
好的,我现在需要帮用户总结一篇文章的内容,控制在100字以内。用户的要求是直接写文章描述,不需要开头语。首先,我得仔细阅读文章内容,抓住关键点。 文章主要讲的是ToneShell后门的新样本被用于针对政府机构的攻击。这个后门被归因于Mustang Panda组织,他们通常攻击政府机构、NGO等高调组织。Kaspersky的研究人员分析了一个恶意驱动程序,发现它从2025年2月起被用于攻击亚洲国家的政府机构。 此外,文章提到这个新样本使用了内核模式加载器,这是首次出现的情况。驱动程序ProjectConfiguration.sys使用了被盗的证书,并且具备多种逃避检测的机制,比如隐藏文件操作、干扰微软 Defender等。 总结时要包括关键信息:ToneShell的新样本、Mustang Panda组织、针对政府机构、内核模式加载器、逃避检测机制以及攻击目标地区。 现在把这些要点浓缩到100字以内。确保涵盖主要攻击者、技术手段和影响范围。 </think> ToneShell后门的新样本通过内核模式加载器传播,针对政府机构实施网络间谍活动。该恶意软件由Mustang Panda组织开发,具备隐藏功能和文件操作拦截能力,并干扰微软 Defender以规避检测。攻击主要针对亚洲国家的政府机构。 2025-12-30 00:16:16 Author: www.bleepingcomputer.com(查看原文) 阅读量:21 收藏

A new sample of the ToneShell backdoor, typically seen in Chinese cyberespionage campaigns, has been delivered through a kernel-mode loader in attacks against government organizations.
The backdoor has been attributed to the Mustang Panda group, also known as HoneyMyte or Bronze President, that usually targets government agencies, NGOs, think tanks, and other high-profile organizations worldwide.
Security researchers at Kaspersky analyzed a malicious file driver found on computer systems in Asia and discovered that it has been used in campaigns since at least February 2025 against government organizations in Myanmar, Thailand, and other Asian countries.
Evidence showed that the compromised entities had prior infections with older ToneShell variants, PlugX malware, or the ToneDisk USB worm, also attributed to state-sponsored Chinese hackers.
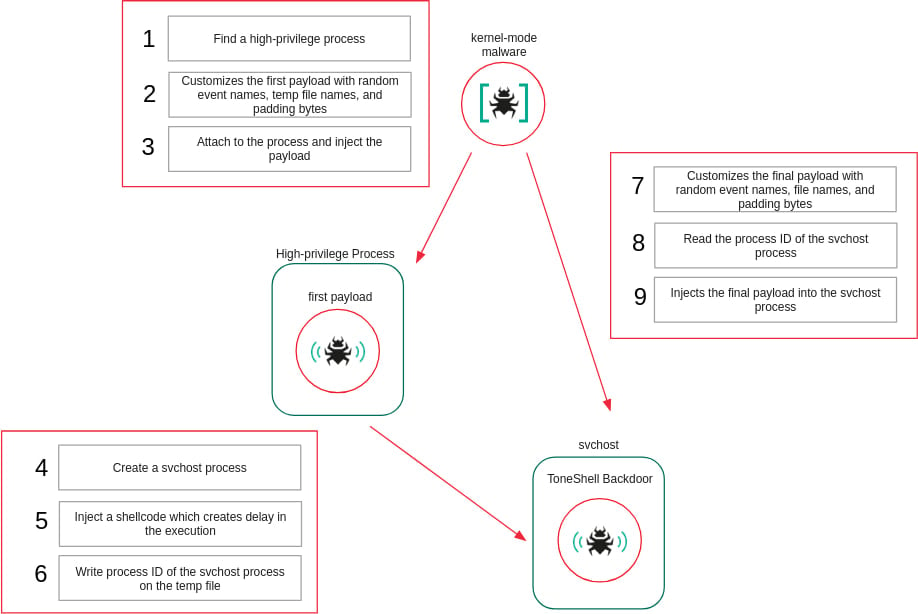
New kernel-mode rootkit
According to Kaspersky, the new ToneShell backdoor was deployed by a mini-filter driver named ProjectConfiguration.sys and signed with a stolen or leaked certificate valid between 2012 and 2015 and issued to Guangzhou Kingteller Technology Co., Ltd.
Mini-filters are kernel-mode drivers that plug into the Windows file-system I/O stack and can inspect, modify, or block file operations. Security software, encryption tools, and backup utilities typically use them.
ProjectConfiguration.sys embeds two user-mode shellcodes in its .data section, each executed as a separate user-mode thread to be injected into user-mode processes.
To evade static analysis, the driver resolves required kernel APIs at runtime by enumerating loaded kernel modules and matching function hashes, rather than importing functions directly.
It registers as a mini-filter driver and intercepts file-system operations related to deletion and renaming. When such operations target the driver itself, they are blocked by forcing the request to fail.
The driver also protects its service-related registry keys by registering a registry callback and denying attempts to create or open them. To ensure priority over security products, it selects a mini-filter altitude above the antivirus-reserved range.
Additionally, the rootkit interferes with Microsoft Defender by modifying the configuration of the WdFilter driver so it is not loaded into the I/O stack.
To shield injected user-mode payloads, the driver maintains a list of protected process IDs, denies handle access to those processes while the payloads are executing, and removes protection once execution completes.
"This is the first time we’ve seen ToneShell delivered through a kernel-mode loader, giving it protection from user-mode monitoring and benefiting from the rootkit capabilities of the driver that hides its activity from security tools," says Kaspersky.
Source: Kaspersky
New ToneShell variant
The new variant of the ToneShell backdoor that Kaspersky analyzed features changes and stealth enhancements. The malware now uses a new host identification scheme based on a 4-byte host ID market instead of the 16-byte GUID used previously, and also applies network traffic obfuscation with fake TLS headers.
In terms of the supported remote operations, the backdoor now supports the following commands:
- 0x1 — Create a temporary file for incoming data
- 0x2 / 0x3 — Download file
- 0x4 — Cancel download
- 0x7 — Establish a remote shell via a pipe
- 0x8 — Receive operator command
- 0x9 — Terminate shell
- 0xA / 0xB — Upload file
- 0xC — Cancel upload
- 0xD — Close connection
Kaspersky advises that memory forensics is key in uncovering ToneShell infections backed by the new kernel-mode injector.
The researchers have high confidence in attributing the new ToneShell backdoor sample to the Mustang Panda cyberespionage group. They assess that the threat actor has evolved its tactics, techniques, and procedures to gain operational stealth and resilience.
The cybersecurity company provides in its report a short list of indicators of compromise (IoCs) to help organizations detect Mustang Panda intrusions and defend against them.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.
如有侵权请联系:admin#unsafe.sh

