
好的,我现在需要帮用户总结一篇关于WatchGuard防火墙漏洞的文章,控制在100字以内。首先,我得通读整篇文章,抓住关键信息。 文章提到有超过115,000台WatchGuard Firebox设备暴露在线,且未修补一个关键的远程代码执行漏洞CVE-2025-14733。这个漏洞影响Fireware OS 11.x及更高版本。攻击者可以利用这个漏洞在未经身份验证的情况下远程执行任意代码。 进一步的信息显示,只有配置了IKEv2 VPN的设备才容易受到攻击。即使移除了易受攻击的配置,如果还配置了Branch Office VPN到静态网关对等体,设备仍然可能处于风险中。WatchGuard提供了补丁,并建议用户旋转本地存储的秘密,并给出了临时修复措施。 Shadowserver报告称,在补丁发布后一天内发现了超过124,658个未修补的实例,其中大部分在第二天仍然暴露。CISA将此漏洞加入已知被利用的漏洞目录,并要求联邦机构在一周内修补设备。 此外,文章还提到WatchGuard之前修补过类似的漏洞CVE-2025-9242和CVE-2022-23176,说明这是一个持续的问题。 现在我需要把这些信息浓缩到100字以内。重点包括:受影响设备数量、漏洞名称和版本、攻击者的能力、易受攻击的条件、补丁情况、暴露数量以及CISA的行动。 可能的结构是:描述问题、受影响范围、攻击方式、修复建议和影响数据。这样确保所有关键点都被涵盖,并且语言简洁明了。 </think> 超过11.5万台未修补的WatchGuard Firebox设备暴露在线,面临关键远程代码执行漏洞CVE-2025-14733威胁。该漏洞影响Fireware OS 11.x及以上版本,允许未经身份验证的攻击者远程执行任意代码。仅配置为IKEv2 VPN的设备易受攻击,CISA要求联邦机构在一周内完成修复以应对活跃攻击。 2025-12-22 09:15:22 Author: www.bleepingcomputer.com(查看原文) 阅读量:9 收藏

Over 115,000 WatchGuard Firebox devices exposed online remain unpatched against a critical remote code execution (RCE) vulnerability actively exploited in attacks.
The security flaw, tracked as CVE-2025-14733, affects Firebox firewalls running Fireware OS 11.x and later (including 11.12.4_Update1), 12.x or later (including 12.11.5), and 2025.1 up to and including 2025.1.3.
Successful exploitation enables unauthenticated attackers to execute arbitrary code remotely on vulnerable devices, following low-complexity attacks that don't require user interaction.
As WatchGuard explained in a Thursday advisory, when it released CVE-2025-14733 security updates and tagged it as exploited in the wild, unpatched Firebox firewalls are only vulnerable to attacks if configured for IKEv2 VPN. It also warned that even if vulnerable configurations are removed, the firewall may still be at risk if a Branch Office VPN (BOVPN) to a static gateway peer is still configured.
"WatchGuard Fireware OS iked process contains an out of bounds write vulnerability in the OS iked process," an NVD advisory explains. "This vulnerability may allow a remote unauthenticated attacker to execute arbitrary code and affects both the mobile user VPN with IKEv2 and the branch office VPN using IKEv2 when configured with a dynamic gateway peer."
WatchGuard has shared indicators of compromise to help customers identify compromised Firebox appliances on their network, advising those who find signs of malicious activity to rotate all locally stored secrets on vulnerable firewalls. It also provided a temporary workaround for network defenders who can't immediately patch vulnerable devices, requiring them to disable dynamic peer BOVPNs, add new firewall policies, and disable the default system policies that handle VPN traffic.
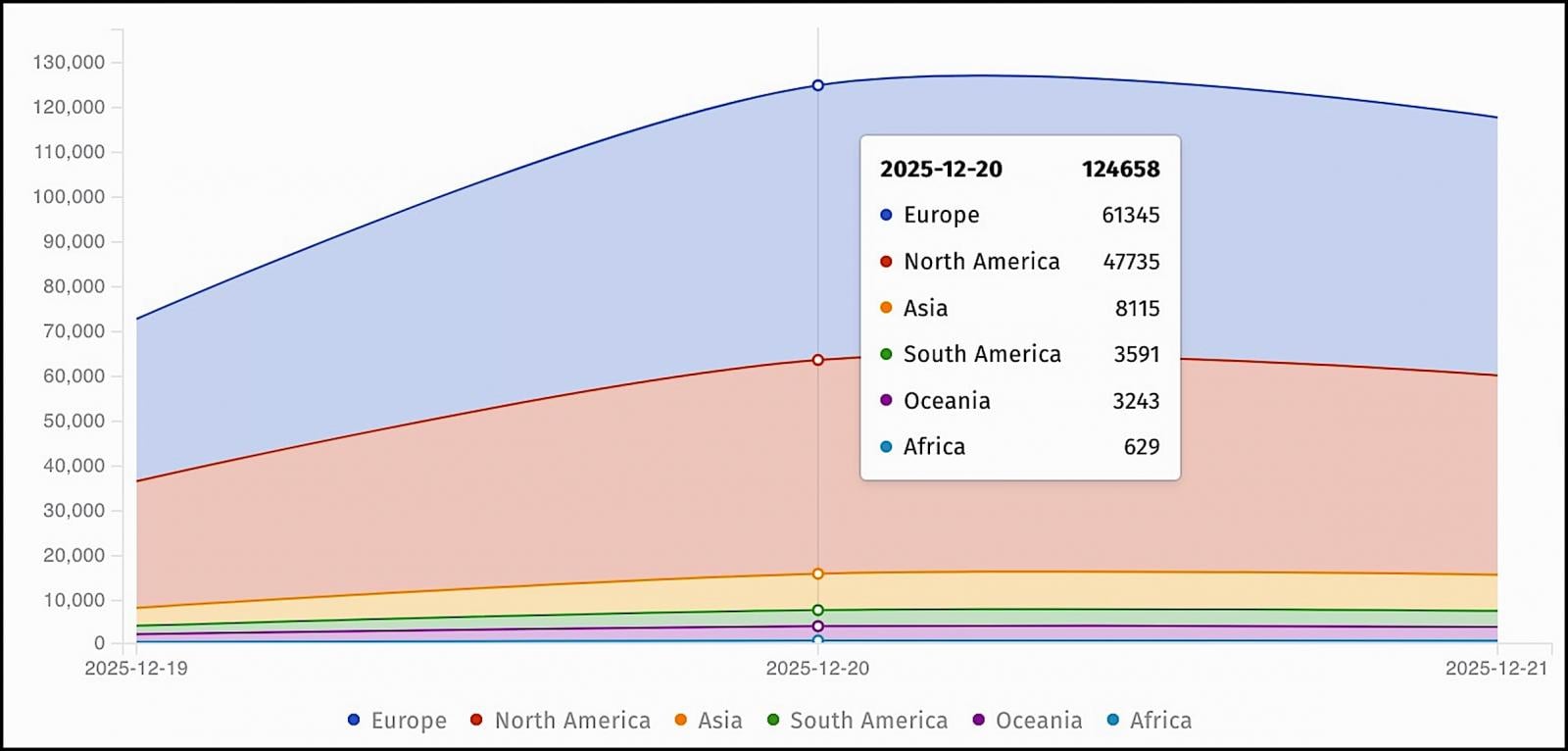
On Saturday, the Internet security watchdog group Shadowserver found over 124,658 unpatched Firebox instances exposed online, with 117,490 still exposed on Sunday.
One day after WatchGuard released patches, CISA added CVE-2025-14733 to its Known Exploited Vulnerabilities (KEV) Catalog.
The U.S. cybersecurity agency also ordered Federal Civilian Executive Branch (FCEB) agencies (executive branch non-military agencies, such as the Department of Energy, the Department of the Treasury, and the Department of Homeland Security) to patch Firebox firewalls within a week, by December 26th, as mandated by the Binding Operational Directive (BOD) 22-01.
"This type of vulnerability is a frequent attack vector for malicious cyber actors and poses significant risks to the federal enterprise," CISA warned. "Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable."
In September, WatchGuard patched an almost identical RCE vulnerability (CVE-2025-9242) impacting Firebox firewalls. One month later, Shadowserver found over 75,000 Firebox firewalls vulnerable to CVE-2025-9242 attacks, most in North America and Europe, with CISA later tagging the security flaw as actively exploited in the wild and ordering federal agencies to secure their Firebox appliances from ongoing attacks.
Two years ago, CISA also ordered U.S. government agencies to patch another actively exploited WatchGuard flaw (CVE-2022-23176) impacting Firebox and XTM firewall appliances.
WatchGuard works with over 17,000 security resellers and service providers to protect the networks of more than 250,000 small and mid-sized companies worldwide.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.
如有侵权请联系:admin#unsafe.sh

