
嗯,用户让我总结一下这篇文章的内容,控制在100个字以内,而且不需要用“文章内容总结”或者“这篇文章”这样的开头。直接写描述就行。 首先,我需要通读整篇文章,抓住主要信息。文章讲的是ASUS Live Update的一个漏洞,编号是CVE-2025-59374。这个漏洞被报道为最近或正在进行的攻击,但实际上它是一个历史上的供应链攻击事件,发生在2018-2019年的“ShadowHammer”行动中。 接下来,文章提到这个漏洞被添加到CISA的已知被利用漏洞(KEV)目录中,但并不意味着这是一个新出现的威胁。受影响的软件ASUS Live Update已经到了生命周期末期(EoL),在2021年10月就结束了支持。因此,目前没有支持的产品受到影响。 然后,文章指出虽然ASUS在2025年12月更新了他们的FAQ页面,但并没有提供新的补丁或解决方案。FAQ中的截图和建议都是基于2019年的信息,并没有新的内容。CISA也表示,将这个漏洞加入KEV目录并不意味着当前有活跃的攻击活动。 最后,作者建议用户确保他们使用的是最新版本的软件,并提醒安全团队在处理与CISA相关的CVE时要谨慎判断其紧迫性,特别是对于已经退役的软件或早已解决的事件。 总结一下:文章主要讲述了ASUS Live Update的一个历史漏洞被重新提及的情况,并解释了为什么这并不构成新的威胁。 </think> ASUS Live Update的一个历史漏洞(CVE-2025-59374)被添加到CISA的已知被利用漏洞目录中。该漏洞源于2018-2019年的供应链攻击(ShadowHammer),影响的是已停止支持的软件版本。尽管最近更新了相关文档和FAQ页面,但并无新风险或补丁要求。当前无受支持设备受影响。 2025-12-22 19:0:37 Author: www.bleepingcomputer.com(查看原文) 阅读量:4 收藏

An ASUS Live Update vulnerability tracked as CVE-2025-59374 has been making the rounds in infosec feeds, with some headlines implying recent or ongoing exploitation.
The CVE documents a historic supply-chain attack in an End-of-Life (EoL) software product, not a newly emerging threat.
Not all CISA KEVs signal urgency
Recent coverage of CVE-2025-59374 has framed the issue as a newly relevant security risk following its addition to CISA's Known Exploited Vulnerabilities (KEV) catalog.
A closer look, however, shows the reality is much more nuanced.
The CVE documents the 2018-2019 "ShadowHammer" supply-chain attack, in which maliciously modified ASUS Live Update binaries were selectively delivered to a small number of targeted systems.
The CVE entry for the compromise, now-rated a 9.3 (Critical) on the CVSS scale, states:
"UNSUPPORTED WHEN ASSIGNED" Certain versions of the ASUS Live Update client were distributed with unauthorized modifications introduced through a supply chain compromise. The modified builds could cause devices meeting specific targeting conditions to perform unintended actions. Only devices that met these conditions and installed the compromised versions were affected. The Live Update client has already reached End-of-Support (EOS) in October 2021, and no currently supported devices or products are affected by this issue.
The 'unsupported when assigned' text already suggests that the CVE was filed for an EoL product.
The primary vendor advisory linked to in the CVE entry is from 2019. This advisory additionally links to an FAQ: https://www.asus.com/support/faq/1018727/ bearing the last updated timestamp, 2025/12/06 20:09.
Note, however, this FAQ 1018727 link existed in that spot back in 2019 when the advisory was first published.
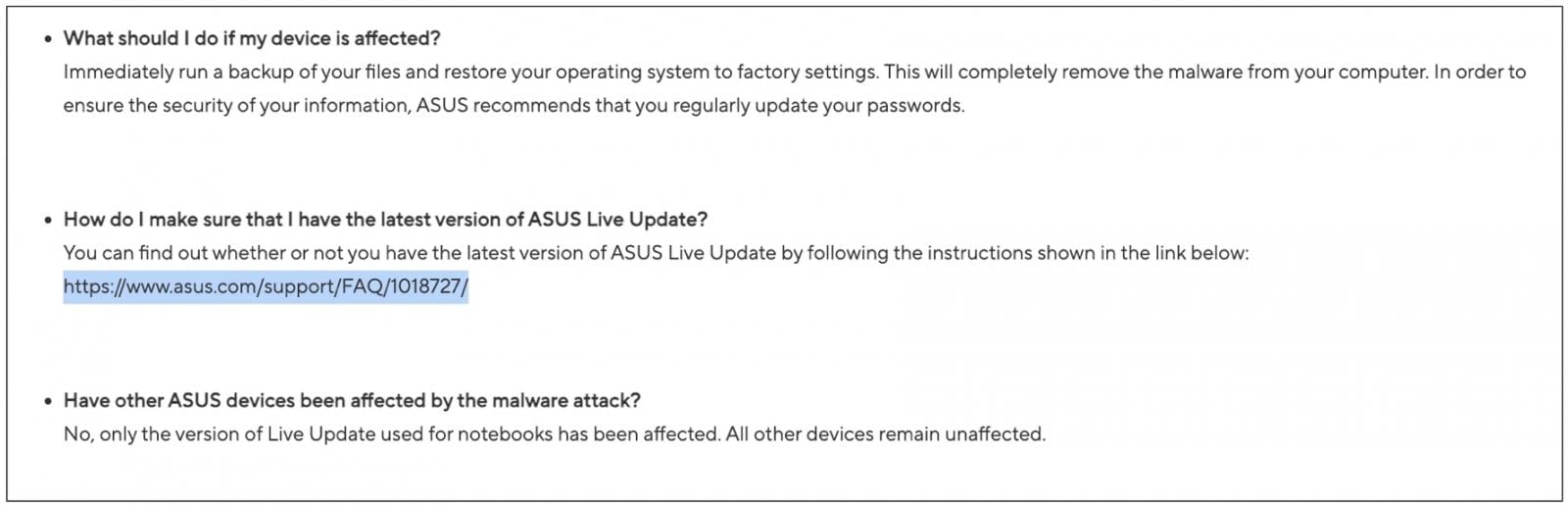
As seen by BleepingComputer, the FAQ page does not provide the first publication timestamp metadata. Rather, it has simply been updated this month and shows the aforementioned December 6th date on the page.

(BleepingComputer)
The archived pages help us establish the purpose of the page, and why recent updates made to the page do not necessarily mean a renewed risk from the 2019 issue.
The FAQ entry appears to be ASUS' placeholder page, periodically revised to provide information on the upgrade path, i.e. the latest version users should adopt for the vendor's Live Update utility.
Furthermore, the page continues to display (older) remediation guidance with screenshots bearing 2019 dates:
To get more information about the 2025 CVE assignment, BleepingComputer reached out to ASUS well in advance of publishing but we did not hear back.
We additionally reached out to CISA to understand what prompted the CVE's addition to the KEV catalog.
CISA declined to provide additional comment, instead pointing BleepingComputer to language in Binding Operational Directive 22-01, which notes:
"Addition of a vulnerability to the KEV catalog does not indicate that CISA is observing current active exploitation. If there is accurate reporting of active exploitation, any vulnerability, despite its age, can qualify for KEV catalog addition"
Taken together, the evidence suggests the CVE assignment reflects a retrospective classification effort, formally documenting a well-known attack that predated CVE issuance.
Practical guidance for users
You should still ensure that you have the latest, patched version of the product.
According to the CVE entry, the affected software, ASUS Live Update, reached End-of-Support (EOS) in October 2021, with "no currently supported devices or products are affected by this issue."
The updated ASUS FAQ page from this month, however, contradicts this wording, implying that the support definitively ended on December 4, 2025:
"We announced end of support for ASUS LiveUpdate on 2025/12/4, the last version is 3.6.15."
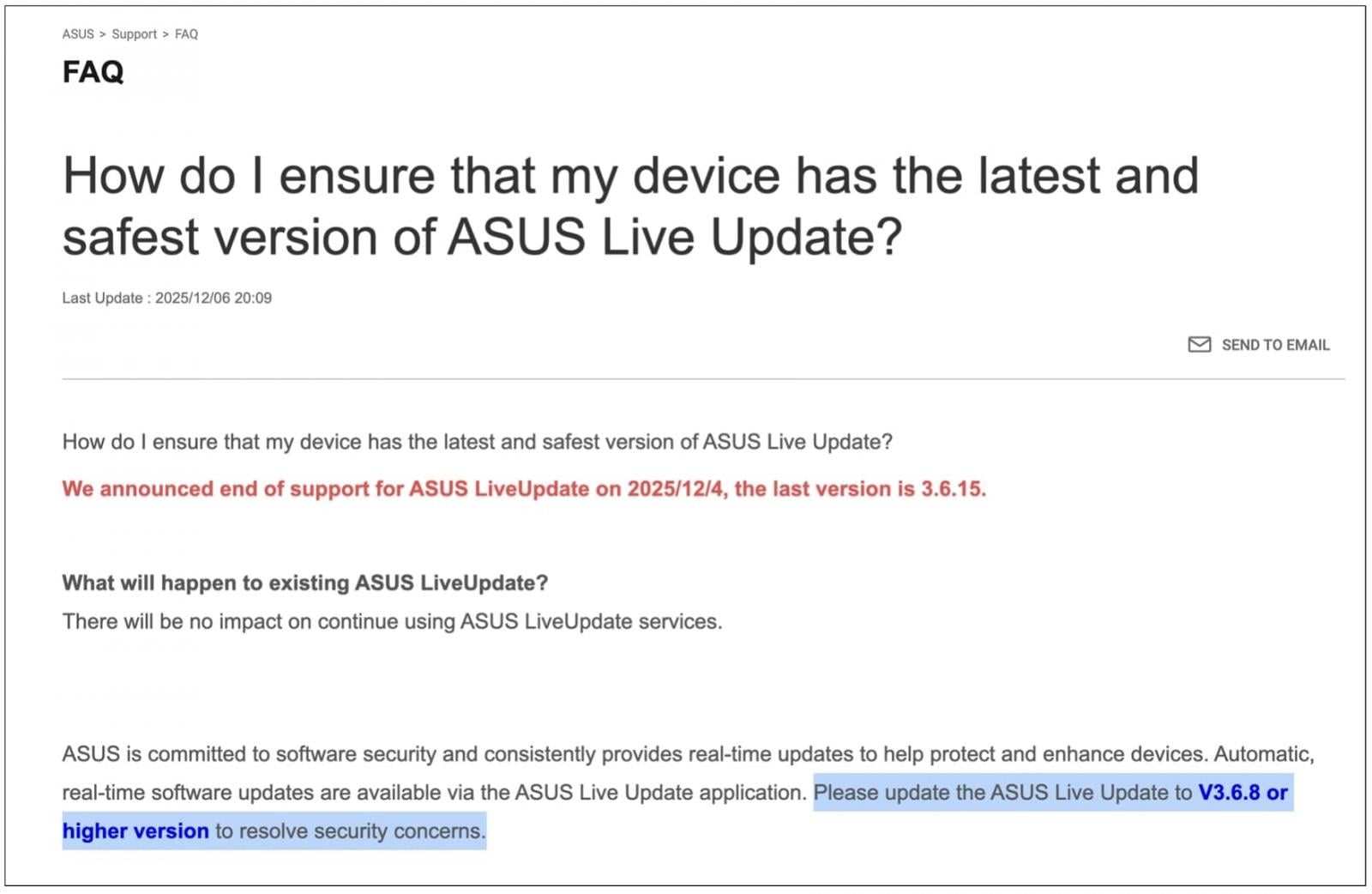
(BleepingComputer)
Earlier copies (2019-22) of the FAQ recommended upgrading to "V3.6.8 or higher version to resolve security concerns," as a fix for the issue was implemented in that version at the time. That dated advice has been left as-is on the updated FAQ from this month.
The release 3.6.15, however, is now listed as the "last version." That version apparently existed as early as March 2024 if not before, meaning there is no new urgency to upgrade—contrary to the usual call-to-action following recent supply chain compromises.
CVE-2025-59374 formalizes a well-documented historical attack. FAQ updates, older remediation guidance, the utility's latest release, and CISA context show the page was updated for documentation purposes, not to address a new exploit, impose patching requirements, or signal immediate risk.
Security teams should therefore be mindful when treating CISA-linked CVEs as urgent, particularly for retired software or long-resolved incidents.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.
如有侵权请联系:admin#unsafe.sh

