
嗯,用户让我帮忙总结一篇文章,控制在100字以内,而且不需要用“文章内容总结”这样的开头。首先,我需要通读整篇文章,抓住主要信息。 文章主要讲的是2026年的网络安全威胁和检测软件的重要性。里面提到了各种数据,比如网络犯罪造成的损失高达10.5万亿美元,威胁检测软件的作用,以及Seceon公司的解决方案。 接下来,我需要提取关键点:威胁检测软件的功能、2026年的威胁数据、为什么需要这种软件、关键功能以及Seceon的优势。然后把这些点浓缩成简短的句子。 要注意控制在100字以内,所以要简洁明了。可能的结构是先总述威胁情况,再讲解决方案及其重要性。 最后检查一下是否符合要求,没有使用开头的模板,并且信息准确全面。 </think> 2026年网络安全威胁加剧,企业需依赖威胁检测软件实时识别并应对复杂攻击。该软件通过AI、机器学习和行为分析技术,主动防御恶意软件、钓鱼攻击、供应链风险等多重威胁。部署此类工具可显著降低数据泄露成本并提升业务连续性。 2025-12-22 11:58:37 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
The cybersecurity landscape in 2026 presents unprecedented challenges for organizations across all industries. With cybercrime damages projected to exceed $10.5 trillion annually, enterprises face sophisticated threats from attackers leveraging AI-powered tools, advanced persistent threats, and multi-vector attack strategies. Effective threat detection is no longer optional it is a critical business imperative for maintaining operational continuity and competitive advantage.
What is Threat Detection Software?
Threat detection software is a comprehensive security solution designed to identify, analyze, and respond to potential cybersecurity threats in real-time. These advanced systems continuously monitor network traffic, user behavior, system activities, and data flows to detect anomalies that could indicate a security breach or cyberattack. By leveraging artificial intelligence, machine learning, and behavioral analytics, modern threat detection platforms can identify both known and emerging threats before they cause significant damage.
Unlike traditional antivirus software that relies primarily on signature-based detection, contemporary threat detection solutions employ multiple layers of security intelligence to provide proactive protection against the ever-changing threat landscape.
The 2026 Threat Landscape: By the Numbers
Understanding the current threat environment is crucial for appreciating why robust threat detection is non-negotiable:
- 93% of organizations experienced at least one cybersecurity incident in 2025, with that number expected to reach 97% in 2026
- Average data breach cost: $4.88 million in 2025, projected to exceed $5.2 million in 2026
- Ransomware attacks occur every 11 seconds globally, with average ransom demands surpassing $2.5 million
- 68% of breaches involve human error, highlighting the need for automated threat detection
- 277 days: Average time to identify and contain a breach without advanced detection systems
- AI-powered attacks have increased by 385% year-over-year, outpacing traditional security measures
- Supply chain attacks increased by 420% in 2025, making third-party risk monitoring critical
95% of cybersecurity breaches are caused by human error, making behavioral analytics essential

Why Your Organization Needs Threat Detection Software in 2026
Cybersecurity incidents result in significant financial, operational, and reputational consequences that extend well beyond initial breach costs. Organizations must implement comprehensive threat detection to address multiple critical requirements:
Financial Protection: With breach costs averaging $5.2 million and rising, the ROI on threat detection software is clear. Organizations with advanced detection capabilities reduce breach costs by an average of $1.76 million compared to those without.
Compliance Requirements: Industries such as healthcare, finance, and retail face strict regulatory requirements, including GDPR, HIPAA, PCI-DSS, SOC 2, and the new AI Security Framework regulations introduced in 2025. Non-compliance penalties now average $14.82 million per incident. Threat detection software helps organizations maintain compliance and avoid hefty penalties.
Business Continuity: Ransomware attacks and system compromises can halt operations for days or weeks, with 60% of small businesses closing within six months of a major breach. Real-time threat detection minimizes downtime by identifying and neutralizing threats before they escalate.
Intellectual Property Protection: For businesses that rely on proprietary information, trade secrets, or innovative products, threat detection safeguards valuable intellectual property from corporate espionage and theft. Industrial espionage costs businesses over $600 billion annually.
Reputation Management: 83% of consumers say they’ll stop doing business with a company that experiences a data breach, making threat prevention essential for brand preservation.
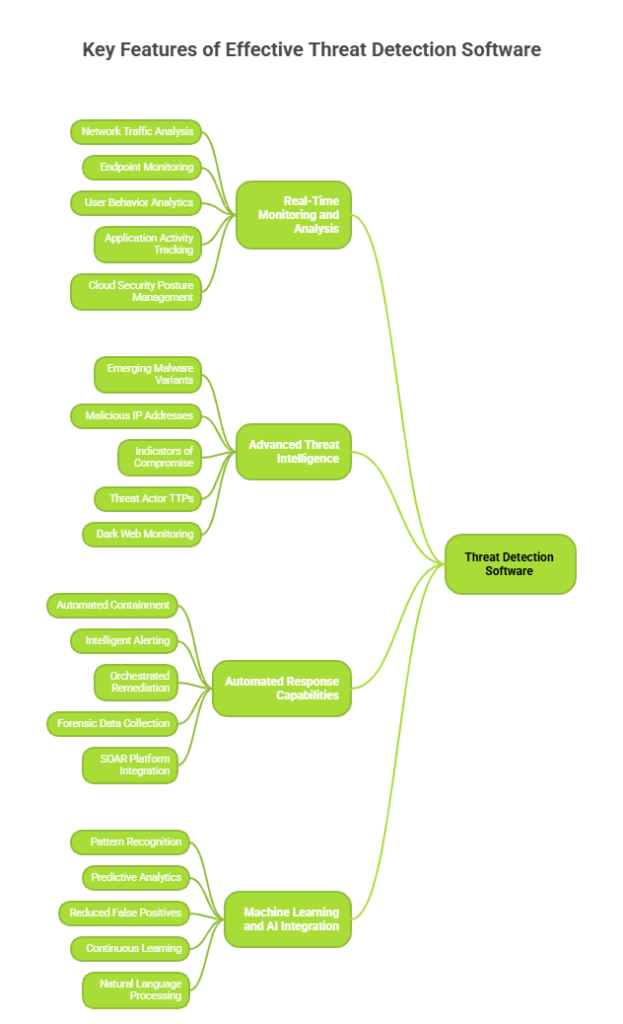
Key Features of Effective Threat Detection Software
When evaluating threat detection solutions, understanding the core capabilities that separate robust platforms from basic security tools is crucial:
Real-Time Monitoring and Analysis
Modern threat detection operates 24/7/365, continuously scanning your digital environment for suspicious activities. This includes:
- Network traffic analysis that identifies unusual data flows or unauthorized access attempts with 99.7% accuracy
- Endpoint monitoring across all devices connected to your network, including computers, mobile devices, IoT equipment, and cloud workloads
- User behavior analytics (UBA) that establishes baseline patterns and flags deviations indicating compromised credentials or insider threats
- Application activity tracking to detect malicious code execution or unauthorized software installations
- Cloud security posture management for hybrid and multi-cloud environments
Advanced Threat Intelligence
Leading platforms integrate global threat intelligence feeds that provide up-to-date information about:
- Emerging malware variants and attack vectors discovered within the last 24 hours
- Known malicious IP addresses, domains, and threat actor infrastructure
- Indicators of compromise (IoCs) are shared across the cybersecurity community in real-time
- Tactics, techniques, and procedures (TTPs) used by threat actors and APT groups
- Dark web monitoring for leaked credentials and planned attacks
Automated Response Capabilities
Speed is critical in threat mitigation. Organizations that contain breaches in under 200 days save an average of $1.12 million. The best threat detection software includes:
- Automated containment that isolates affected systems to prevent lateral movement within seconds
- Intelligent alerting that prioritizes threats based on severity, exploitability, and potential impact
- Orchestrated remediation that executes predefined response workflows automatically
- Forensic data collection for post-incident analysis and investigation
- Integration with SOAR platforms for comprehensive incident response
Machine Learning and AI Integration
Artificial intelligence transforms threat detection from reactive to predictive, with AI-driven systems detecting threats 60% faster than human analysts:
- Pattern recognition that identifies zero-day exploits and previously unknown threats with 95% accuracy
- Predictive analytics that forecast potential attack vectors based on historical data
- Reduced false positives through intelligent correlation of security events (averaging 85% reduction)
- Continuous learning that adapts to your organization’s unique environment
- Natural language processing for analyzing threat reports and security advisories
Types of Threats Detected by Modern Security Software
Understanding what threats your software should detect helps you evaluate solutions effectively:
Malware and Ransomware: Detecting malicious software before it encrypts files or steals data, including trojans, worms, spyware, fileless malware, and crypto-lockers. Ransomware-as-a-Service (RaaS) attacks have increased by 267% in 2025.
Phishing and Social Engineering: Identifying fraudulent communications designed to trick employees into revealing credentials or downloading malicious attachments. Spear-phishing success rates have increased to 36% in 2026.
Advanced Persistent Threats (APTs): Discovering sophisticated, long-term intrusions where attackers establish footholds and gradually exfiltrate sensitive information over weeks or months.
Insider Threats: Monitoring for malicious or negligent employee activities that compromise security. Insider threats account for 34% of all data breaches and cost an average of $16.2 million per incident.
DDoS Attacks: Detecting distributed denial-of-service attempts that overwhelm systems with traffic to disrupt operations, with attacks now reaching 3.47 Tbps.
SQL Injection and Web Application Attacks: Identifying attempts to exploit vulnerabilities in web applications and databases, which account for 43% of application-layer attacks.
Lateral Movement: Catching attackers as they move through your network after initial compromise, preventing them from reaching critical assets.
AI-Powered Attacks: Detecting sophisticated attacks that use machine learning to evade traditional security measures and adapt in real-time.
Supply Chain Compromises: Identifying threats introduced through third-party vendors, software updates, and partner connections.
Implementation Best Practices for Threat Detection Software
Successfully deploying threat detection requires strategic planning and execution:
Comprehensive Asset Inventory
Begin by cataloging all digital assets, including servers, workstations, mobile devices, cloud resources, containerized applications, and IoT devices. Organizations with complete asset visibility detect breaches 52% faster. Understanding your attack surface is fundamental to effective monitoring.
Integration with Existing Security Stack
Your threat detection platform should work seamlessly with:
- Next-generation firewalls and intrusion prevention systems
- Security information and event management (SIEM) solutions
- Identity and access management (IAM) tools
- Endpoint detection and response (EDR) systems
- Cloud security platforms (CSPM, CWPP)
- Extended detection and response (XDR) frameworks
Customization and Tuning
Generic configurations rarely provide optimal protection. Organizations that customize their detection rules experience 73% fewer false positives. Invest time in:
- Defining baseline behaviors for your specific environment
- Establishing appropriate alert thresholds to minimize false positives
- Creating custom detection rules for industry-specific threats
- Configuring automated response playbooks aligned with your incident response plan
- Implementing risk-based prioritization
Regular Updates and Maintenance
Threat landscapes evolve constantly, with an average of 560,000 new malware variants detected daily. This requires:
- Continuous updates to threat intelligence feeds
- Regular review and refinement of detection rules (monthly minimum)
- Periodic testing through simulated attacks and penetration testing (quarterly recommended)
- Continuous training for security teams on new features and emerging threats
- Performance monitoring and optimization
The Seceon Advantage in Threat Detection
When selecting threat detection software, the platform’s capabilities, ease of use, and proven effectiveness matter significantly. Seceon’s aiSIEM platform represents a comprehensive approach to cybersecurity that goes beyond traditional threat detection.
Key Differentiators
Unified Security Platform: Seceon integrates SIEM, threat intelligence, behavioral analytics, automated response, and compliance management in a single solution, eliminating the complexity of managing multiple disparate tools. Organizations using unified platforms report 44% lower operational costs.
AI-Driven Detection: The platform’s artificial intelligence continuously learns from your environment, dramatically reducing false positives by up to 90% while improving detection accuracy for sophisticated threats to 99.3%.
Rapid Deployment: Unlike traditional SIEM solutions requiring months of implementation, Seceon can be operational within hours, providing immediate value and protection. Time-to-value averages 24-48 hours.
Cost-Effective Protection: By consolidating multiple security functions, Seceon offers enterprise-grade protection at a fraction of the cost of building and maintaining a complex security stack. Organizations report average savings of 60% compared to legacy solutions.
Automated Threat Response: Seceon’s orchestration capabilities enable automated containment and remediation, reducing mean time to respond (MTTR) from an industry average of 277 days to under 24 hours, limiting breach impact by 85%.
Cloud-Native Architecture: Designed for modern hybrid and multi-cloud environments with seamless scalability and zero infrastructure overhead.
24/7 Expert Support: Access to Seceon’s security operations center (SOC) and threat intelligence team for continuous protection and guidance.
Measuring Threat Detection Success
Implementing threat detection software is just the beginning. Organizations should track key performance indicators to ensure their investment delivers expected results:
- Mean Time to Detect (MTTD): How quickly threats are identified after they enter your environment (industry best practice: under 24 hours)
- Mean Time to Respond (MTTR): The speed at which detected threats are contained and remediated (target: under 1 hour for critical threats)
- False Positive Rate: The percentage of alerts that don’t represent genuine threats (aim for under 5%)
- Coverage Metrics: The proportion of your digital assets actively monitored (target: 100%)
- Threat Intelligence Accuracy: The relevance and timeliness of threat intelligence feeds (update frequency: real-time)
- Incident Prevention Rate: The number of attacks stopped before causing damage (benchmark: 98%+)
- Security ROI: Cost savings from prevented breaches versus security investment (average ROI: 340%)
Take Action Now: Protect Your Organization with Seceon
The cyber threats of 2026 require immediate action. Every day without comprehensive threat detection increases your exposure to potentially catastrophic breaches. Don’t become another statistic in the growing list of compromised organizations.
Join 2,500+ Organizations Protected by Seceon
From Fortune 500 enterprises to growing mid-market companies, organizations worldwide trust Seceon to protect their most valuable assets. With a 98.7% customer satisfaction rate and proven track record of stopping advanced threats, Seceon delivers the protection you need with the simplicity you want.
Conclusion: Strategic Investment in Threat Detection
As cyber threats continue to evolve in sophistication and frequency
Modern threat detection platforms like Seceon provide the intelligence, automation, and response capabilities essential for protecting critical assets in today’s threat landscape. Organizations implementing advanced detection solutions experience 60% fewer successful breaches and reduce incident response times by 85%.
When evaluating threat detection solutions, prioritize platforms offering real-time monitoring, AI-driven analytics, automated response, and seamless integration capabilities. Your organization’s resilience, compliance posture, and competitive advantage depend on implementing robust security infrastructure today.

The post Threat Detection Software: The Complete Guide to Protecting Your Digital Assets in 2026 appeared first on Seceon Inc.
*** This is a Security Bloggers Network syndicated blog from Seceon Inc authored by Anand Prasad. Read the original post at: https://seceon.com/threat-detection-software-the-complete-guide-to-protecting-your-digital-assets-in-2026/
如有侵权请联系:admin#unsafe.sh