文章记录了2025年10月发现的一个加密货币骗局,骗子利用假聊天机器人和陷阱链接引诱受害者。骗局通过Telegraph平台和Google表单传播,声称受害者拥有大量比特币,并要求支付提现费用。该骗局持续到2026年,利用免费服务进行诈骗活动。 2026-1-4 04:30:30 Author: isc.sans.edu(查看原文) 阅读量:9 收藏
Introduction
In October 2025, a work colleague documented a cryptocurrency scam using a fake chatbot. After investigating this, I was able to receive messages from the campaign, and these emails have continued to land in my honeypot account since then. This diary documents the cryptocurrency scam campaign as it continues in 2026.
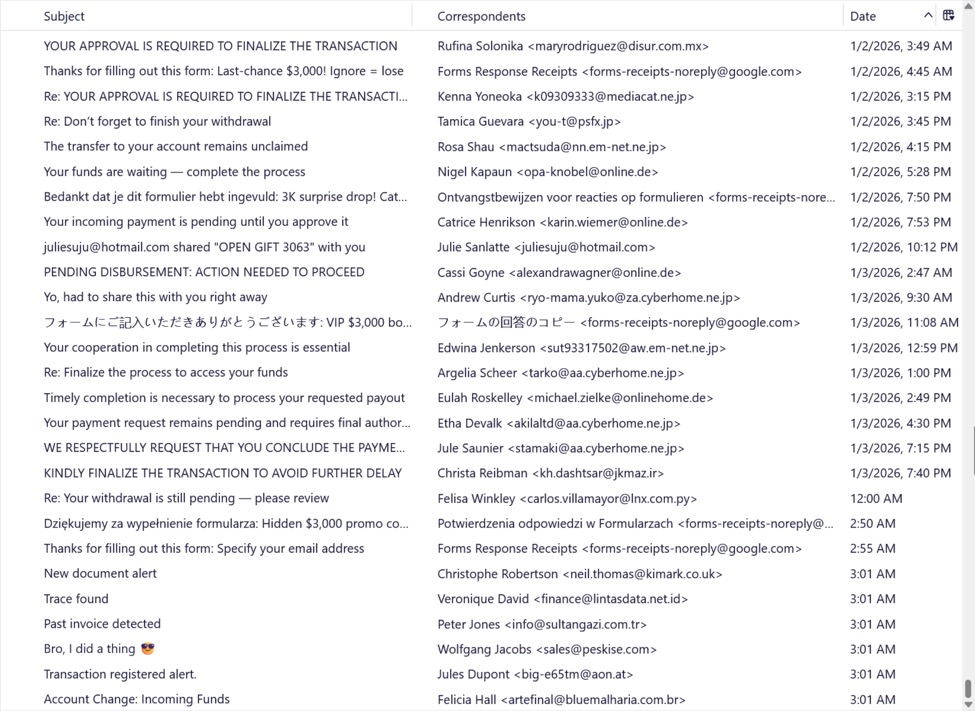
Shown above: My honeypot email inbox with several emails from this cryptocurrency scam campaign.
Details
This campaign promises cash payouts on cryptocurrency that potential victims unknowingly have.
This campaign primarily abuses the minimalist publishing platform telegra[.]ph, which anyone can use to publish a simple web page very quickly. Many of these emails have minimal messaging and contain links to these telegra[.]ph pages.
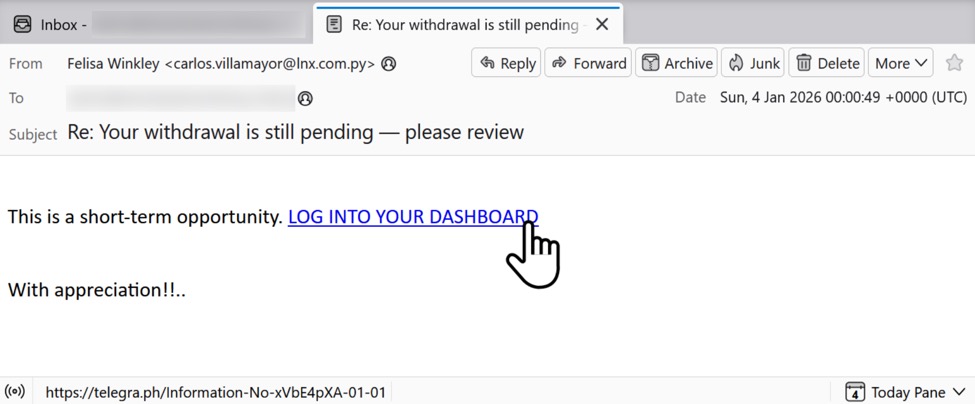
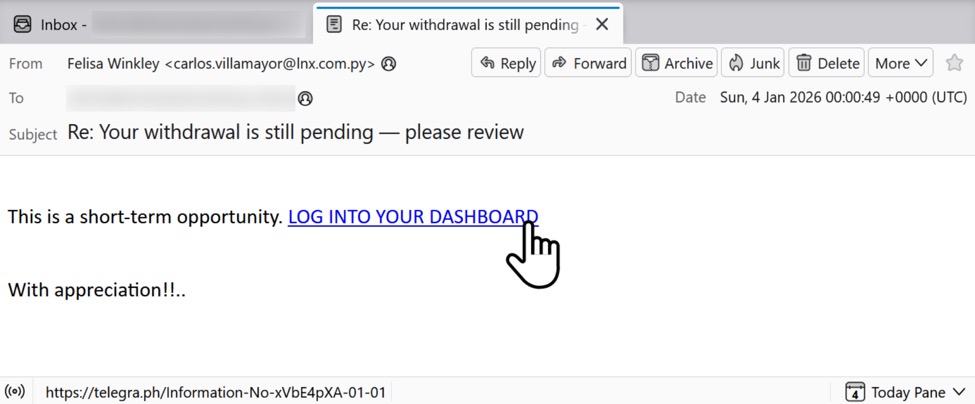
Shown above: Example of an email from this campaign with link to a telegra[.]ph page.
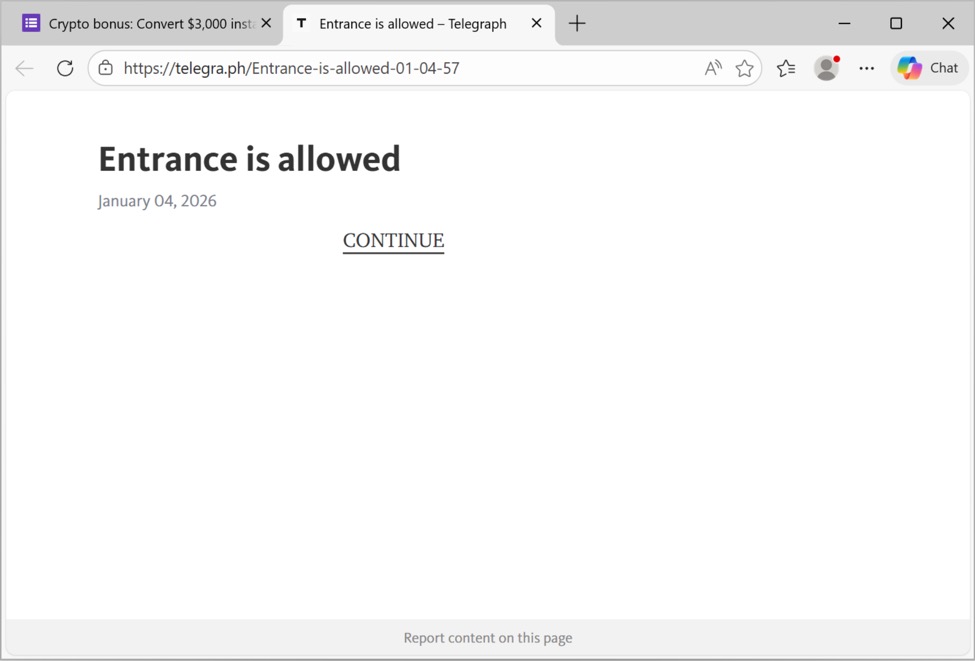
Shown above: Example of a telegra[.]ph page from this campaign.
This campaign is not limited to abusing telegra[.]ph. Many of these emails contain Google Forms pages that lead to the telegra[.]ph page.
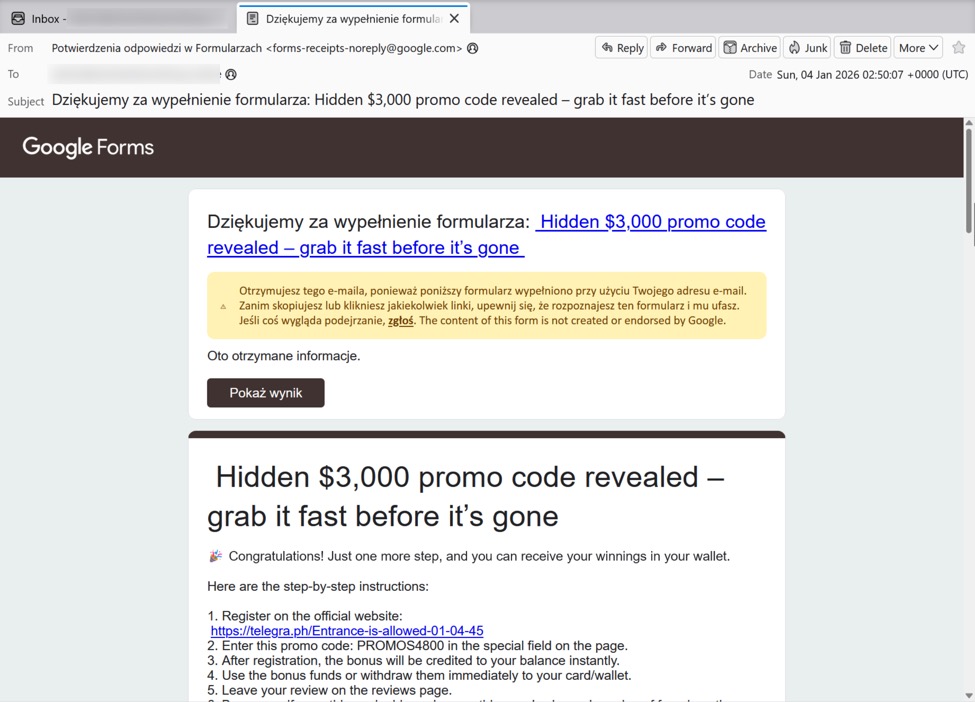
Shown above: Example of a Google Forms email from this campaign.
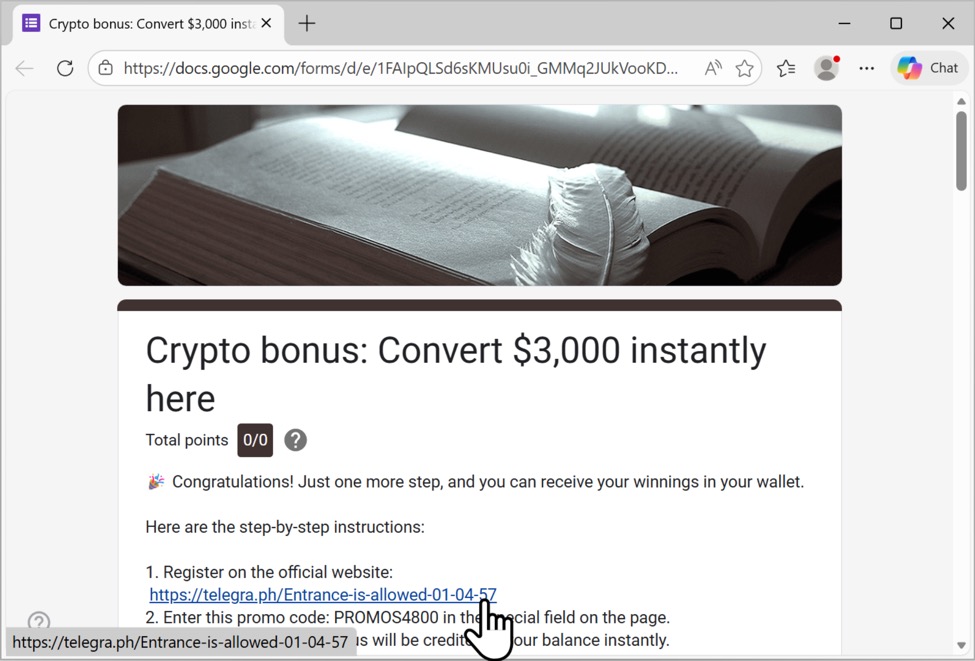
Shown above: Example of a response from the Google Forms link that leads to a telegra[.]ph page for this campaign.
These telegra[.]ph pages generally lead to the same type of cryptocurrency scam, stating you have over $100K in US dollars worth of Bitcoin from an automated Bitcoin mining cloud platform.
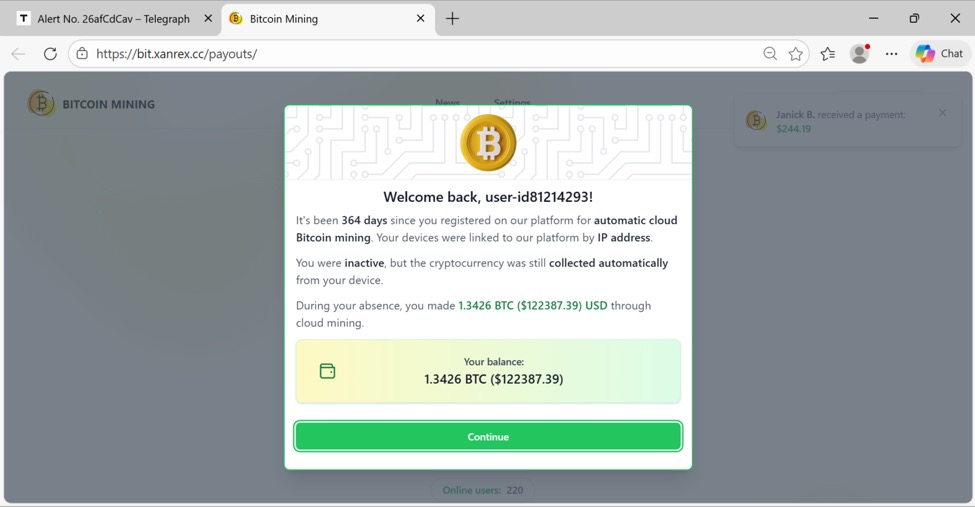
Shown above: Example of a page to begin the cryptocurrency scam.
In November 2025, I posted a video on YouTube, where I went through the website step-by-step, interacting with the fake chatbot to get to the actual scam. The scam involves paying a fee to convert the supposed Bitcoin to US dollars, which potential victims would send to a wallet controlled by the criminals.
Final Words
Many free services are easy to abuse for these types of campaigns. While these emails may seem obviously fake, they continue to be cost-effective for criminals to send, and criminals can easily abuse other services to host everything needed for this scam.
Bradley Duncan
brad [at] malware-traffic-analysis.net
如有侵权请联系:admin#unsafe.sh