
嗯,用户让我帮忙总结一下这篇文章的内容,控制在100字以内,而且不需要用“文章内容总结”或者“这篇文章”这样的开头,直接写描述。首先,我需要仔细阅读文章内容,抓住主要信息。 文章讲的是亚马逊的AWS GuardDuty团队警告了一个针对EC2和ECS的加密货币挖矿活动。攻击者使用了被妥协的IAM凭证。这个活动从11月2日开始,用了持久机制来延长挖矿时间,并阻碍事件响应者。 攻击者使用了一个Docker Hub镜像,这个镜像在10月底创建,下载量超过10万次。亚马逊提到攻击者没有利用漏洞,而是使用了有效的客户凭证。他们在EC2上创建了启动模板和自动扩展组,在ECS上注册了任务定义,指向恶意镜像。镜像中包含挖矿软件和启动脚本。 此外,攻击者启用了实例终止保护,让管理员无法远程终止实例,必须先禁用保护才能关闭。亚马逊已经通知受影响的客户,并移除了恶意镜像,但提醒威胁行为者可能还会使用其他名称和账户。 现在我要把这些信息浓缩到100字以内。重点包括:攻击目标、使用的凭证、时间、持久机制、使用的Docker镜像、影响以及亚马逊的应对措施。 可能的结构是:亚马逊警告EC2和ECS被加密挖矿攻击利用IAM凭证;攻击始于11月2日,使用恶意Docker镜像;启用实例终止保护;已通知客户并移除镜像。 这样应该能控制在100字以内,并且直接描述内容。 </think> 亚马逊警告称,针对其EC2和ECS服务的加密货币挖矿活动利用了被妥协的IAM凭证展开攻击。该活动始于11月2日,采用恶意Docker镜像并启用实例终止保护以延长挖矿时间。亚马逊已通知受影响客户并移除恶意镜像。 2025-12-17 22:0:20 Author: www.bleepingcomputer.com(查看原文) 阅读量:1 收藏

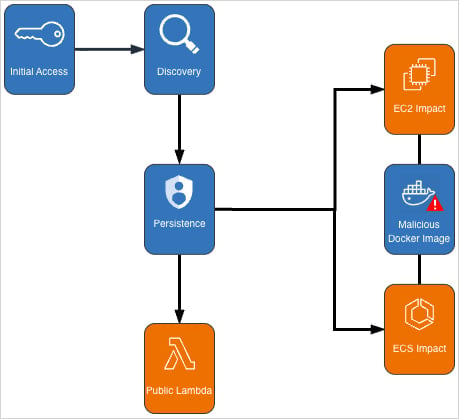
Amazon’s AWS GuardDuty security team is warning of an ongoing crypto-mining campaign that targets its Elastic Compute Cloud (EC2) and Elastic Container Service (ECS) using compromised credentials for Identity and Access Management (IAM).
The operation started on November 2nd and employed a persistence mechanism that extended mining operations and hindered incident responders.
The threat actor used a Docker Hub image that was created at the end of October and had more than 100,000 pulls.
The Amazon EC2 service lets users run virtual machines in AWS, while ECS allows running containerized applications (e.g., Docker apps) on the cloud platform.
Planting crypto-miners on these instances allows threat actors to profit financially at the expense of AWS customers and Amazon, who must bear the burden of computational resource exhaustion.
Amazon says that the attacker did not leverage a vulnerability but used valid credentials in customer accounts.
Crypto-mining operations
AWS said in a report released today that the attacker started cryptomining within 10 minutes of initial access, following reconnaissance of EC2 service quotas and IAM permissions.
This was possible by registering a task definition pointing to the Docker Hub image yenik65958/secret, created on October 29, which included an SBRMiner-MULTI cryptominer and a startup script to launch it automatically when the container started.
Each task was configured with 16,384 CPU units and 32GB of memory, and the desired count for ECS Fargate tasks was set to 10.
Source: Amazon
On Amazon EC2, the attacker created two launch templates with startup scripts that automatically initiated cryptomining, along with 14 auto-scaling groups configured to deploy at least 20 instances each, with a maximum capacity of up to 999 machines.
Novel persistence method
Once the machines were running, the attacker enabled a setting that prevents administrators from remotely terminating them, forcing responders to explicitly disable the protection before shutting them down. This was likely introduced to delay response and maximize cryptomining profits.
"An interesting technique observed in this campaign was the threat actor’s use of ModifyInstanceAttribute across all launched EC2 instances to disable API termination," Amazon explains.
"Although instance termination protection prevents accidental termination of the instance, it adds an additional consideration for incident response capabilities and can disrupt automated remediation controls," the company says.
After identifying the campaign, Amazon alerted affected customers about the cryptomining activity and the need to rotate the compromised IAM credentials.
Also, the malicious Docker Hub image has been removed from the platform, but Amazon warns that the threat actor could deploy similar images under different names and publisher accounts.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.
如有侵权请联系:admin#unsafe.sh

