
2025-12-22: StealC from files impersonating cracked versions of popular software
文章描述了StealC v2恶意软件通过伪装成流行软件的破解版本进行传播的过程。攻击者诱导用户从虚假网站下载文件,这些文件实际上是经过伪装的恶意程序。一旦运行,恶意程序会窃取用户数据并发送到指定服务器。相关技术细节包括文件哈希、大小和类型等。 2025-12-22 05:51:0 Author: www.malware-traffic-analysis.net(查看原文) 阅读量:11 收藏
文章描述了StealC v2恶意软件通过伪装成流行软件的破解版本进行传播的过程。攻击者诱导用户从虚假网站下载文件,这些文件实际上是经过伪装的恶意程序。一旦运行,恶意程序会窃取用户数据并发送到指定服务器。相关技术细节包括文件哈希、大小和类型等。 2025-12-22 05:51:0 Author: www.malware-traffic-analysis.net(查看原文) 阅读量:11 收藏
2025-12-22 (MONDAY): STEALC FROM FILES IMPERSONATING CRACKED VERSIONS OF POPULAR SOFTWARE
ASSOCIATED FILES:
- 2025-12-22-IOCs-for-StealC-infection.txt.zip 1.4 kB (1,385 bytes)
- 2025-12-22-StealC-files.zip 20.2 MB (20,183,148 bytes)
- 2025-12-22-traffic-from-StealC-infection.zip 46.2 MB (46,246,925 bytes)
NOTES:
- We used to see Lumma Stealer from this type of download, but now it's StealC v2.
2025-12-22 (MONDAY): STEALC FROM FILES IMPERSONATING CRACKED VERSIONS OF POPULAR SOFTWARE TRAFFIC LEADING TO THE INITIAL FILE DOWNLOAD: - Page from site claiming to have cracked version of popular software - hxxps[:]//gorcerie[.]com/the-impact-of-clear-excess-formats-on-business-performance-and-data-integrity/?[info removed] - hxxps[:]//media.maxdatahost1[.]lat/share/download?AH2hSGmZbAUAWGgCAFVTFwASAAAAAADc/[name of software]&rar - hxxps[:]//arch2.megafilehost8[.]mom/e/get/0dW2euBOrmIidUcl3Q7OBgzi/application.zip EXAMPLE OF STEALC TRAFFIC AFTER RUNNING EXE EXTRACTED FROM THE DOWNLOADED FILE: - hxxp[:]//37.221.66[.]166/4a815a53876a4172.php <-- repeated HTTP POST requests ASSOCIATED FILES - SHA256 hash: fd885e2a9fa8b945850f42fe2a27fdd75b377c34b77b12af2366d38e90062af3 - File size: 15,228,803 bytes - File name: application.7z - File type: 7-zip archive data, version 0.4 - File description: Initial download, a password-protected 7-zip archive - Password: 4650 - SHA256 hash: 8d46297b6191e44ff42975839bd767662622aed84e1d0025b05e171f55ff015e - File size: 895,382,766 bytes - File name: appFile.exe - File type: PE32+ executable (GUI) x86-64, for MS Windows - File description: Extracted from the 7-zip archive, an inflated 64-bit EXE padded with null bytes - SHA256 hash: b2f7371fa7599c9e72d7e3f4129741b8d240a4b8b00e2e889835c57c66f21848 - File size: 30,796,046 bytes - File type: PE32+ executable (GUI) x86-64, for MS Windows - File description: The above 64-bit EXE with most of the null bytes removed
IMAGES
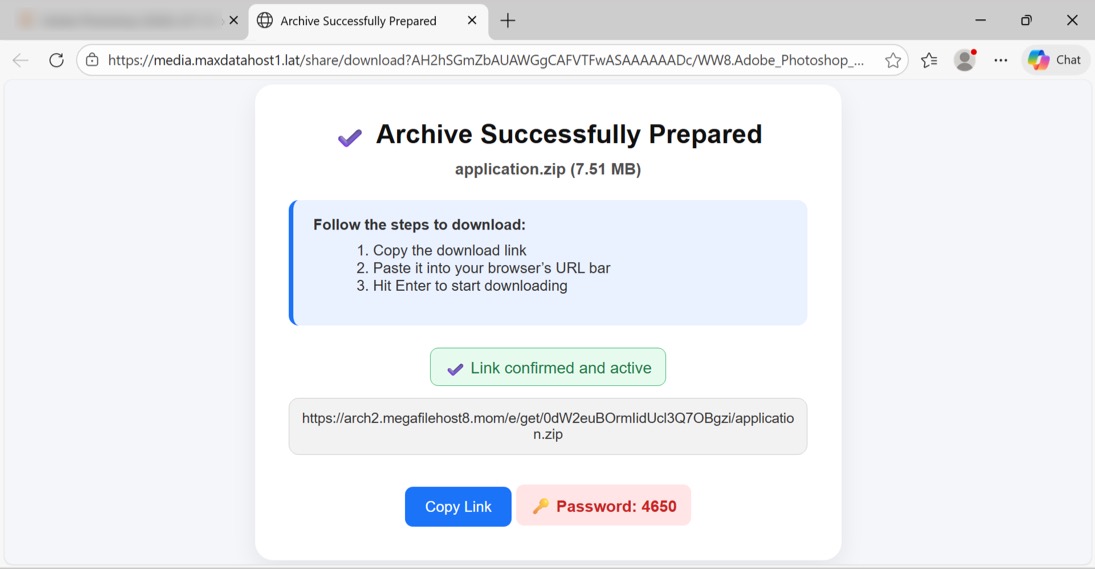
Shown above: Example of page with URL to download the initial file.
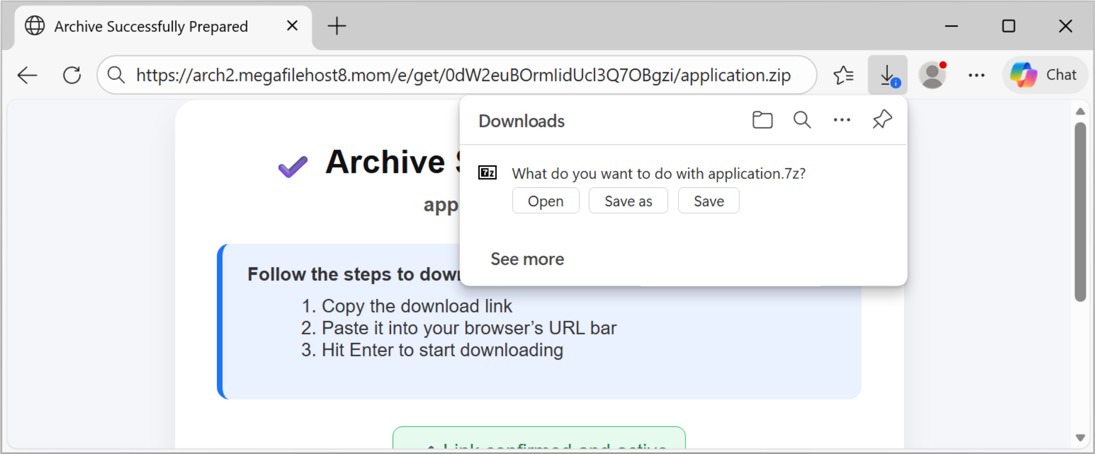
Shown above: Using the URL to download the initial file, a password-protected 7-zip archive.
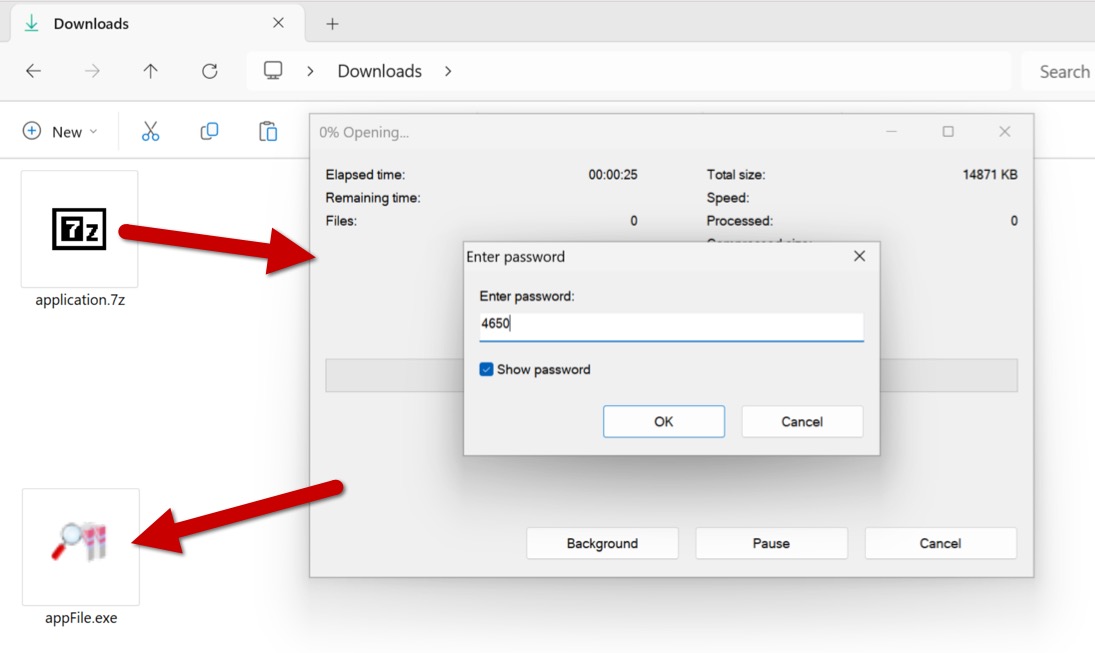
Shown above: Opening the password-protected 7-zip archive.

Shown above: Characteristics of the inflated EXE within the 7-zip archive.
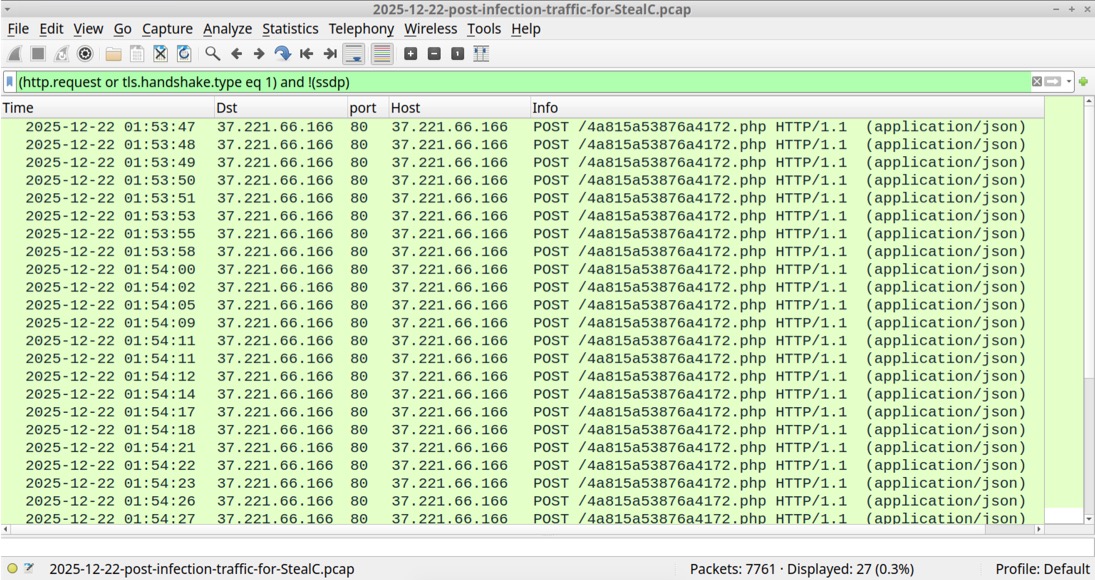
Shown above: StealC traffic after running the inflated EXE.
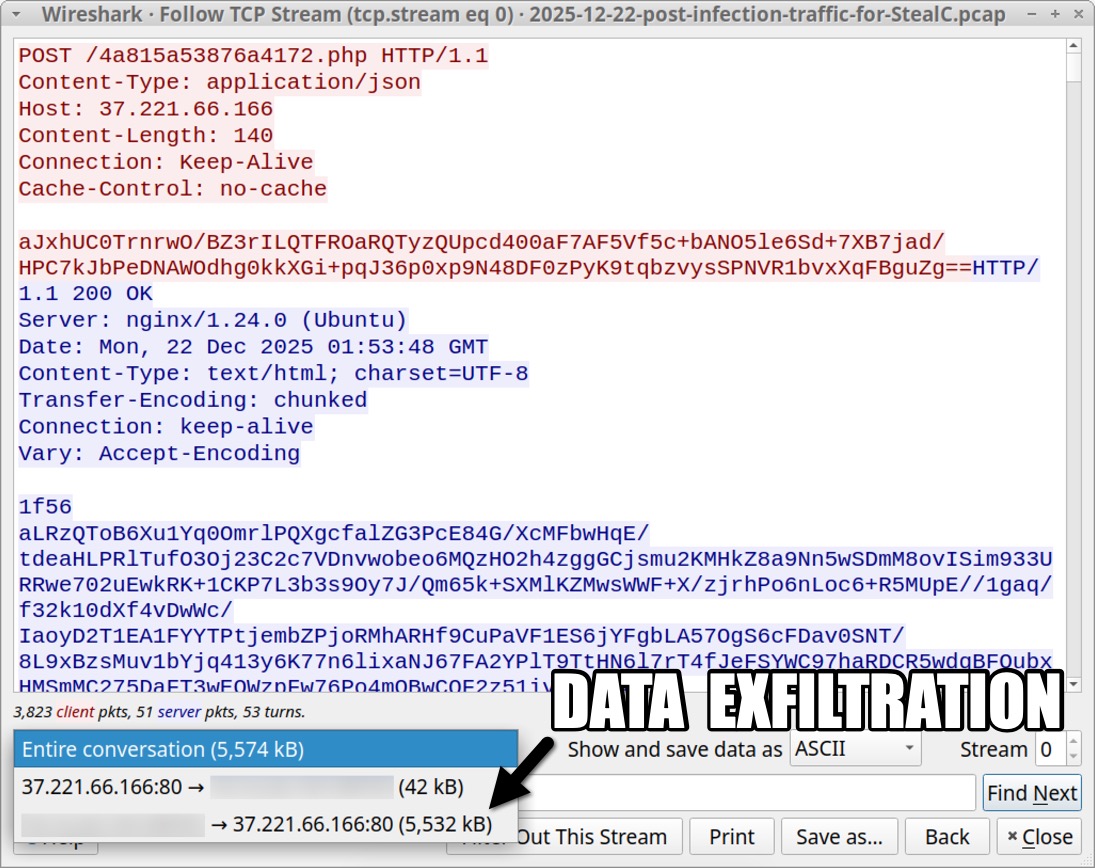
Shown above: TCP stream of the StealC traffic.
Click here to return to the main page.
文章来源: https://www.malware-traffic-analysis.net/2025/12/22/index.html
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh