好的,我现在需要帮用户总结一篇文章的内容,控制在100字以内。首先,我得仔细阅读文章,抓住主要信息。 文章讲的是一个NPM包“Lotusbail”被用来窃取WhatsApp的账号信息。这个包下载量超过5.6万次,已经存在六个月了。它伪装成合法的Baileys库,拦截用户的凭证、消息、联系人和媒体,并加密后发送出去。攻击者还能通过硬编码的配对码获取持久访问权限,即使卸载包后仍然有效。此外,这个包还用了27种反调试陷阱来隐藏自己的行为。 接下来,我需要把这些要点浓缩到100字以内。重点包括:NPM包名称、下载量、窃取信息的方式、伪装成合法库、加密数据、持久访问权限以及反调试机制。 最后,组织语言确保简洁明了,直接描述内容,不使用总结性的开头。 </think> 一个NPM包“Lotusbail”伪装成合法的WhatsApp Web API库,在六个月内被下载超5.6万次。该包窃取用户凭证和数据,并安装后门。它通过加密数据并隐藏服务器细节来掩盖活动,甚至在卸载后仍保持访问权限。研究人员指出传统安全措施难以检测此类复杂供应链攻击。 2025-12-27 09:40:47 Author: securityaffairs.com(查看原文) 阅读量:9 收藏
NPM package with 56,000 downloads compromises WhatsApp accounts
Pierluigi Paganini
December 27, 2025

An NPM package with over 56,000 downloads stole WhatsApp credentials, hid its activity, and installed a backdoor.
Koi Security researchers warned that the NPM package ‘Lotusbail’, a WhatsApp Web API library and fork of ‘Baileys’, has been stealing users’ credentials and data.
The package has been available for six months and has had over 56,000 downloads. Lotusbail supports sending and receiving WhatsApp messages, wrapping the legitimate WebSocket client so all messages pass through it first, enabling the malicious capture of information.
The Lotusbail npm package works as a fully functional WhatsApp API, making it hard to detect because it is based on the legitimate Baileys library. It wraps WhatsApp’s WebSocket client, intercepting credentials, messages, contacts, and media while continuing normal operations.
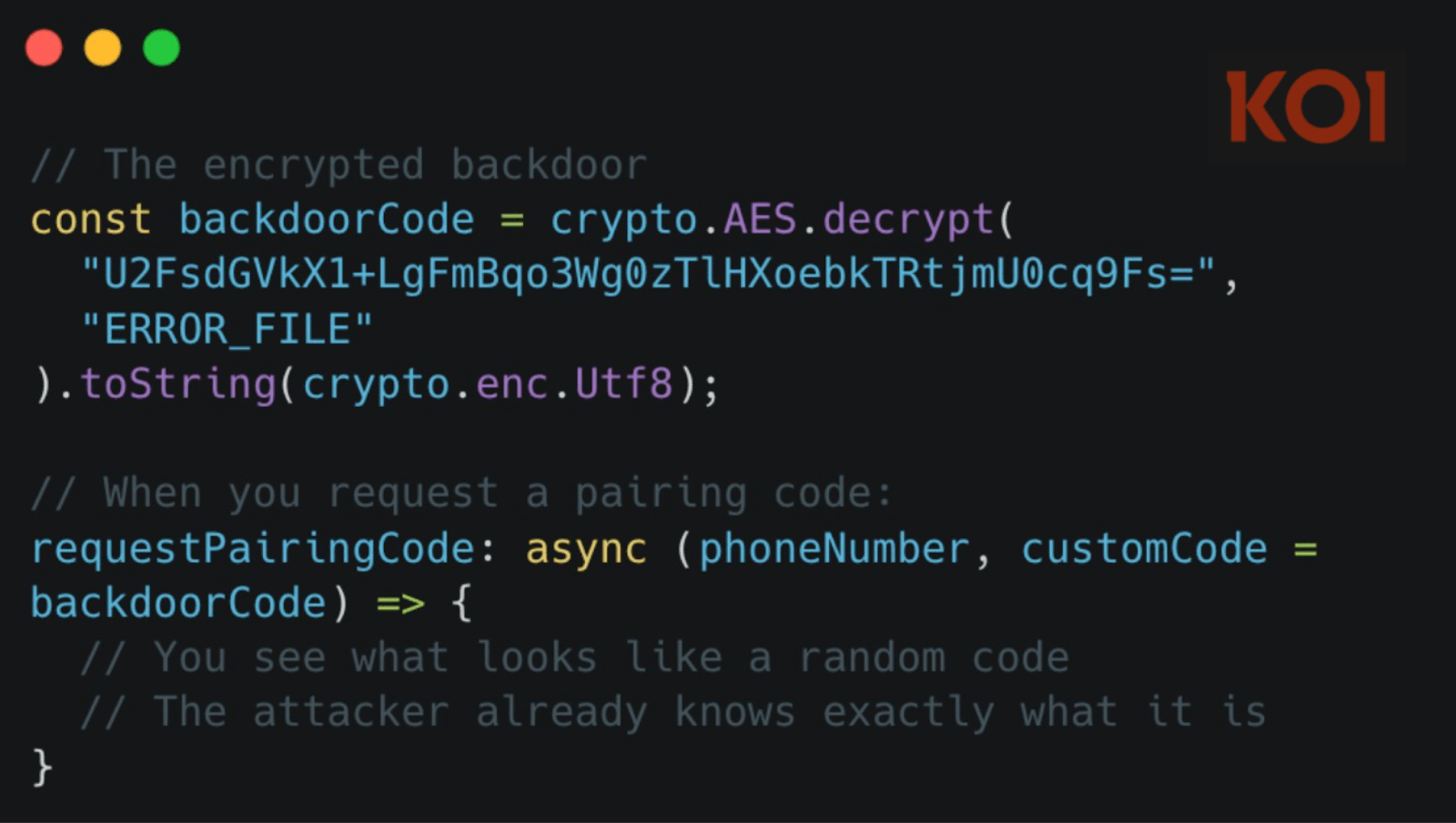
All stolen data is encrypted with custom RSA before exfiltration, using heavily obfuscated, hidden server details. The malware also hijacks WhatsApp’s device pairing process with a hardcoded code, secretly linking the attacker’s device to the victim’s account.
“The malware hijacks this process with a hardcoded pairing code. The code is encrypted with AES and hidden in the package” reads the report published by Koi Security

“This means the threat actor has a key to your WhatsApp account. When you use this library to authenticate, you’re not just linking your application – you’re also linking the threat actor’s device. They have complete, persistent access to your WhatsApp account, and you have no idea they’re there.
The threat actor can read all your messages, send messages as you, download your media, access your contacts – full account control. “
Even after uninstalling the package, attacker access persists until devices are manually unlinked.
The package uses 27 anti-debugging traps that freeze execution when analysis tools are detected, checking for debuggers and sandboxes. The attackers even labeled malicious code sections with comments, showing a highly professional, well-organized approach to a sophisticated supply chain attack.
“Traditional security doesn’t catch this. Static analysis sees working WhatsApp code and approves it. Reputation systems see 56,000 downloads and trust it. The malware hides in the gap between “this code works” and “this code only does what it claims.” concludes the report. “Catching sophisticated supply chain attacks requires behavioral analysis – watching what packages actually do at runtime. When a WhatsApp library implements custom RSA encryption and includes 27 anti-debugging traps, those are signals. But you need systems watching for them.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, malware)
如有侵权请联系:admin#unsafe.sh