenticated ADB services exposed through proxy endpoints, targeting ports 5555, 5858, 12108, and 3222.
The Android Debug Bridge (ADB) is a development and debugging interface that allows installing and removing apps, running shell commands, transferring files, and debugging Android devices. When exposed over a network, ADB can allow unauthorized remote connections to modify or take control of Android devices.
When reachable, botnet payloads were delivered via netcat or telnet, piping shell scripts directly into the exposed device for local execution, written to /data/local/tmp.
Synthient captured multiple payload variants throughout December, but the delivery methods remained unchanged.
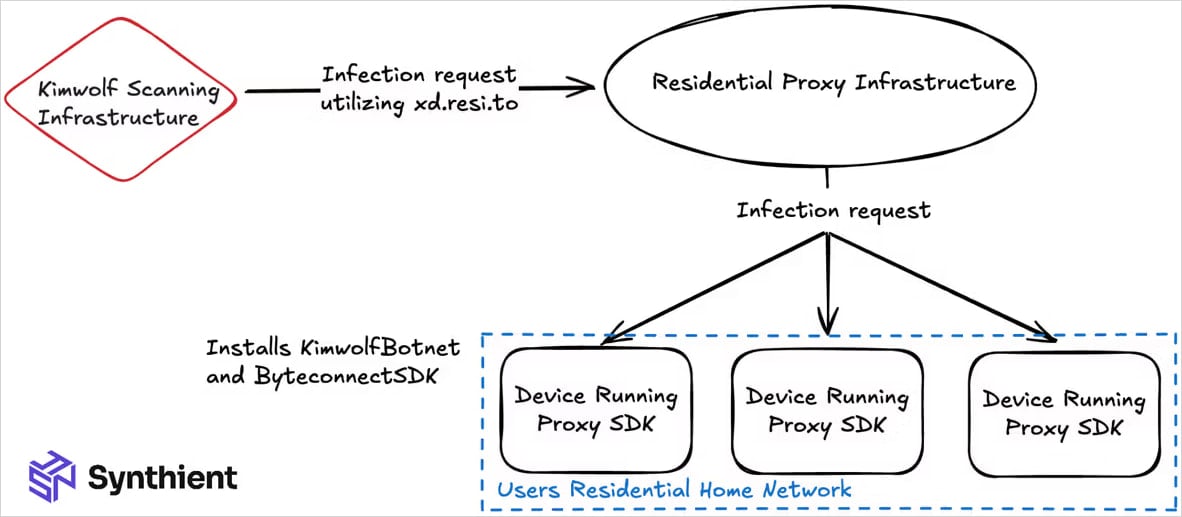
Source: Synthient
The researchers found high exposure rates in one sample residential proxy pool, underscoring that such devices can be exploited within minutes of joining these networks.
"Upon analyzing exposed devices part of IPIDEAs proxy pool, we found that 67% of all Android devices are unauthenticated, leaving them vulnerable to remote code execution," Synthient explains.
"From our scans, we found approximately 6 million vulnerable IPs […] These devices are often shipped pre-infected with SDKs from proxy providers," the researchers say.
IPIDEA, one of the impacted proxy providers and a top Kimwolf target because it enabled access to all ports, responded to Synthient’s alert on December 28 by blocking access to local networks and a broad range of ports.
In total, the researchers sent almost a dozen vulnerability reports "to the top proxy providers" observed in Kimwolf activity. However, researchers cannot confidently determine all the proxy providers targeted by the malware.
Protecting against Kimwolf
Synthient has published an online scanner tool to help users identify if any of their network devices are part of the Kimwolf botnet.
In the case of a positive result, the researchers suggest that infected TV boxes should be "wiped or destroyed," otherwise the botnet will persist.
The general recommendation is to avoid low-cost generic Android TV boxes and to prefer ‘Google Play Protect certified’ devices from reputable OEMs, such as Google’s Chromecast, NVIDIA Shield TV, and Xiaomi Mi TV Box.
7 Security Best Practices for MCP
As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
如有侵权请联系:admin#unsafe.sh

