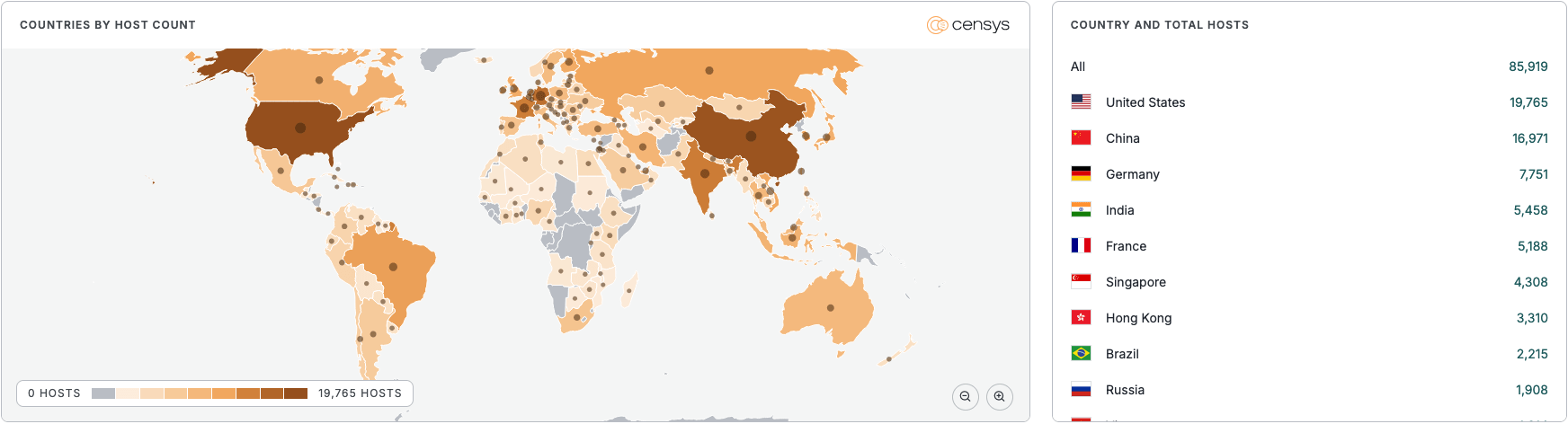
MongoBleed(CVE-2025-14847)是一种高危漏洞,影响全球超8.7万 MongoDB 实例。未授权攻击者可借此泄露服务器内存数据。该漏洞源于 zlib 消息解压功能,默认启用且影响多个 MongoDB 版本。建议用户立即升级至修复版本或禁用 zlib 压缩以缓解风险。 2025-12-29 12:56:44 Author: securityaffairs.com(查看原文) 阅读量:11 收藏
MongoBleed flaw actively exploited in attacks in the wild
Pierluigi Paganini
December 29, 2025

A recently disclosed MongoDB flaw (MongoBleed) is under active exploitation, with over 87,000 potentially vulnerable instances exposed worldwide.
A newly disclosed MongoDB vulnerability, tracked as CVE-2025-14847 (aka MongoBleed, CVSS score of 8.7), is being actively exploited, with more than 87,000 potentially vulnerable instances identified worldwide.
Cybersecurity researcher Joe Desimone published a proof-of-concept exploit for this vulnerability that allows unauthenticated attackers to leak sensitive server memory.
According to Censys, most of the potentially vulnerable instances are in the U.S., China, Germany, and India.
“A working exploit has been publicly available since December 26, 2025, with initial reporting of exploitation in the wild reported shortly after.” reads the report published by cybersecurity firm Wiz.
At this time, attack details remain unclear.

MongoDB is a popular open-source NoSQL database used to store and manage data in a flexible, document-based format.
Instead of tables and rows like traditional SQL databases, MongoDB stores data as JSON-like documents (called BSON). This makes it well-suited for modern applications that need scalability, high performance, and flexible data models.
The vulnerability CVE-2025-14847 can allow an unauthenticated, remote attacker to execute arbitrary code on vulnerable servers.
“An client-side exploit of the Server’s zlib implementation can return uninitialized heap memory without authenticating to the server. We strongly recommend upgrading to a fixed version as soon as possible.” reads the advisory.
The issue stems zlib message decompression, which is enabled by default, and allows unauthenticated attackers to leak data from MongoDB servers at the network level. The vulnerability impacts publicly exposed instances and reachable private servers. Exploitation can lead to gradual extraction of sensitive data such as user details, passwords, and API keys.
This flaw impacts the following MongoDB versions:
- MongoDB 8.2.0 through 8.2.3
- MongoDB 8.0.0 through 8.0.16
- MongoDB 7.0.0 through 7.0.26
- MongoDB 6.0.0 through 6.0.26
- MongoDB 5.0.0 through 5.0.31
- MongoDB 4.4.0 through 4.4.29
- All MongoDB Server v4.2 versions
- All MongoDB Server v4.0 versions
- All MongoDB Server v3.6 versions
Versions 8.2.3, 8.0.17, 7.0.28, 6.0.27, 5.0.32, and 4.4.30 addressed the issue.
Users should upgrade immediately or, if unable, disable zlib compression on MongoDB by configuring compression options to omit zlib.
“We strongly suggest you upgrade immediately.” continues the advisory. “If you cannot upgrade immediately, disable zlib compression on the MongoDB Server by starting mongod or mongos with a networkMessageCompressors or a net.compression.compressors option that explicitly omits zlib. Example safe values include snappy,zstd or disabled”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, MongoBleed)
如有侵权请联系:admin#unsafe.sh