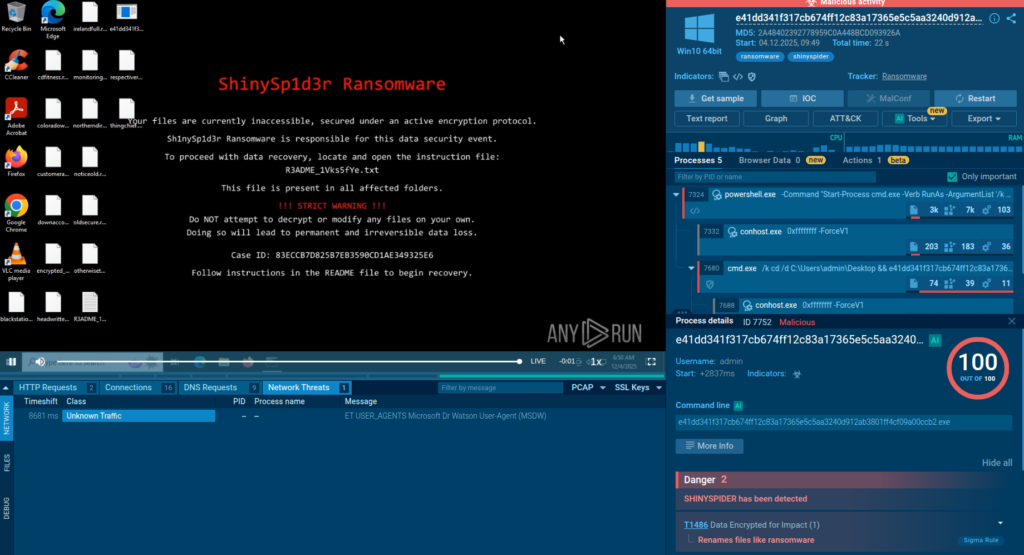
ANY.RUN is wrapping up 2025 with updates that take pressure off your SOC and help your team work faster. You can now get AI‑generated Sigma rules, track threats by industry and region, and detect new campaigns with better speed and accuracy.
Let’s see what these improvements bring to your security stack.
Product Updates
Industry & Geo Threat Landscape in TI Lookup
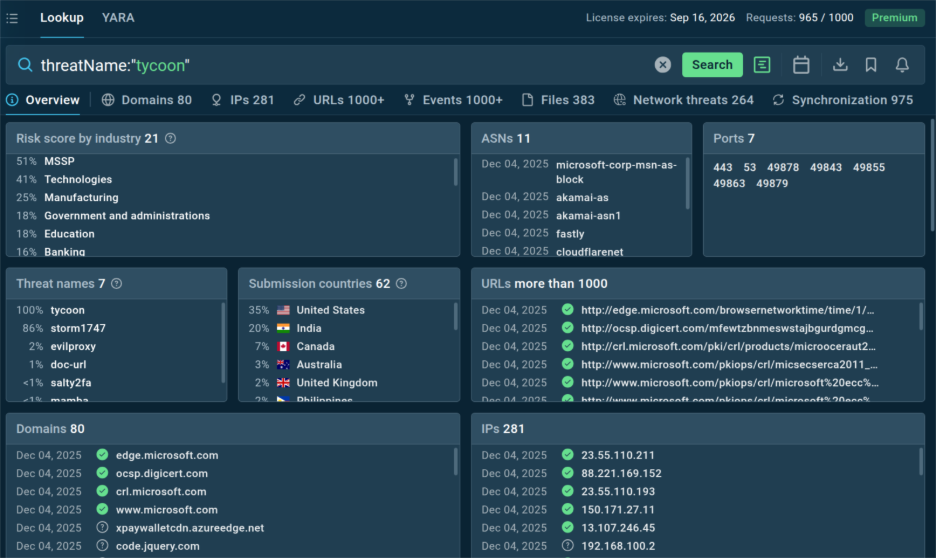
TI Lookup now gives every indicator extra context showing which industries and countries are linked to the threat of your industry and where similar activity is trending. It’s an easy way to see whether a threat actually affects your business or if it’s just background noise.
Built on live data from more than 15,000 organizations, this update helps your team tighten detection focus and reduce blind spots:
- See what matters first: Identify threats targeting your market or region so you can prioritize high‑risk activity.
- Triage faster: Skip irrelevant alerts and go straight to the ones that match your exposure.
- Work with better insight: Use targeted intelligence to guide hunts, automate enrichment, and improve MTTD.
With TI Lookup, you spot threats earlier, respond faster, and keep your attention where it counts.
AI Sigma Rules in ANY.RUN Sandbox
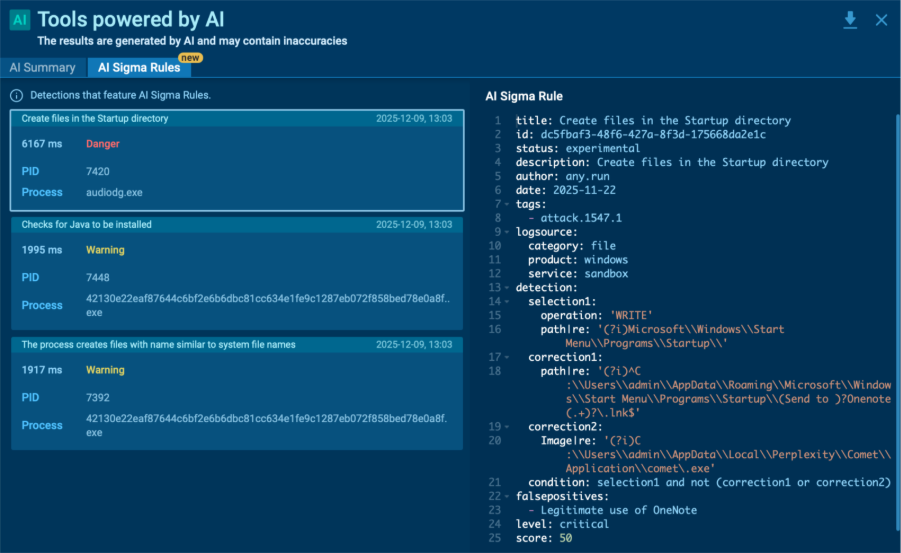
The new AI Sigma Rules feature in the Interactive Sandbox turns your confirmed detections into ready‑to‑use Sigma rules automatically. Instead of spending hours writing them by hand, you can now take the rule straight from the sandbox and add it to your SIEM or SOAR in seconds.
The rules are created from the same processes, files, and network events you see in the sandbox, so they stay closely tied to real attacker behavior. That means better accuracy and quicker response without extra effort.
Here’s what you gain:
- Less manual work: Every confirmed threat instantly becomes a reusable detection rule.
- Better coverage: Each investigation now improves how your SOC spots similar attacks later.
- Faster action: Analysts spend less time writing rules and more time acting on real signals.
Threat Coverage Updates
In December, our detection team rolled out another wave of coverage improvements with:
- 86 new behavior signatures
- 13 new YARA rules
- 1,686 new Suricata rules
These updates enhance phishing detection, expand coverage of stealers, loaders, and RATs, and clean up false positives across multi‑stage attacks.
New Behavior Signatures
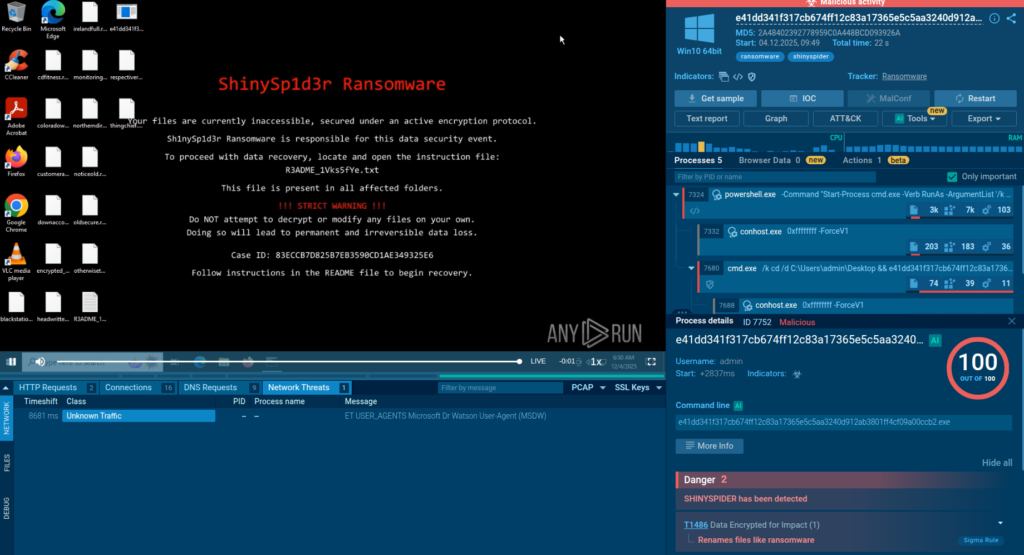
Fresh signatures add visibility into persistence, lateral movement, and abuse of system tools seen across mixed environments.
Highlighted families include:
These detections help analysts catch miner and loader activity earlier and recognize evasion tricks like rundll32 abuse or PowerShell obfuscation.
New YARA Rules
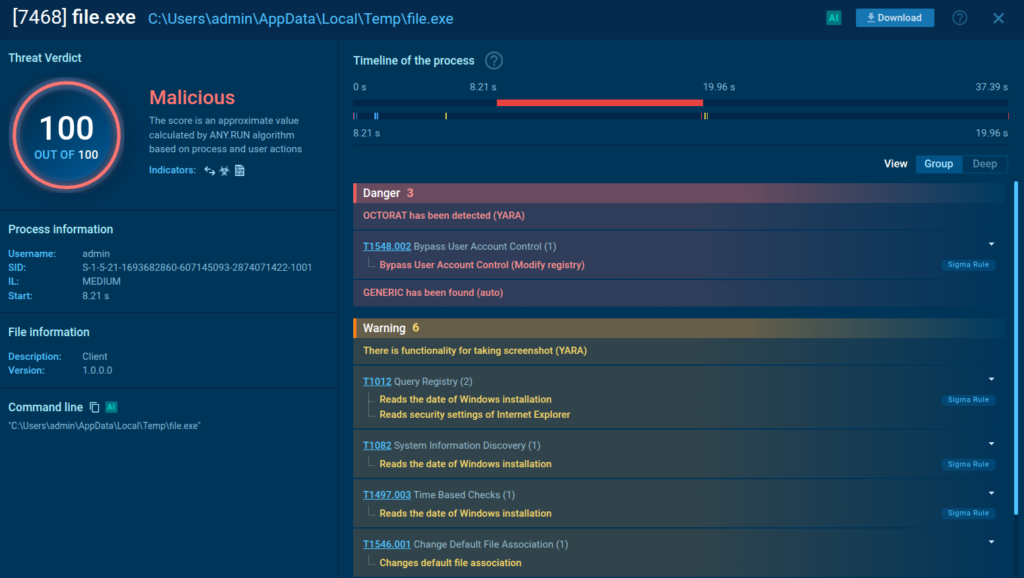
We added 13 YARA rules to improve detection across new malware strains and living‑off‑the‑land tools.
Highlighted families are STEAL1, SANTASTEALER, UNIXSTEALER, OCTORAT, DonutLoader.
These cover credential theft, modular loaders, and dual‑use administrative tools to ensure better coverage for both Windows and Linux‑based systems.
New Suricata Rules
We’ve added 1,686 Suricata rules targeting phishing, botnet activity, and evasive network behaviors often missed by standard IDS.
Together, these bring better coverage of C2 traffic, phishing domains, and low‑signal campaign infrastructure.
Businesses that are constantly being bombarded by hundreds of hacker attacks daily can upgrade their proactive defense with ANY.RUN’s Threat Intelligence Feeds.

Powered by sandbox analyses of the latest malware & phishing samples across 15K SOCs, they deliver fresh, real-time malicious network IOCs to numerous companies around the globe. Enriched with detailed sandbox reports, TI Feeds not only help you catch emerging threats early but also provide your analysts with actionable intelligence for fast remediation, boosting your detection rate and driving down the MTTR.
Threat Intelligence Reports
In December we published new TI Reports summarizing late‑year activity:
- End of Year Phishing (Available as part of the TI Lookup Premium subscription)
Each brief distills TTPs, campaigns, and IOCs from live submissions to help SOC teams anticipate what’s next.
About ANY.RUN
ANY.RUN powers SOCs at more than 15,000 organizations, giving them faster visibility into live threats through interactive sandboxing and cloud‑based intelligence.
Our Interactive Sandbox lets you analyze Windows, Linux, and Android samples in real time, watch the execution flow second‑by‑second, and pull IOCs instantly, no installs, no waiting. Combined with Threat Intelligence Lookup and Threat Intelligence Feeds, you get a single workflow built to speed up investigation, cut MTTD and MTTR, and keep your SOC focused on the right threats.
Start 2026 with faster detection, better threat intel, and less noise.
Request trial of ANY.RUN’s products for your SOC.