
A new campaign called 'GhostPoster' uses malicious Firefox extensions to hide JavaScript code in image logos, aiming to monitor browser activity and install a backdoor. Over 50,000 users have downloaded these extensions, which enable operators to hijack affiliate links, inject tracking code, and perform click and ad fraud. Researchers identified 17 compromised extensions across popular categories, highlighting the threat to user privacy and potential for more severe attacks. 2025-12-16 22:30:17 Author: www.bleepingcomputer.com(查看原文) 阅读量:1 收藏

A new campaign dubbed 'GhostPoster' is hiding JavaScript code in the image logo of malicious Firefox extensions with more than 50,000 downloads, to monitor browser activity and plant a backdoor.
The malicious code grants operators persistent high-privilege access to the browser, enabling them to hijack affiliate links, inject tracking code, and commit click and ad fraud.
The hidden script is acting as a loader that fetches the main payload from a remote server. To make the process more difficult to detect, the payload is intentionally retrieved only once in ten attempts.
Koi Security researchers discovered the GhostPoster campaign and identified 17 compromised Firefox extensions that either read the PNG logo to extract and execute the malware loader or download the main payload from the attacker's server.
It should be noted that the malicious extensions are from popular categories:
- free-vpn-forever
- screenshot-saved-easy
- weather-best-forecast
- crxmouse-gesture
- cache-fast-site-loader
- freemp3downloader
- google-translate-right-clicks
- google-traductor-esp
- world-wide-vpn
- dark-reader-for-ff
- translator-gbbd
- i-like-weather
- google-translate-pro-extension
- 谷歌-翻译
- libretv-watch-free-videos
- ad-stop
- right-click-google-translate
The researchers say that not all the extensions above use the same payload loading chain, but all of them exhibit the same behavior and communicate with the same infrastructure.
The FreeVPN Forever extension was the one Koi Security analyzed initially after its AI tool flagged it for parsing the raw bytes of its logo image file to locate a JavaScript snippet hidden using the steganography technique.
Source: Koi Security
The JavaScript loader activates 48 hours later to fetch a payload from a hardcoded domain. A second backup domain is available if the payload is not retrieved from the first one.
According to Koi Security, the loader is mostly dormant and gets the payload only 10% of the time, making it likely to evade detection from traffic monitoring tools.
The downloaded payload is heavily obfuscated via case swapping and base64 encoding. A cipher decodes it and then XOR-encrypts it using a key derived from the extension’s runtime ID.
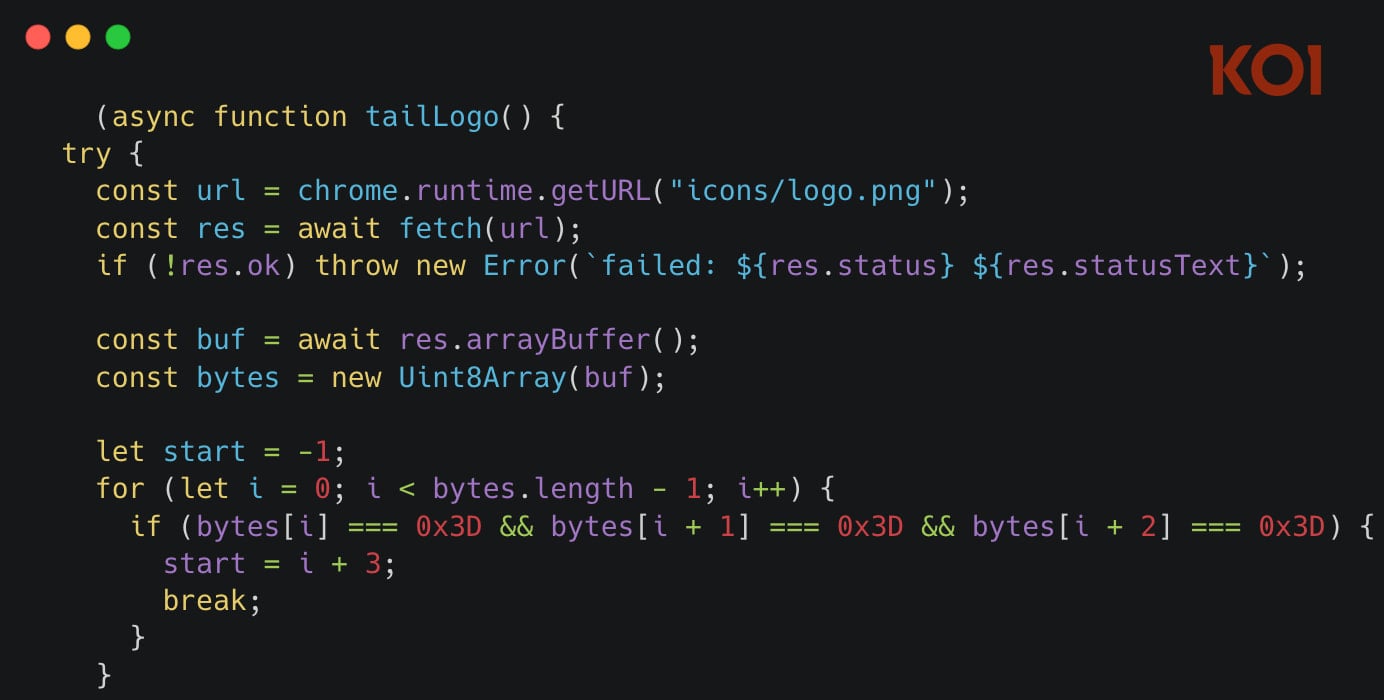
Source: Koi Security
The final payload has the following capabilities:
- Hijacks affiliate links on major e-commerce sites, redirecting commissions to the attackers.
- Injects Google Analytics tracking into every page the user visits.
- Strips security headers from all HTTP responses.
- Bypasses CAPTCHA via three distinct mechanisms to circumvent bot protections.
- Injects invisible iframes for ad fraud, click fraud, and tracking, which self-delete after 15 seconds.
Although the malware does not harvest passwords or redirect users to phishing pages, it still threatens user privacy.
Moreover, due to the stealthy loader employed by GhostPoster, the campaign could quickly become far more dangerous if the operator decides to deploy a more harmful payload.
Users of the listed extensions are recommended to remove them and should consider resetting passwords for critical accounts.
Many of the malicious extensions were still available on Firefox’s Add-Ons page at the time of writing. BleepingComputer has contacted Mozilla about it, but a comment wasn’t immediately available.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.
如有侵权请联系:admin#unsafe.sh

