嗯,用户让我用中文总结一下这篇文章,控制在一百个字以内,而且不需要用“文章内容总结”之类的开头。好的,我先仔细读一下文章内容。 这篇文章讲的是一个立陶宛男子被逮捕,他涉嫌传播了一种叫做KMSAuto的恶意软件。这种软件窃取了剪贴板数据,并感染了大约280万台Windows和Office系统。他通过将恶意软件嵌入到KMSAuto这个非法的Windows激活工具中,来传播这种剪贴板窃取的恶意软件。这种恶意软件会监控用户的剪贴板,寻找加密货币地址,并将其替换为攻击者控制的钱包地址,从而在用户不知情的情况下转移加密货币交易。 从2020年到2023年,这种伪装成非法Windows激活工具的恶意软件被下载了大约280万次。通过这种方式,攻击者进行了8400次交易,涉及3100个钱包,总共窃取了约17亿韩元的加密资产。其中有8名韩国受害者损失了约1600万韩元。 警方在2020年8月展开调查,因为有人在使用KMSAuto下载后,在交易中损失了1比特币。经过调查,他们发现了这个立陶宛嫌疑人,并通过国际刑警组织协调将其从格鲁吉亚引渡到韩国。 总结一下,文章主要讲述了立陶宛男子利用KMSAuto传播恶意软件,窃取加密货币的事件及其影响和警方的行动。 现在我需要把这些信息浓缩到100字以内。重点包括:立陶宛男子被逮捕、传播KMSAuto恶意软件、感染280万台系统、窃取加密货币、警方行动等。 可能的结构是:立陶宛男子因传播KMSAuto恶意软件被捕,该软件感染了280万台系统并窃取加密货币地址,导致大量损失。警方跨国合作将其逮捕。 检查一下字数是否合适。 </think> 一名立陶宛男子因涉嫌传播KMSAuto恶意软件被捕。该软件感染了约280万台Windows和Office系统,并窃取用户剪贴板中的加密货币地址以实施盗窃。警方跨国合作将其逮捕。 2025-12-30 11:26:46 Author: securityaffairs.com(查看原文) 阅读量:7 收藏
Lithuanian suspect arrested over KMSAuto malware that infected 2.8M systems
Pierluigi Paganini
December 30, 2025

A Lithuanian national was arrested for allegedly spreading KMSAuto malware that stole clipboard data and infected 2.8 million Windows and Office systems.
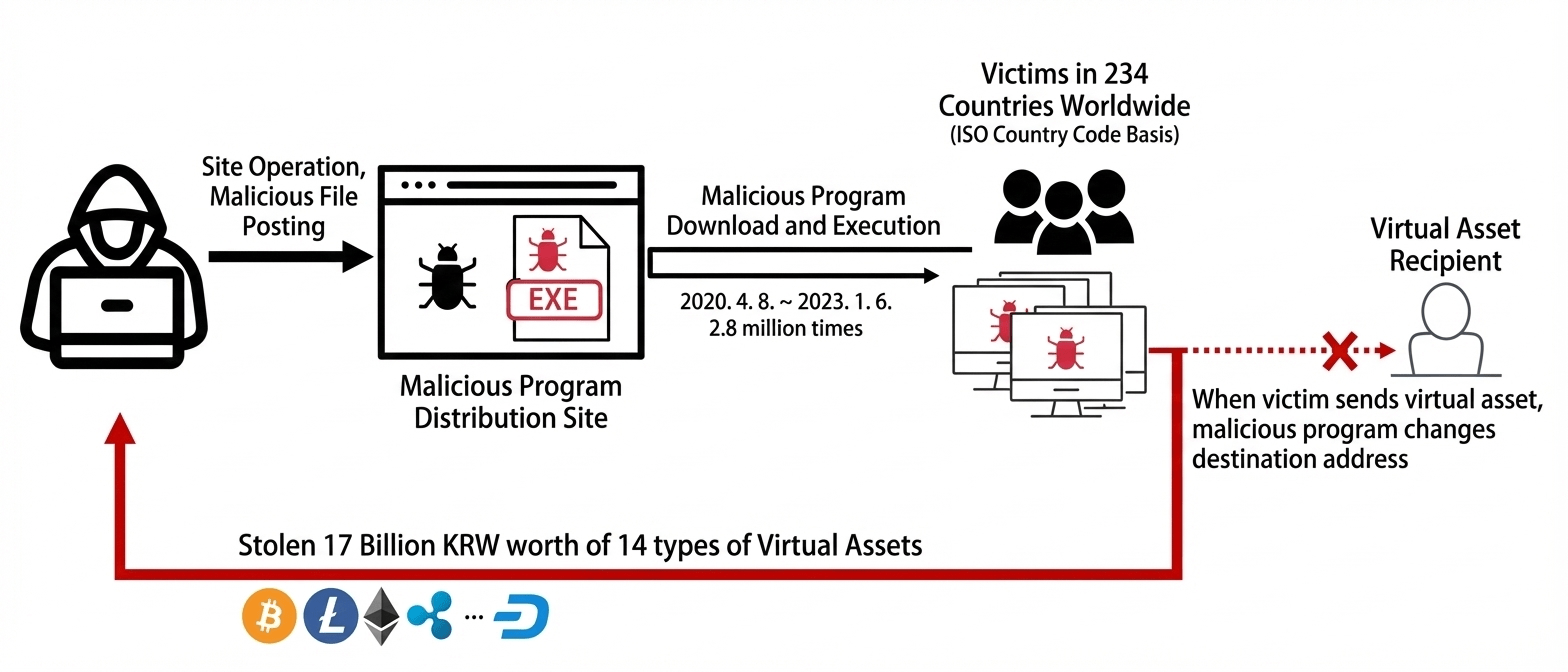
A Lithuanian man (29) was arrested for allegedly spreading KMSAuto-based clipboard-stealing malware that infected about 2.8 million Windows and Office systems.
The man was extradited from Georgia to South Korea under Interpol coordination. Authorities say he trojanized the KMSAuto piracy tool to distribute clipper malware that monitored victims’ clipboards for cryptocurrency addresses and replaced them with attacker-controlled wallets, redirecting crypto transactions without users’ knowledge.
According to the Korean National Police Agency, the suspect used KMSAuto to lure victims into downloading a malicious executable that scanned the clipboard for cryptocurrency addresses and replaced them with ones controlled by the attacker – known as ‘clipper malware’.
According to the Korean National Police Agency, the suspect added malware to the KMSAuto tool that checked clipboard contents for cryptocurrency addresses and changed the destination address to one controlled by the attacker. This type of threat is called clipper malware.
From 2020 to 2023, malware disguised as the illegal Windows activator KMSAuto was downloaded about 2.8 million times worldwide. The clipper malware replaced crypto wallet addresses during transactions, enabling theft via 8,400 transfers from 3,100 wallets, totaling about ₩1.7 billion. Eight South Korean victims lost ₩16 million, with infections traced to pirated software.
“Between April 2020 and January 2023, the suspect distributed malware disguised as an illegal Windows activation tool known as KMSAuto. The malicious software was downloaded approximately 2.8 million times worldwide, including in South Korea.” reads the press realese issued by the Korean police. “Investigators identified 3,100 compromised cryptocurrency wallet addresses, which were used in 8,400 transactions to steal virtual assets worth approximately 1.7 billion won. Eight South Korean victims were confirmed, suffering combined losses of about 16 million won.”

In August 2020, police launched an investigation after a victim lost 1 Bitcoin, worth about 12 million won, when malware automatically replaced the intended wallet address with one controlled by a hacker during a transaction. The infection came from KMSAuto, an illegal Windows activation tool downloaded online. Investigators uncovered a large-scale international operation targeting exchanges and companies across six countries, traced illicit crypto flows, and identified a Lithuanian suspect. With the help of international partners, police seized the suspect’s devices, issued an Interpol red notice, and arrested the suspect in Georgia.
“Various damages caused by malicious programs To prevent this, you should be careful with programs from unknown sources..”saying,“In the future too Police are working with law enforcement agencies around the world to combat borderless cybercrime. We plan to respond strictly, including repatriation.”. Park Woo-hyun, cyber investigation director at the National Police Agency, said.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, malware)
如有侵权请联系:admin#unsafe.sh