嗯,用户让我帮忙总结一下这篇文章的内容,控制在100个字以内,而且不需要用“文章内容总结”或者“这篇文章”这样的开头。好的,我得先仔细阅读一下文章,抓住主要信息。 文章主要讲的是GreyNoise在2025年圣诞节期间观察到的针对Adobe ColdFusion漏洞的大规模攻击活动。攻击者来自日本的基础设施,利用了多个CVE漏洞,主要集中在2023-2024年的漏洞。攻击手法包括JNDI/LDAP注入和ProjectDiscovery Interactsh工具。攻击目标主要是美国、西班牙和印度的服务器,峰值出现在圣诞节当天。 接下来,我需要把这些信息浓缩到100字以内。首先提到GreyNoise监测到攻击活动的时间和目标:圣诞节期间针对ColdFusion漏洞的攻击。然后说明攻击者的来源和手法:日本基础设施、多个CVE漏洞、JNDI/LDAP注入。最后提到主要影响地区和时间点:美国、西班牙、印度,峰值在圣诞节。 这样组合起来应该可以满足用户的要求了。 </think> GreyNoise监测到2025年圣诞节期间针对Adobe ColdFusion漏洞的大规模攻击活动,攻击者利用日本基础设施和多个CVE漏洞进行JNDI/LDAP注入等手法,主要影响美国、西班牙和印度服务器,峰值出现在圣诞节当天。 2026-1-3 10:59:28 Author: securityaffairs.com(查看原文) 阅读量:6 收藏
Thousands of ColdFusion exploit attempts spotted during Christmas holiday

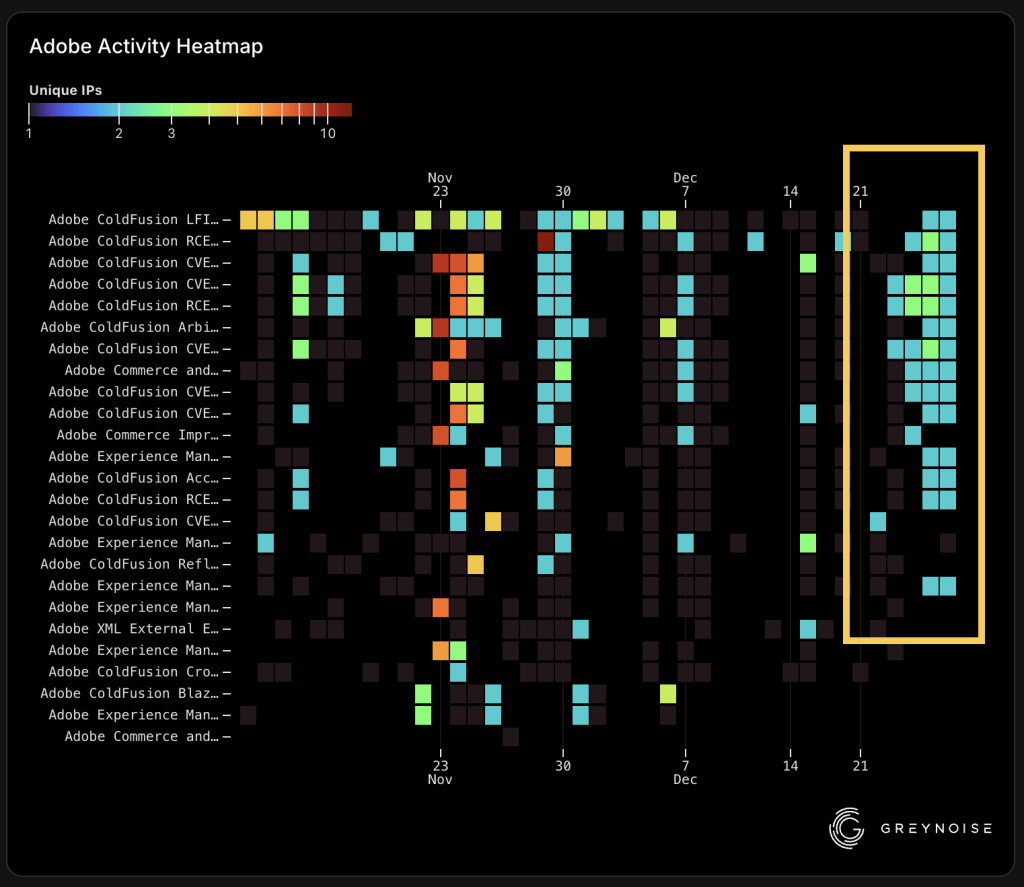
GreyNoise observed thousands of attacks targeting about a dozen Adobe ColdFusion vulnerabilities during the Christmas 2025 holiday.
GreyNoise reports a coordinated campaign exploiting about a dozen Adobe ColdFusion vulnerabilities, with thousands of attack attempts observed during the Christmas 2025 holiday.
“GreyNoise observed a coordinated exploitation campaign targeting Adobe ColdFusion servers over the Christmas 2025 holiday period.” reads the report published by GreyNoise. “The attack appears to be a single threat actor operating from Japan-based infrastructure (CTG Server Limited). This source was responsible for ~98% of attack traffic, systematically exploiting 10+ ColdFusion CVEs from 2023-2024.”
A single actor, using Japan-based infrastructure, generated about 98% of the traffic and exploited more than 10 ColdFusion CVEs from 2023–2024. The attacks used ProjectDiscovery Interactsh for out-of-band verification, with JNDI/LDAP injection as the main vector. Most activity occurred on Christmas Day, suggesting deliberate timing to exploit reduced security monitoring.
The researchers observed 5,940 malicious requests exploiting ColdFusion vulnerabilities from 2023–2024, peaking on December 25.
Most of the requests targeted servers in the US (4,044), Spain (753), and India (128).

GreyNoise identified a dominant threat actor using two IPs (134.122.136[.]119, 134.122.136[.]96) hosted by CTG Server Limited (AS152194), responsible for nearly all observed ColdFusion exploitation traffic. The two IPs accounted for over 98% of requests, operated concurrently in many cases, shared Interactsh sessions, and showed automated, coordinated behavior cycling through multiple attack types. Minor activity came from a handful of secondary IPs across Canada, India, the US, and Cloudflare. CTG Server Limited, a Hong Kong–registered provider with rapid IP space growth, has prior links to phishing, spam, bogon routing, and weak abuse enforcement, raising concerns about its role as a permissive hosting environment.
Below is the list of targeted ColdFusion vulnerabilities:
| CVE | Type | Requests |
|---|---|---|
| Generic RCE | Remote Code Execution | 1,403 |
| Generic LFI | Local File Inclusion | 904 |
| CVE-2023-26359 | Deserialization RCE | 833 |
| CVE-2023-38205 | Access Control Bypass | 654 |
| CVE-2023-44353 | Remote Code Execution | 611 |
| CVE-2023-38203 | Remote Code Execution | 346 |
| CVE-2023-38204 | Remote Code Execution | 346 |
| CVE-2023-29298 | Access Control Bypass | 342 |
| CVE-2023-29300 | Remote Code Execution | 176 |
| CVE-2023-26347 | Access Control Bypass | 171 |
| CVE-2024-20767 | Arbitrary File Read | 146 |
| CVE-2023-44352 | Reflected XSS | 8 |
Analysis shows the ColdFusion activity was only about 0.2% of a much larger vulnerability scanning campaign conducted from the same two IPs. Overall, the operation generated more than 2.5 million requests, targeting a total of 767 CVEs spanning 2001–2025, with over 1,200 attack signatures and thousands of unique fingerprints and OAST domains.
The campaign focused mainly on reconnaissance, followed by CVE exploitation, LFI, and RCE attempts. It targeted more than 47 technology stacks, including Java application servers, web frameworks, CMS platforms, network devices, and enterprise software. The scale, breadth of CVEs, and automation indicators point to a systematic, template-based reconnaissance effort covering the global vulnerability landscape.
The experts published Indicators of Compromise for this campaign.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Adobe)
如有侵权请联系:admin#unsafe.sh