
嗯,用户让我帮忙总结一篇文章的内容,控制在100字以内,而且不需要用“文章内容总结”之类的开头。首先,我得仔细阅读用户提供的文章内容,抓住主要信息。 文章讲的是一个自动化攻击活动,针对Palo Alto Networks的GlobalProtect和Cisco的SSL VPN平台。攻击者使用了基于凭证的攻击方式,利用了超过1万个IP地址进行登录尝试,主要针对美国、墨西哥和巴基斯坦的基础设施。攻击流量来自德国的一个云服务提供商,使用了Firefox用户代理,看起来像是脚本化的探测活动。 然后,攻击者还转向了Cisco SSL VPN端点,同样使用了大量的IP地址进行探测。虽然Cisco发布了零日漏洞警告,但GreyNoise没有发现关联证据。Palo Alto建议用户使用强密码和多因素认证,并确认这些攻击只是凭证探测,并非系统被攻破。 所以,我需要把这些关键点浓缩到100字以内:自动化攻击活动、目标VPN平台、基于凭证、大量IP地址、特定国家、德国云服务、Firefox用户代理、脚本化探测、转向Cisco VPN、无漏洞关联、建议措施。 最后,确保语言简洁明了,不遗漏重要信息。 </think> 一篇关于针对Palo Alto Networks GlobalProtect和Cisco SSL VPN平台的自动化凭证攻击的文章。攻击者利用超过1万个IP地址对美国、墨西哥和巴基斯坦的基础设施发起登录尝试,恶意流量主要来自德国的一家云服务提供商。研究人员观察到攻击者使用Firefox用户代理进行脚本化凭证探测。此外,同一攻击源还针对Cisco SSL VPN端点发起类似活动。Palo Alto建议用户加强密码保护并启用多因素认证。 2025-12-18 17:30:25 Author: www.bleepingcomputer.com(查看原文) 阅读量:3 收藏

An automated campaign is targeting multiple VPN platforms, with credential-based attacks being observed on Palo Alto Networks GlobalProtect and Cisco SSL VPN.
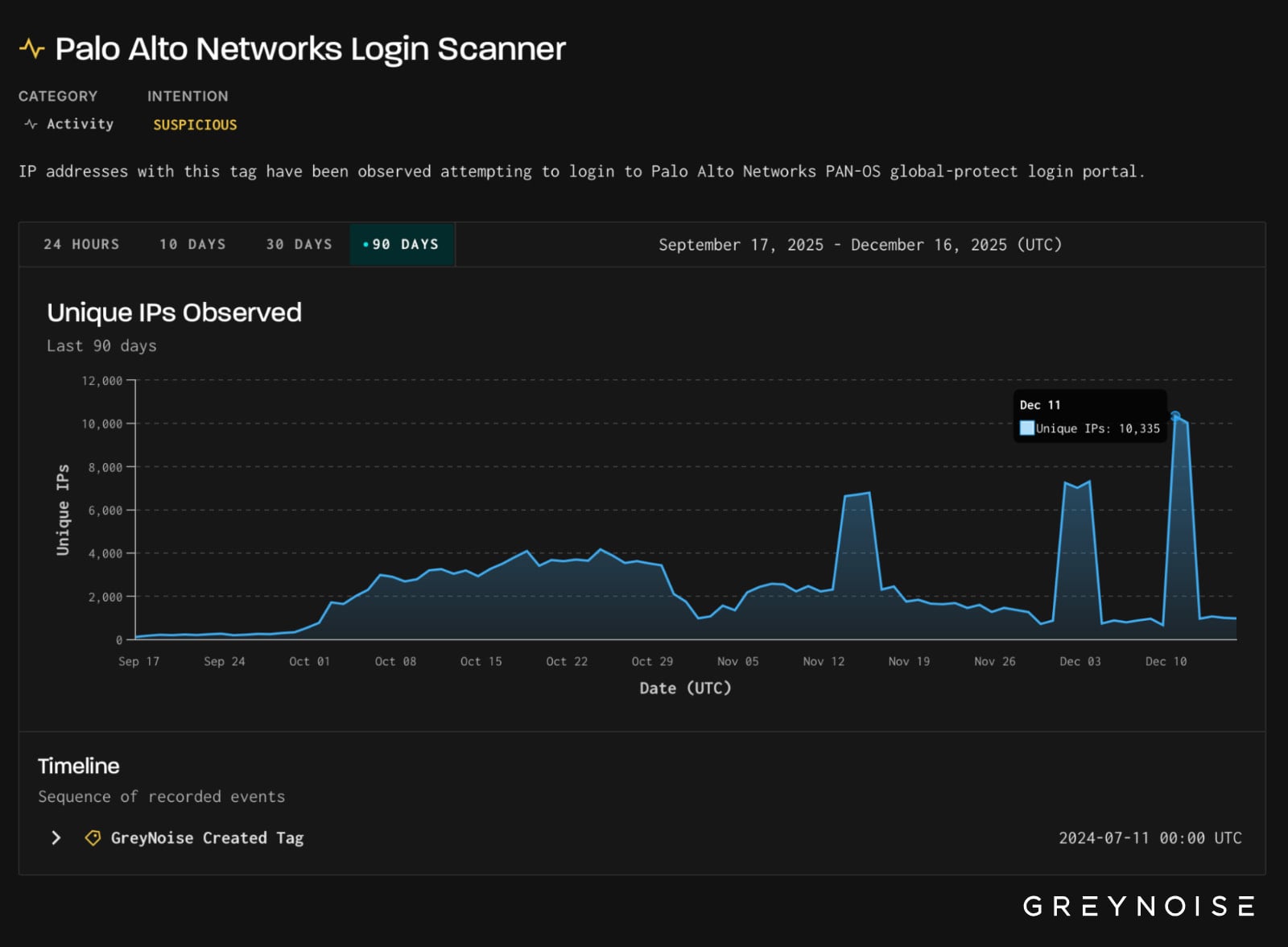
On December 11, threat monitoring platform GreyNoise observed the number of login attempts aimed at GlobalProtect portals peaked at 1.7 million during a period of 16 hours.
Collected data showed that the attacks originated from more than 10,000 unique IP addresses and were aimed at infrastructure located in the United States, Mexico, and Pakistan.
The malicious traffic originated almost entirely from the 3xK GmbH (Germany) IP space, indicating a centralized cloud infrastructure.
Based on researchers' observations, the threat actor reused common username and password combinations, and most of the requests were from a Firefox user agent that is uncommon for automated login activity through this provider.
"The consistency of the user agent, request structure, and timing suggests scripted credential probing designed to identify exposed or weakly protected GlobalProtect portals, rather than interactive access attempts or vulnerability exploitation," GreyNoise explains.
“This activity reflects continued pressure against enterprise VPN authentication endpoints, a pattern GreyNoise has observed repeatedly during periods of heightened attacker activity.”
Source: GreyNoise
On December 12, activity originating from the same hosting provider using the same TCP fingerprint started to probe Cisco SSL VPN endpoints.
GreyNoise monitors recorded a jump of unique attack IPs to 1,273, from the normal baseline of less than 200.
The activity constitutes the first large-scale use of 3xK-hosted IPs against Cisco SSL VPNs in the past 12 weeks.
In this case, too, the login payloads followed normal SSL VPN authentication flows, including CSRF handling, indicating automated credential attacks rather than exploits.

Source: GreyNoise
Yesterday, Cisco warned customers of a maximum-severity zero-day vulnerability (CVE-2025-20393) in Cisco AsyncOS that is actively exploited in attacks targeting Secure Email Gateway (SEG) and Secure Email and Web Manager (SEWM) appliances.
However, GreyNoise underlines that it found no evidence linking the observed activity to CVE-2025-20393.
A Palo Alto Networks spokesperson confirmed to BleepingComputer that they are aware of the activity. The company recommends users to use strong passwords and multi-factor authentication protection.
“We are aware of the credential-based activity reported by GreyNoise targeting VPN gateways, including GlobalProtect portals. This activity reflects automated credential probing and does not constitute a compromise of our environment or an exploitation of any Palo Alto Networks vulnerability," the Palo Alto Networks spokesperson said.
"Our investigation confirms that these are scripted attempts to identify weak credentials," they added.
Apart from the recommended Palo Alto Networks action, Grey Noise also advises administrators to audit network appliances, look for unexpected login attempts, and block known malicious IPs performing these probes.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.
如有侵权请联系:admin#unsafe.sh

