
多个威胁行为者利用OAuth设备代码授权机制,在钓鱼攻击中入侵微软365账户。攻击者诱使受害者输入设备代码,授权其应用程序访问账户。自9月以来此类攻击显著增加,涉及网络犯罪分子和国家背景的威胁行为者。 2025-12-19 17:31:18 Author: www.bleepingcomputer.com(查看原文) 阅读量:3 收藏

Multiple threat actors are compromising Microsoft 365 accounts in phishing attacks that leverage the OAuth device code authorization mechanism.
Attackers trick victims into entering a device code on Microsoft’s legitimate device login page, unknowingly authorizing an attacker-controlled application and granting them access to the target account without stealing credentials or bypassing multi-factor authentication (MFA).
Although the method isn’t new, email security firm Proofpoint says that these attacks have increased significantly in volume since September, and involve both financially motivated cybercriminals like TA2723 and state-aligned threat actors.
"Proofpoint Threat Research has observed multiple threat clusters using device code phishing to trick users into granting a threat actor access to their Microsoft 365 account," the security company warned, adding that widespread campaigns using these attack flows are "highly unusual."
Tools and campaigns
The attack chains that Proofpoint observed in the campaigns have slight variations, but they all involve tricking victims into entering a device code on Microsoft’s legitimate device login portals.
In some cases, the device code is presented as a one-time password, while the lure can be a token re-authorization notification in others.
The researchers observed two phishing kits used in the attacks, namely SquarePhish v1 and v2, and Graphish, which simplify the phishing process.
SquarePhish is a publicly available red teaming tool that targets OAuth device grant authorization flows via QR codes, mimicking legitimate Microsoft MFA/TOTP setups.
Graphish is a malicious phishing kit shared on underground forums, supporting OAuth abuse, Azure App Registrations, and adversary-in-the-middle (AiTM) attacks.
Regarding the campaigns Proofpoint observed, the researchers highlighted three in the report:
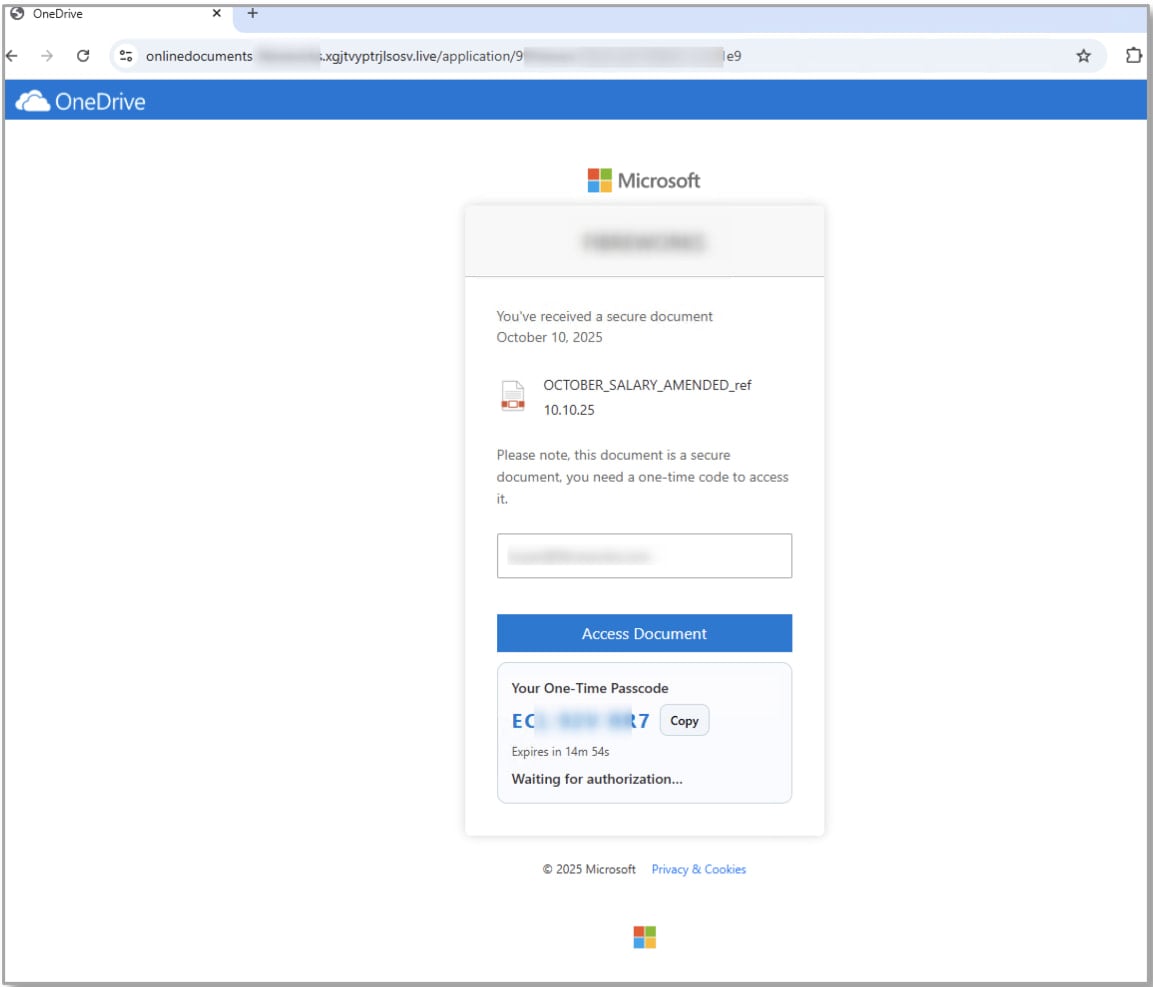
- Salary bonus attacks – A campaign using document-sharing lures and localized company branding to entice recipients to click links to attacker-controlled websites. Victims are then instructed to complete "secure authentication" by entering a provided code on Microsoft’s legitimate device login page, which authorizes an attacker-controlled application.
.jpg)
Source: Proofpoint
- TA2723 attacks – An actor involved in high-volume credential-phishing, previously known for spoofing Microsoft OneDrive, LinkedIn, and DocuSign, that started using OAuth device code phishing in October. Proofpoint assesses that early phases of these campaigns likely used SquarePhish2, with later waves potentially shifting to the Graphish phishing kit.
Source: Proofpoint
- State-aligned activity – Since September 2025, Proofpoint observed a suspected Russia-aligned threat actor tracked as UNK_AcademicFlare abusing OAuth device code authorization for account takeover. The actor uses compromised government and military email accounts to build rapport before sharing links that spoof OneDrive, leading victims into a device code phishing workflow. The activity primarily targets government, academic, think tank, and transportation sectors in the U.S. and Europe.
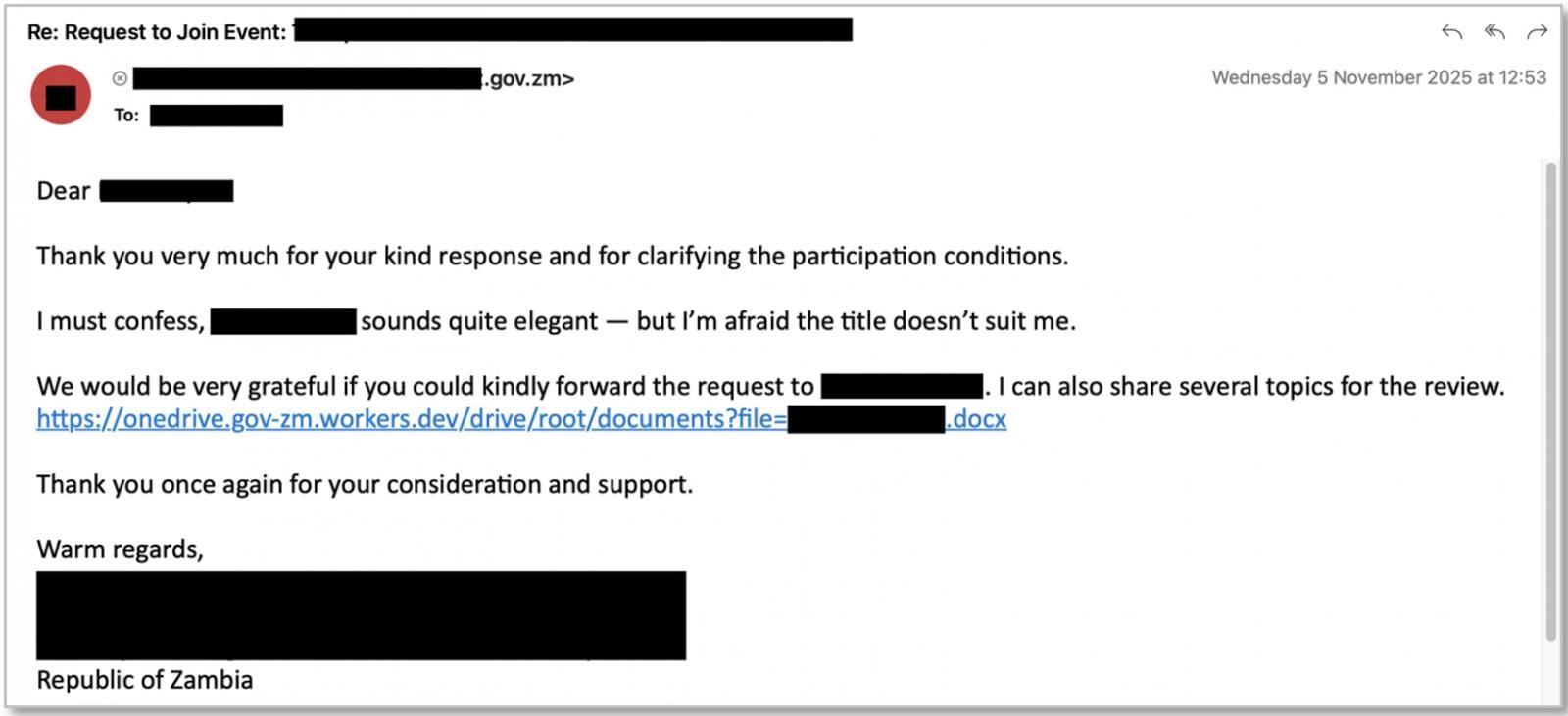
Source: Proofpoint
To block these attacks, Proofpoint recommends that organizations use Microsoft Entra Conditional Access where possible and consider introducing a policy on sign-in origin.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.
如有侵权请联系:admin#unsafe.sh

