文章指出传统基于边缘的安全模型已无法应对生成式AI带来的内部API风险。生成式AI通过API与系统交互引发复杂行为链,传统防火墙和WAF难以检测。文章强调需采用多维度API监控和实时智能技术(如Salt Security)以应对新兴威胁。 2025-12-30 13:0:1 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
For the last twenty years, cybersecurity has been built around the edge: the belief that threats come from the outside, and that firewalls, WAFs, and API gateways can inspect and control what enters the environment.
That model worked when applications were centralized, traffic was predictable, and most interactions followed a clear pattern: a user in a browser talking to an app inside a data center.
Agentic AI breaks that model.
Today, AI systems don’t just generate responses — they take action. Agents trigger workflows, call APIs, update records, fan out across services, and interact autonomously with internal systems and third-party SaaS. That shift moves the risk inside the API ecosystem, where perimeter-based tools have limited visibility.
The Architectural Truth: The Perimeter Model No Longer Fits Modern Traffic
Legacy perimeter tools were designed for a world with simple assumptions:
- Users sit at the “edge”
- Apps sit inside a defensible perimeter
- Traffic is predictable
- Lateral movement is limited and observable
Agentic AI broke those assumptions almost overnight.
APIs already made every service both a client and a server. Agentic AI amplifies this by turning every LLM, MCP server, automation tool, and SaaS ecosystem into an active participant in your environment.
A single user request can now trigger:
- An AI assistant
- An MCP server
- 10–50 downstream internal API calls
- SaaS workflows
- Webhooks firing back internally
- Additional agent actions
- More API calls
- More SaaS integrations
This is no longer “north–south vs. east–west.” In the age of agentic AI, API traffic behaves more like a scene from Everything Everywhere All at Once — chaotic, multi-directional, and hard to predict.
The API Fabric: A Multi-Directional Mesh of Constant Motion
In the API fabric, every node is both client and server:
- An AI agent is a client of your MCP server and a server for chat APIs.
- A microservice is a server to another service and a client of databases and SaaS.
- A SaaS platform is a server for your webhooks and a client to your internal APIs.
This means the most security-critical flows now look like:
- External prompt → LLM → MCP server → sensitive internal API
- Stolen SaaS token → third-party app → your webhook → internal automation API
- Internal agent → external SaaS → unmonitored data exfil path
Attackers don’t care about compass directions. They care about the fastest chain of APIs that reaches sensitive data.
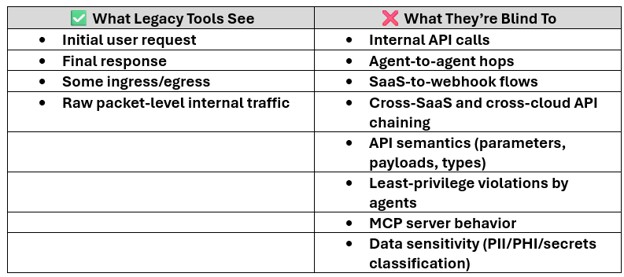
Why Edge Security and WAAP Tools Miss Most of the Agentic AI Attack Chain
Neither WAFs nor WAAPs were designed for:
- Multi-directional internal API behavior
- AI-generated machine-to-machine traffic
- SaaS-to-webhook flows
- Agent-to-agent interactions
- MCP server exposures
- Emerging AI action-layer abuse patterns
Here’s what they see vs. what they miss:
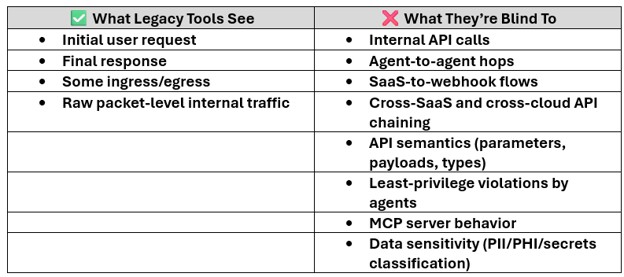
Still feel secure? You might want to rethink your posture
Point solutions give snapshot visibility. Agentic AI creates continuous, dynamic API behavior. The gap between those two is now a systemic security risk
Why Multi-Directional Visibility Is Now Mandatory
To secure APIs — and the AI agents sitting on top of them — security teams need visibility into:
- Every caller: users, services, SaaS apps, agents, schedulers
- Every call: internal, external, cross-cloud, cross-SaaS
- Every chain: multi-hop workflows that create “off-axis” paths to sensitive systems
- Every behavior pattern: normal vs. anomalous vs. malicious
- Every data flow: sensitive fields, policy violations, and data movement
Agentic AI doesn’t attack your perimeter. It attacks your blind spots inside the API fabric.
Why Salt Security Is Built for the API Fabric (and for Agentic AI)
Salt is purpose-built for this new world — designed around the API fabric itself, not a perimeter model.
Salt provides the multi-directional visibility and runtime intelligence required to secure agentic AI environments:
1) Observe API traffic where it actually runs
Across cloud environments, gateways, service meshes, MCP servers, and SaaS-driven workflows — including east/west and agent-created “off-axis” paths.
2) Reconstruct the real API fabric
Salt rebuilds the operational truth: what APIs exist, who is calling them (including agents and SaaS tools), how data moves, and where risk accumulates.
3) Detect and stop what edge tools can’t
Salt identifies high-risk behavior that perimeter tools miss, including misconfigured or over-permissioned agents, abnormal API chaining, new exposure from MCP integrations, and data exfil paths that look like “normal” workflows until you see the full chain.
Recent Salt capabilities reinforce this approach, including:
- Salt MCP Finder: discovers MCP servers before attackers do
- Salt Illuminate™: unified runtime intelligence across the fabric
- Ask Pepper AI: natural-language analysis of API risk and posture
Conclusion: The Risk Has Moved. Security Has to Move With It.
Agentic AI has shifted risk away from the perimeter and deep into the API fabric. Firewalls, WAFs, and gateways were never designed to observe or understand the behavior of LLMs, MCP servers, or autonomous agents moving across internal and SaaS-connected systems.
Security teams need to see every actor, every call, and every chain — not just what crosses the edge.
The edge is no longer where your risk lives. Your APIs are. And now, so are your agents.
If you want to learn more about Salt and how we can help you, please contact us, schedule a demo, or visit our website. You can also get a free API Attack Surface Assessment from Salt Security’s research team and learn what attackers already know.
*** This is a Security Bloggers Network syndicated blog from Salt Security blog authored by Eric Schwake. Read the original post at: https://salt.security/blog/edge-security-is-not-enough-why-agentic-ai-moves-the-risk-inside-your-apis
如有侵权请联系:admin#unsafe.sh