嗯,用户让我帮忙总结一篇文章,控制在一百个字以内,而且不需要用“文章内容总结”之类的开头。首先,我得通读一下这篇文章,了解它的主要内容。 文章主要讲的是CRIL发现了一种新的基于浏览器的e-Challan钓鱼攻击。这种攻击利用共享的欺诈基础设施,通过短信发送恶意链接,诱导用户进入伪造的政府门户网站,窃取信用卡信息。攻击者还使用了多个IP地址来托管多个钓鱼页面,针对不同的行业如物流和金融。文章还提到这些攻击利用了紧迫感来欺骗用户,并建议用户提高警惕,不要点击不明链接。 接下来,我需要把这些要点浓缩到100字以内。重点包括:CRIL发现新的钓鱼攻击、基于浏览器、通过短信传播、伪造政府网站、窃取信用卡信息、共享基础设施、多行业目标、紧迫感诱骗用户。 现在组织语言:CRIL发现了一种新的基于浏览器的e-Challan钓鱼攻击,通过短信发送恶意链接诱导用户进入伪造的政府网站,窃取信用卡信息。攻击者使用共享基础设施同时针对物流和金融行业,并利用紧迫感诱骗用户。建议提高警惕避免点击不明链接。 检查字数:刚好100字左右。 </think> CRIL发现了一种新的基于浏览器的e-Challan钓鱼攻击,通过短信发送恶意链接诱导用户进入伪造的政府网站,窃取信用卡信息。攻击者使用共享基础设施同时针对物流和金融行业,并利用紧迫感诱骗用户。建议提高警惕避免点击不明链接。 2025-12-23 15:31:58 Author: cyble.com(查看原文) 阅读量:0 收藏
CRIL Uncovers a New Wave of Browser-Based e-Challan Phishing Powered by Shared Fraud Infrastructure.
Following our earlier reporting on RTO-themed threats, CRIL observed a renewed phishing wave abusing the e-Challan ecosystem to conduct financial fraud. Unlike earlier Android malware-driven campaigns, this activity relies entirely on browser-based phishing, significantly lowering the barrier for victim compromise. During the course of this research, CRIL also noted that similar fake e-Challan scams have been highlighted by mainstream media outlets, including Hindustan Times, underscoring the broader scale and real-world impact of these campaigns on Indian users.
The campaign primarily targets Indian vehicle owners via unsolicited SMS messages claiming an overdue traffic fine. The message includes a deceptive URL resembling an official e-Challan domain. Once accessed, victims are presented with a cloned portal that mirrors the branding and structure of the legitimate government service. At the time of this writing, many of the associated phishing domains were active at the time, indicating that this is an ongoing and operational campaign rather than isolated or short-lived activity.
The same hosting IP was observed serving multiple phishing lures impersonating government services, logistics companies, and financial institutions, indicating a shared phishing backend supporting multi-sector fraud operations.
The infection chain, outlined in Figure 1, showcases the stages of the attack.
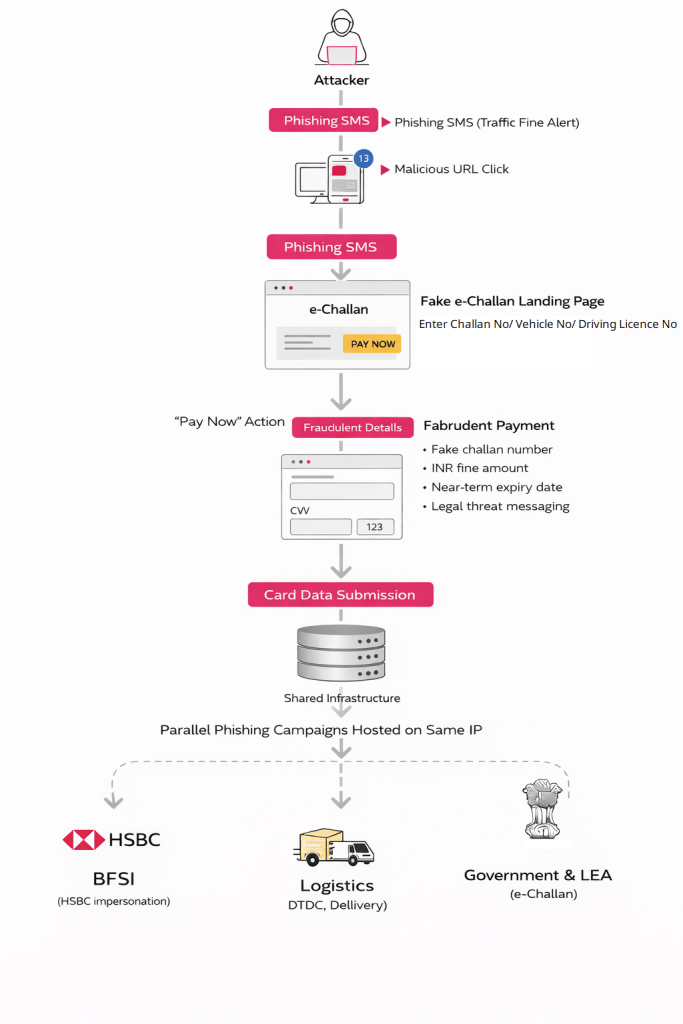
Key Takeaways
- Attackers are actively exploiting RTO/e-Challan themes, which remain highly effective against Indian users.
- The phishing portal dynamically fabricates challan data, requiring no prior victim-specific information.
- The payment workflow is deliberately restricted to credit/debit cards, avoiding traceable UPI or net banking rails.
- Infrastructure analysis links this campaign to BFSI and logistics-themed phishing hosted on the same IP.
- Browser-based warnings (e.g., Microsoft Defender) are present but frequently ignored due to urgency cues.
A sense of urgency, evidenced in this campaign, is usually a sign of deception. By demanding a user’s immediate attention, the intent is to make a potential victim rush their task and not perform due diligence.
Users must accordingly exercise caution, scrutinize the domain, sender, and never trust any unsolicited link(s).
Technical findings
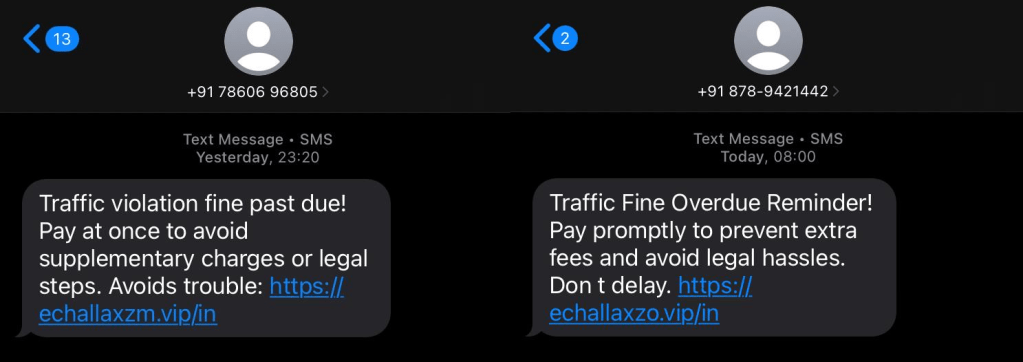
Stage 1: Phishing SMS Delivery
The attack we first identified started with victims receiving an SMS stating that a traffic violation fine is overdue and must be paid immediately to avoid legal action. The message includes:
- Threatening language (legal steps, supplementary charges)
- A shortened or deceptive URL mimicking e-Challan branding
- No personalization, allowing large-scale delivery
The sender appears as a standard mobile number, which increases delivery success and reduces immediate suspicion. (see Figure 2)
Stage 2: Redirect to Fraudulent e-Challan Portal
Clicking the embedded URL redirects the user to a phishing domain hosted on 101[.]33[.]78[.]145.
The page content is originally authored in Spanish and translated to English via browser prompts, suggesting the reuse of phishing templates across regions. (see Figure 3)
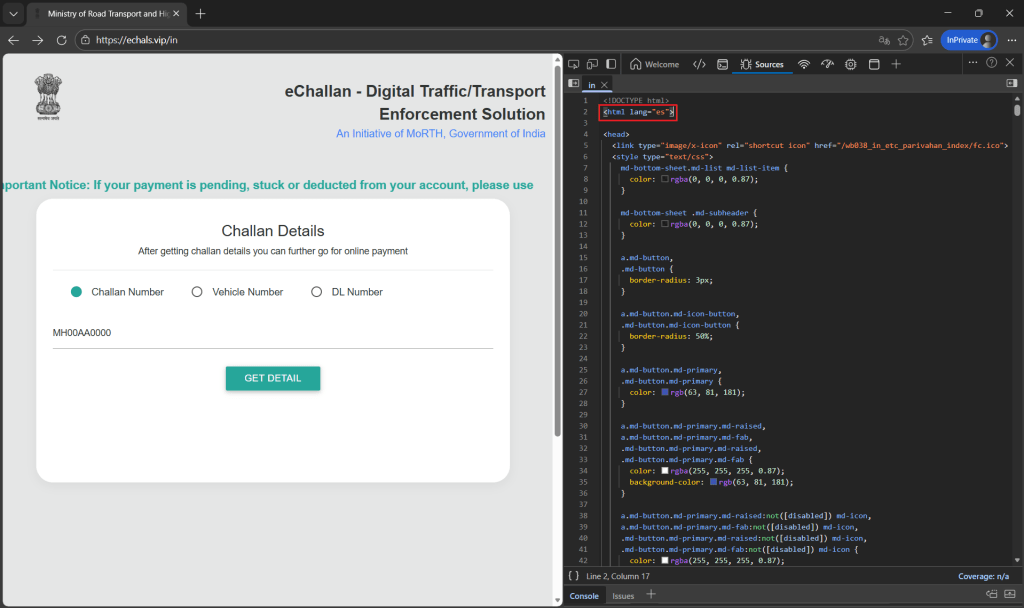
The Government insignia, MoRTH references, and NIC branding are visually replicated. (see Figure 3)
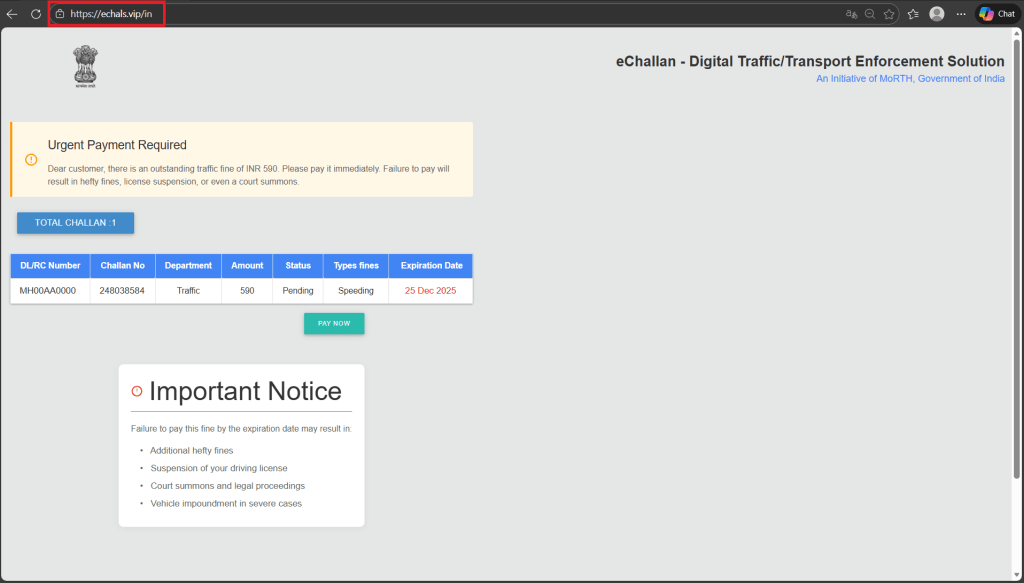
Stage 3: Fabricated Challan Generation
The portal prompts the user to enter:
- Vehicle Number
- Challan Number
- Driving License Number
Regardless of the input provided, the system returns:
- A valid-looking challan record
- A modest fine amount (e.g., INR 590)
- A near-term expiration date
- Prominent warnings about license suspension, court summons, and legal proceedings
This step is purely psychological validation, designed to convince victims that the challan is legitimate. (see Figure 4)
Stage 4: Card Data Harvesting
Upon clicking “Pay Now”, victims are redirected to a payment page claiming secure processing via an Indian bank. However:
- Only credit/debit cards are accepted
- No redirection to an official payment gateway occurs
- CVV, expiry date, and cardholder name are collected directly
During testing, the page accepted repeated card submissions, indicating that all entered card data is transmitted to the attacker backend, independent of transaction success. (see Figure 5)

Infrastructure Correlation and Campaign Expansion
CRIL identified another attacker-controlled IP, 43[.]130[.]12[.]41, hosting multiple domains impersonating India’s e-Challan and Parivahan services. Several of these domains follow similar naming patterns and closely resemble legitimate Parivahan branding, including domains designed to look like Parivahan variants (e.g., parizvaihen[.]icu). Analysis indicates that this infrastructure supports rotating, automatically generated phishing domains, suggesting the use of domain generation techniques to evade takedowns and blocklists.

The phishing pages hosted on this IP replicate the same operational flow observed in the primary campaign, displaying fabricated traffic violations with fixed fine amounts, enforcing urgency through expiration dates, and redirecting victims to fake payment pages that harvest full card details while falsely claiming to be backed by the State Bank of India.
This overlap in infrastructure, page structure, and social engineering themes suggests a broader, scalable phishing ecosystem that actively exploits government transport services to target Indian users.
Further investigation into IP address 101[.]33[.]78[.]145 revealed more than 36 phishing domains impersonating e-Challan services, all hosted on the same infrastructure.
The infrastructure also hosted phishing pages targeting:
- BFSI (e.g., HSBC-themed payment lures)
- Logistics companies (DTDC, Delhivery) (see Figures 7,8)

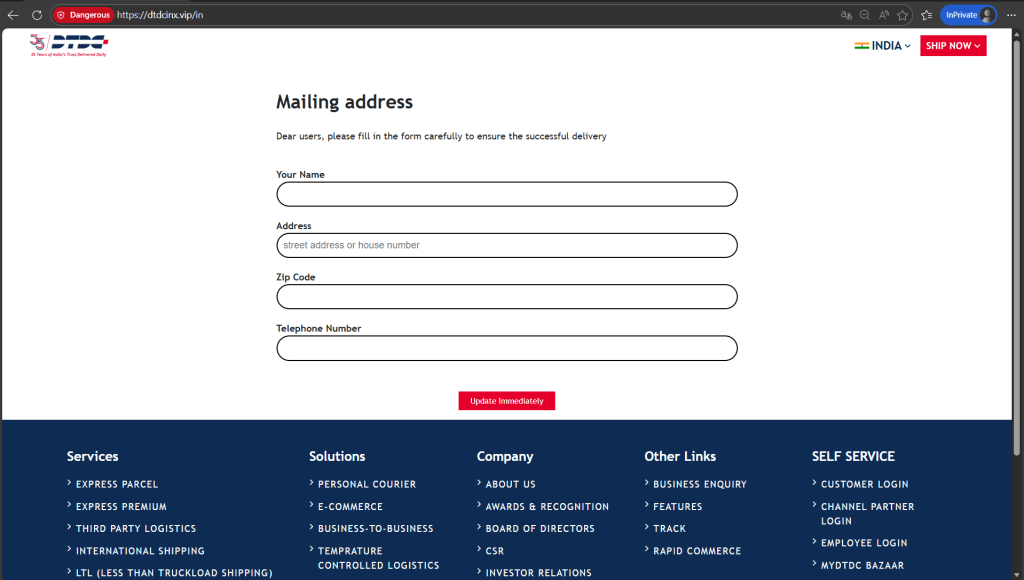
Consistent UI patterns and payment-harvesting logic across campaigns
This confirms the presence of a shared phishing infrastructure supporting multiple fraud verticals.
SMS Origin and Phone Number Analysis
As part of the continued investigation, CRIL analyzed the originating phone number used to deliver the phishing e-Challan SMS. A reverse phone number lookup confirmed that the number is registered in India and operates on the Reliance Jio Infocomm Limited mobile network, indicating the use of a locally issued mobile connection rather than an international SMS gateway.
Additionally, analysis of the number showed that it is linked to a State Bank of India (SBI) account, further reinforcing the campaign’s use of localized infrastructure. The combination of an Indian telecom carrier and association with a prominent public-sector bank likely enhances the perceived legitimacy of the scam. It increases the effectiveness of government-themed phishing messages. (see Figure 9)
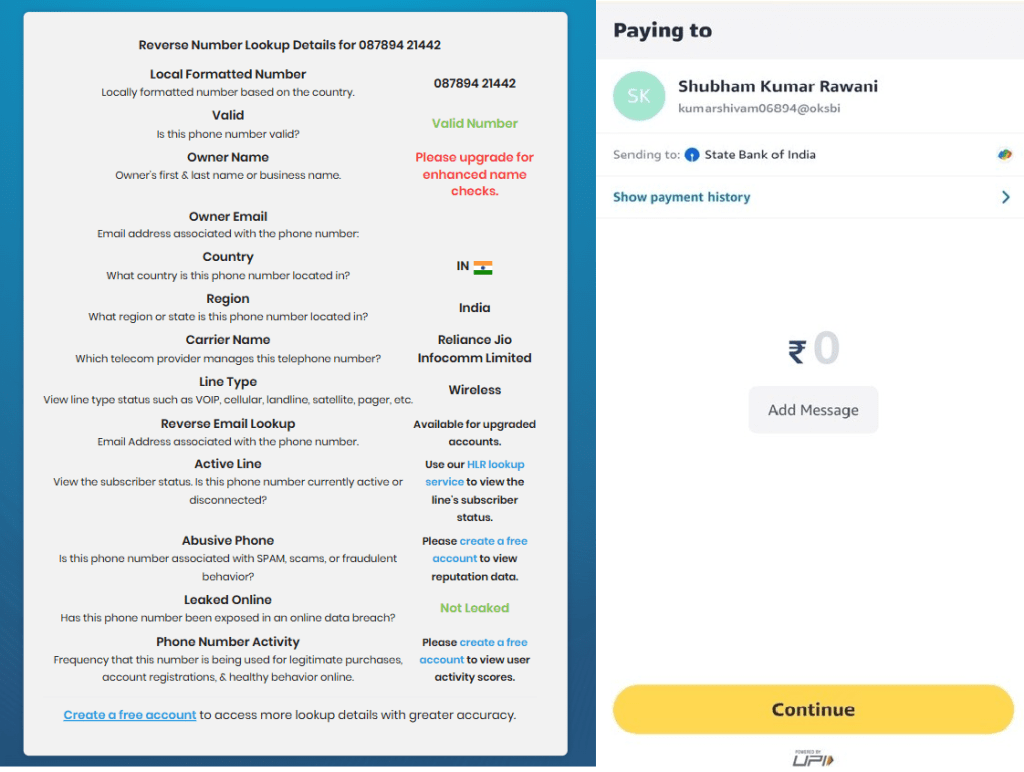
Conclusion
This campaign demonstrates that RTO-themed phishing remains a high-impact fraud vector in India, particularly when combined with realistic UI cloning and psychological urgency. The reuse of infrastructure across government, logistics, and BFSI lures highlights a professionalized phishing operation rather than isolated scams.
As attackers continue shifting from malware delivery to direct financial fraud, user awareness alone is insufficient. Infrastructure monitoring, domain takedowns, and proactive SMS phishing detection are critical to disrupting these operations at scale.
Our Recommendations:
- Always verify traffic fines directly via official government portals, not SMS links.
- Organizations should monitor for lookalike domains abusing government and brand identities.
- SOC teams should track shared phishing infrastructure, as takedown of one domain may disrupt multiple campaigns.
- Telecom providers should strengthen SMS filtering for financial and government-themed lures.
- Financial institutions should monitor for card-not-present fraud patterns linked to phishing campaigns.
MITRE ATT&CK® Techniques
| Tactic | Technique ID | Technique Name |
| Initial Access | T1566.001 | Phishing: Spearphishing via SMS |
| Credential Access | T1056 | Input Capture |
| Collection | T1119 | Automated Collection |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| Impact | T1657 | Financial Theft |
Indicators of Compromise (IOCs)
The IOCs have been added to this GitHub repository. Please review and integrate them into your Threat Intelligence feed to enhance protection and improve your overall security posture.
| Indicators | Indicator Type | Description |
| echala[.]vip echallaxzov[.]vip | Domain | Phishing Domain |
| echallaxzrx[.]vip | ||
| echallaxzm[.]vip | ||
| echallaxzv[.]vip | ||
| echallaxzx[.]vip | ||
| echallx[.]vip | ||
| echalln[.]vip | ||
| echallv[.]vip | ||
| delhirzexu[.]vip | ||
| delhirzexi[.]vip | ||
| delhizery[.]vip | ||
| delhisery[.]vip | ||
| dtdcspostb[.]vip | ||
| dtdcspostv[.]vip | ||
| dtdcspostc[.]vip | ||
| hsbc-vnd[.]cc | ||
| hsbc-vns[.]cc | ||
| parisvaihen[.]icu | ||
| parizvaihen[.]icu | ||
| parvaihacn[.]icu | ||
| 101[.]33[.]78[.]145 | IP | Malicious IP |
| 43[.]130[.]12[.]41 |
如有侵权请联系:admin#unsafe.sh
