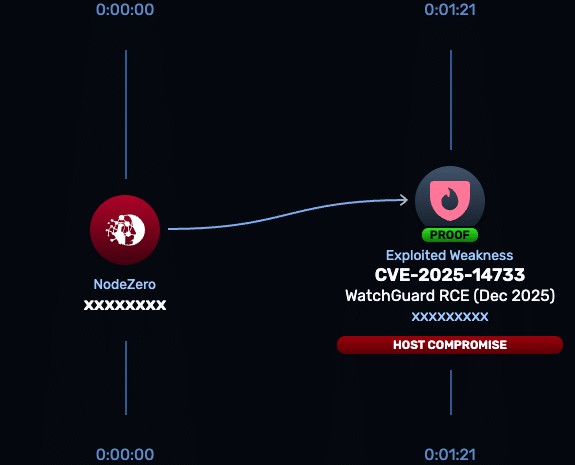
CVE-2025-14733 是 WatchGuard Fireware OS 中的一个严重越界写入漏洞,影响 IKEv2 VPN 服务。远程未认证攻击者可借此执行任意代码。该漏洞已被证实被活跃利用,并加入 CISA 目录。建议立即升级至修复版本并采取加固措施以缓解风险。 2026-1-5 21:31:44 Author: horizon3.ai(查看原文) 阅读量:21 收藏
CVE-2025-14733 is a critical out-of-bounds write vulnerability in the iked process of WatchGuard Fireware OS affecting IKEv2 VPN services, including Mobile User VPN and Branch Office VPN. A remote, unauthenticated attacker can exploit this flaw to execute arbitrary code on affected Firebox appliances. Active exploitation in the wild has been confirmed, and the vulnerability has been added to the CISA Known Exploited Vulnerabilities Catalog.
What it is and why it matters
The vulnerability exists in how Fireware OS processes certain IKEv2 handshake messages within the iked daemon. Specially crafted IKE_AUTH requests can trigger an out-of-bounds write, resulting in remote code execution without authentication.
According to WatchGuard, exploitation attempts via the vulnerability on Firebox devices appear to be part of a broader threat actor campaign targeting edge networking equipment and exposed infrastructure from WatchGuard and other vendors. Because Firebox appliances commonly function as perimeter firewalls and VPN gateways, successful exploitation can result in full device compromise, traffic interception, credential exposure, and downstream access into internal networks.
Stop Guessing, Start Proving
Quick actions — do these now
Run the Rapid Response test
Assess internet-facing Firebox appliances to determine whether the IKEv2 VPN service is exploitable via CVE-2025-14733.
Patch immediately
Upgrade Fireware OS to a fixed version released by WatchGuard. CVE-2025-14733 is actively exploited in the wild, and there is no effective mitigation short of patching. Firebox devices running end-of-life Fireware versions do not receive fixes and should be considered compromised until replaced or removed from exposure.
Harden VPN exposure and rotate secrets
After patching, review IKEv2 VPN configurations to reduce exposure. Disable unused Mobile User VPN and Branch Office VPN services, restrict IKEv2 access where possible, and rotate credentials or certificates used for VPN authentication. If exploitation is suspected, treat the appliance as fully compromised and assume VPN secrets may have been exposed.
NodeZero® Offensive Security Platform — Rapid Response
The WatchGuard Fireware OS Rapid Response test (CVE-2025-14733) enables customers to safely verify whether Firebox appliances running vulnerable Fireware OS versions are exploitable via the IKEv2 out-of-bounds write flaw, and to confirm that patching eliminates exploitability risk.
Run the Rapid Response test
Run the WatchGuard Fireware OS — CVE-2025-14733 Rapid Response test from the customer portal to assess internet-facing Firebox appliances for unauthenticated exploitation of the IKEv2 VPN service.
Patch immediately
Apply WatchGuard’s fixed Fireware OS releases. WatchGuard also recommends rotating locally stored secrets on affected devices.
Re-run the Rapid Response test
After patching and hardening, re-run the Rapid Response test to confirm the IKEv2 attack path is no longer exploitable.
If your Firebox device is only configured with Branch Office VPN tunnels to static gateway peers and you are not able to immediately patch, follow WatchGuard’s recommendations for Secure Access to Branch Office VPNs that Use IPSec and IKEv2 as a temporary mitigation.
Indicators of Compromise
- IKE_AUTH log entries containing unusually large or malformed CERT payloads
- Unexpected crashes, restarts, or hangs of the
ikedprocess. Note: Process hang is a strong indicator, while crashes are a weak indicator of attack. - VPN negotiation attempts from unfamiliar external IP addresses
- Unexplained configuration changes or VPN session behavior following IKE traffic
Always correlate indicators with local logs and telemetry before concluding compromise.
Affected versions & patch
Affected:
- Fireware OS 2025.1 through 2025.1.3
- Fireware OS 12.x through 12.11.5
- Fireware OS 12.5.x (T15 and T35 models) through 12.5.14
- Fireware OS 11.x (end of life)
Patched:
- Fireware OS 2025.1.4
- Fireware OS 12.11.6
- Fireware OS 12.5.15 (T15 and T35 models)
- Fireware OS 12.3.1_Update4 (FIPS)
End-of-life versions do not receive fixes and should be removed from exposure.
References
🔗 WatchGuard PSIRT Advisory (WGSA-2025-00027)
🔗 The Hacker News — WatchGuard warns of active exploitation
🔗 CISA Known Exploited Vulnerabilities Catalog
🔗 CVE-2025-14733 record (cve.org)
Read about other CVEs
NodeZero® Platform
Implement a continuous find, fix, and verify loop with NodeZero
The NodeZero® platform empowers your organization to reduce your security risks by autonomously finding exploitable weaknesses in your network, giving you detailed guidance around how to priortize and fix them, and having you immediately verify that your fixes are effective.
Recognized By
如有侵权请联系:admin#unsafe.sh
