
一名立陶宛男子因涉嫌利用伪装成KMSAuto工具的剪贴板窃取恶意软件感染280万台设备被捕。该软件通过扫描剪贴板中的加密货币地址并将其替换为攻击者控制的地址来窃取虚拟资产。 2025-12-29 19:30:39 Author: www.bleepingcomputer.com(查看原文) 阅读量:7 收藏

A Lithuanian national has been arrested for his alleged involvement in infecting 2.8 million systems with clipboard-stealing malware disguised as the KMSAuto tool for illegally activating Windows and Office software.
The 29-year-old man was extradited from Georgia to South Korea following a related request under Interpol’s coordination.
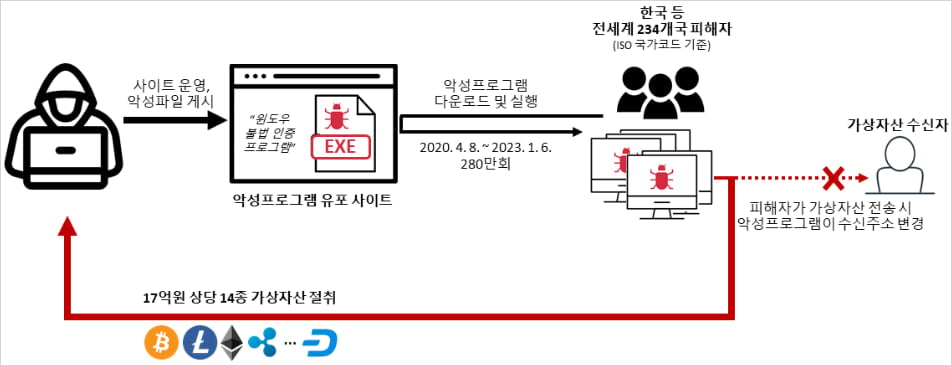
According to the Korean National Police Agency, the suspect used KMSAuto to lure victims into downloading a malicious executable that scanned the clipboard for cryptocurrency addresses and replaced them with ones controlled by the attacker - known as 'clipper malware'.
According to the Korean National Police Agency, the suspect added malware to the KMSAuto tool that checked clipboard contents for cryptocurrency addresses and changed the destination address to one controlled by the attacker. This type of threat is called clipper malware.
"From April 2020 to January 2023, the hacker distributed 2.8 million copies worldwide of malware disguised as an illegal Windows license activation program (KMSAuto)," the police say.
"Through this malware, the hacker stole virtual assets worth approximately KRW 1.7 billion ($1.2 million) in 8,400 transactions from users of 3,100 virtual asset addresses."
The police started the investigation in August 2020, following a report about cryptojacking, where the victim’s system was infected by clipper malware, swapping the intended recipient’s wallet address to direct payments to the attacker.
Source: police.go.kr
The investigation uncovered a malware infection through the said KMSAuto tool. The clipper targeted at least six cryptocurrency exchanges, according to the investigators.
After tracing the stolen amounts and identifying the perpetrator, a raid occurred in December 2024 in Lithuania, where 22 items, including laptop computers and mobile phones, were confiscated.
Examination of the seized items revealed incriminating evidence, eventually leading to the arrest of the hacker in April 2025, while he was traveling from Lithuania to Georgia.
The South Korean police remind the public that using illegal software that violates copyright is risky because such tools can introduce malware into the system.
This type of utility has often been used to distribute malware. Recently, cybercriminals impersonated the Microsoft Activation Scripts (MAS) tool to spread PowerShell scripts that delivered the Cosmali Loader malware.
It is recommended to avoid using unofficial software product activators and, more generally, any Windows executables that aren’t digitally signed and whose source or integrity cannot be validated.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.
如有侵权请联系:admin#unsafe.sh

