嗯,用户让我帮忙总结一篇文章的内容,控制在一百个字以内,而且不需要用“文章内容总结”或者“这篇文章”这样的开头。直接写描述就行。 首先,我需要仔细阅读这篇文章。看起来是关于一个叫做Zoom Stealer的恶意活动,影响了超过两百万的浏览器用户。这个活动通过18个扩展程序收集在线会议的数据,包括URL、ID、嵌入密码等。 文章还提到,这个活动是由一个叫做DarkSpectre的威胁行为者发起的,他们之前还做过其他类似的恶意活动,比如GhostPoster和ShadyPanda。这些扩展程序看起来功能正常,但实际上是用来收集会议信息的。 此外,文章指出DarkSpectre可能与中国有关联,因为他们的基础设施和代码中都有中文元素。这些收集的数据可以用于企业间谍活动或钓鱼攻击。 用户的需求是希望有一个简洁的总结,不超过100字。所以我要抓住关键点:Zoom Stealer是什么,影响了多少人,通过什么方式传播,以及可能带来的威胁。 可能还需要提到DarkSpectre和之前的活动关联,以及数据如何被利用。不过要注意字数限制,所以可能需要简化一些细节。 最后,确保语言简洁明了,直接描述内容,不需要多余的开头。 </think> 研究人员发现名为Zoom Stealer的恶意活动通过18个浏览器扩展程序影响220万用户,收集在线会议数据如链接、ID、密码等,用于企业间谍和钓鱼攻击。该活动由DarkSpectre团伙发起,与之前针对Firefox和Chrome用户的恶意活动相关联,且与中国有关联。 2025-12-30 16:30:49 Author: www.bleepingcomputer.com(查看原文) 阅读量:7 收藏

A newly discovered campaign, which researchers call Zoom Stealer, is affecting 2.2 million Chrome, Firefox, and Microsoft Edge users through 18 extensions that collect online meeting-related data like URLs, IDs, topics, descriptions, and embedded passwords.
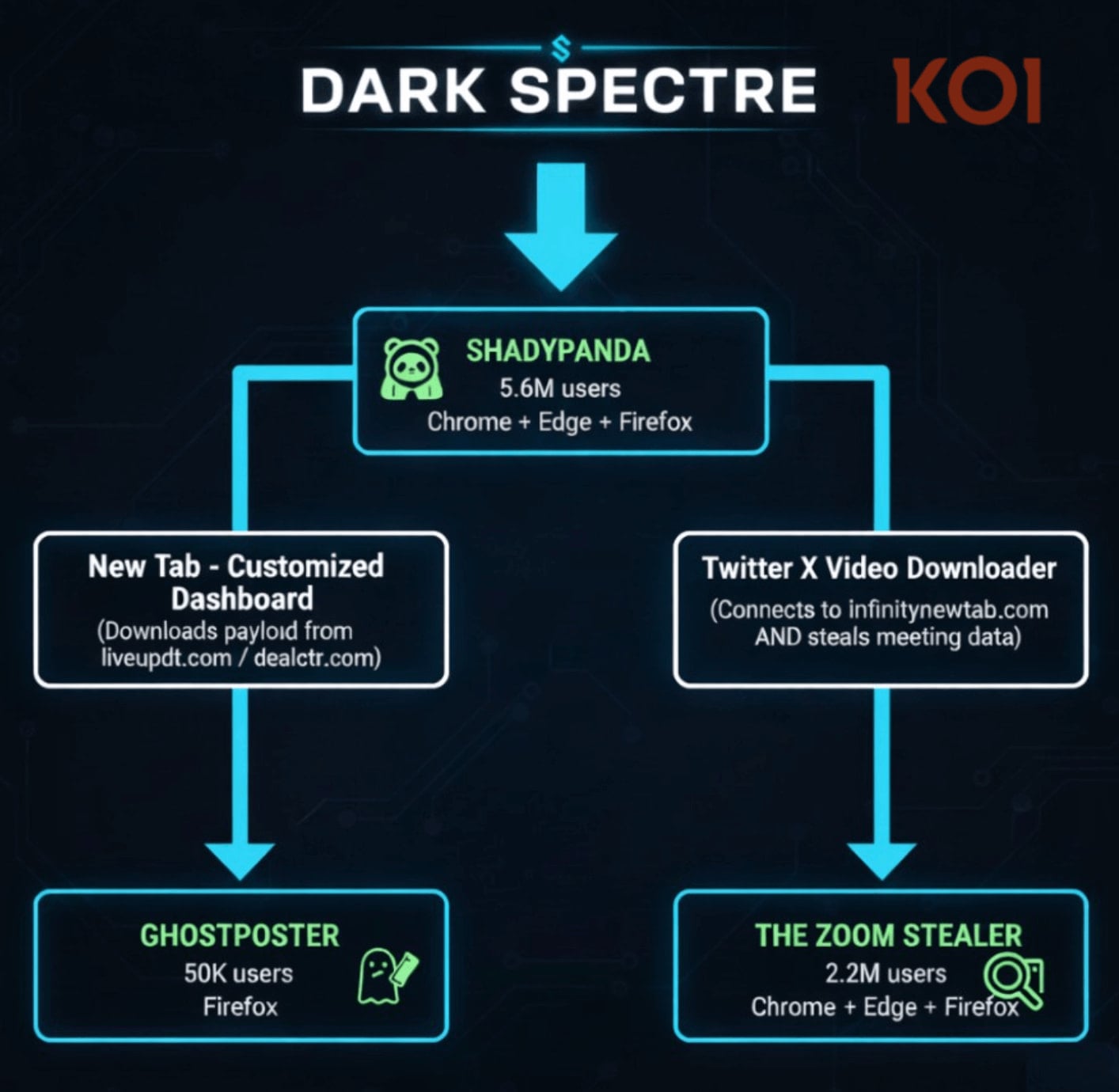
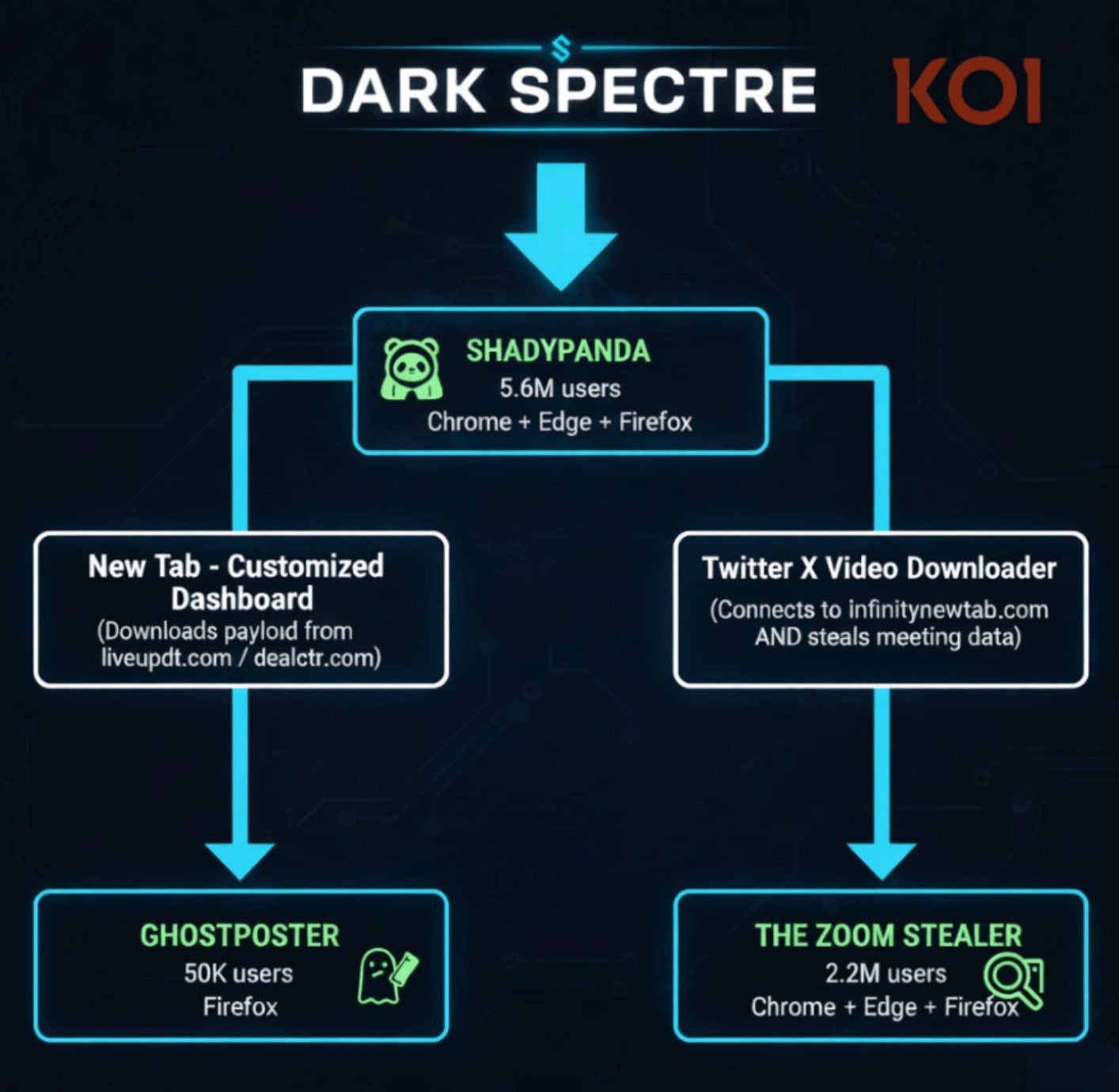
Zoom Stealer is one of three browser extension campaigns that reached more than 7.8 million users over seven years and are attributed to a single threat actor tracked as DarkSpectre.
Based on the used infrastructure, DarkSpectre is believed to be the same China-linked threat actor behind the previously documented GhostPoster, which targeted Firefox users, and ShadyPanda, which delivered spyware payloads to Chrome and Edge users.
ShadyPanda remains active through 9 extensions and an additional 85 'sleepers' that build a user base before turning malicious via updates, researchers at supply-chain security company Koi Security say.
Source: Koi Security
Although the China connection existed before, attribution is now clearer based on hosting servers on Alibaba Cloud, ICP registrations, code artifacts containing Chinese-language strings and comments, activity patterns that match the Chinese timezone, and monetization targeting tuned to Chinese e-commerce.
Corporate meeting intelligence
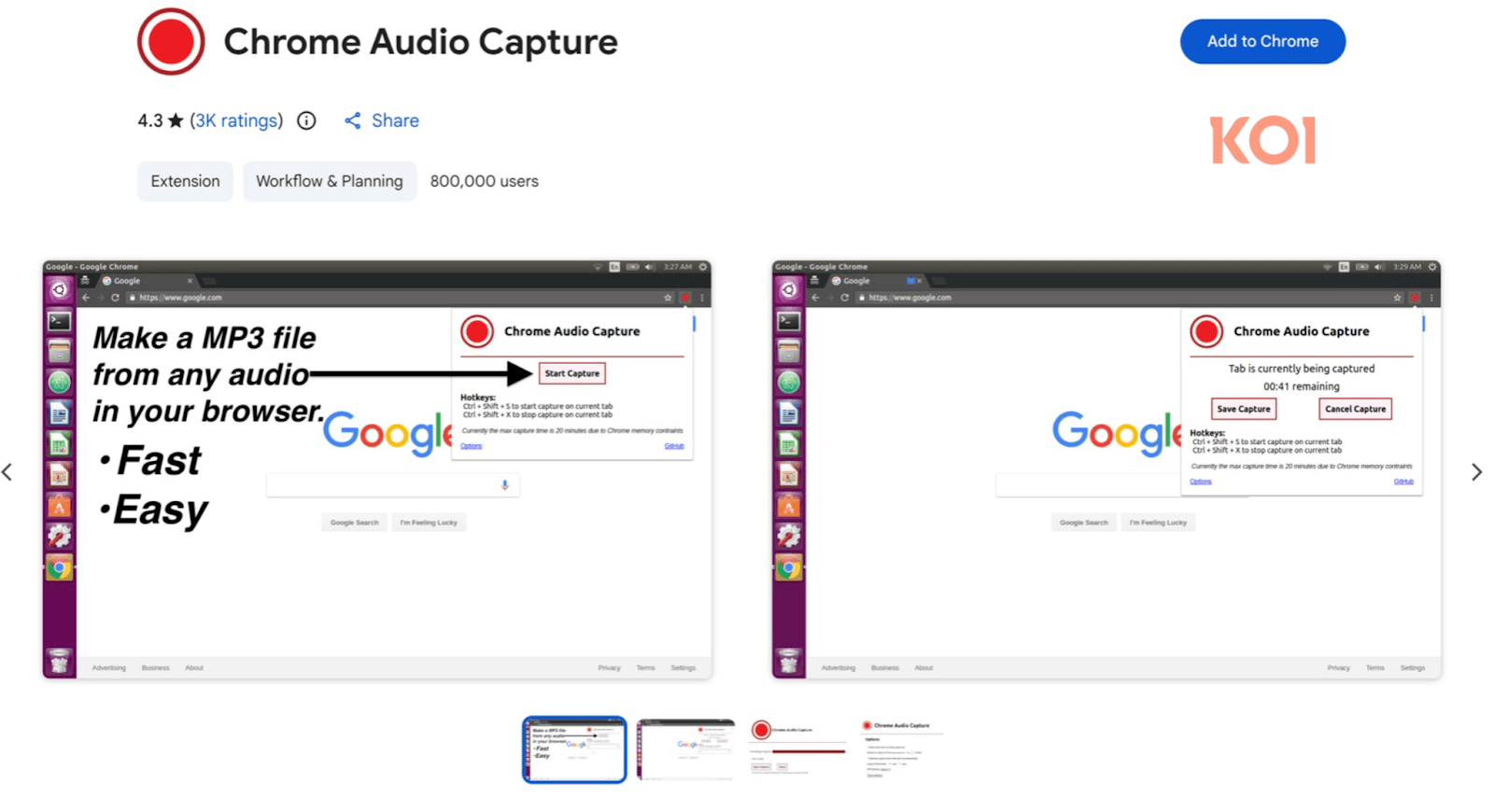
The 18 extensions in the Zoom Stealer campaign are not all meeting-related, and some of them can be used to download videos or as recording assistants: Chrome Audio Capture with 800,000 installations, and Twitter X Video Downloader. Both are still available on the Chrome Web Store at publishing time.
Koi Security researchers note that the extensions are all functional and work as advertised.
Source: Koi Security
According to the researchers, all extensions in the Zoom Stealer campaign request access to 28 video-conferencing platforms (e.g., Zoom, Microsoft Teams, Google Meet, and Cisco WebEx) and collect the following data:
- Meeting URLs and IDs, including embedded passwords
- Registration status, topics, and scheduled times
- Speaker and host names, titles, biographies, and profile photos
- Company logos, graphics, and session metadata
This data is exfiltrated via WebSocket connections and streamed to the threat actors in real time. This activity is triggered when victims visit webinar registration pages, join meetings, or navigate conferencing platforms.
Koi Security says this data can be used for corporate espionage and sales intelligence, which could be used in social engineering attacks or even to sell meeting links to competitors.
"By systematically collecting meeting links, participant lists, and corporate intelligence across 2.2 million users, DarkSpectre has created a database that could power large-scale impersonation operations - providing attackers with credentials to join confidential calls, participant lists to know who to impersonate, and context to make those impersonations convincing," notes the report from Koi Security.
Because many of these extensions operated innocuously for extended periods, users should carefully review the permissions the extensions require and limit their number to the necessary minimum.
Koi Security reported the offending extensions, but many are still present on the Chrome Web Store. The researchers published the complete list of active DarkSpectre extensions.
BleepingComputer has contacted InfinityNewTab and Google for a comment and we will update the article when we hear back.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.
如有侵权请联系:admin#unsafe.sh

