
嗯,用户让我帮忙总结一篇文章,控制在100字以内,而且不需要特定的开头。首先,我需要仔细阅读这篇文章,了解其主要内容和重点。 文章主要讨论了现代企业面临的网络安全挑战,特别是随着IT环境变得越来越复杂,包括本地数据中心、多个云平台和混合架构。传统的安全方法已经无法应对这些复杂的威胁,因此文章提出了一个统一的安全平台作为解决方案。 接下来,文章详细介绍了三种基础设施模型:本地、云和混合基础设施,并解释了每种模型的特点及其在现代业务中的重要性。然后,文章讨论了这些分布式基础设施带来的安全挑战,指出传统安全工具的碎片化导致了效率低下、盲点和高昂的成本。 最后,文章介绍了Seceon的统一安全平台,强调其通过整合多种安全功能、利用AI驱动威胁检测和自动化响应来提供全面的保护。Seceon的优势在于其统一的架构和对混合及多云环境的支持。 现在,我需要将这些要点浓缩到100字以内。首先确定关键信息:现代企业面临复杂IT环境的安全挑战;传统方法失效;Seceon提供统一平台整合安全功能;AI驱动检测和自动化响应;支持混合云环境;提升效率并降低成本。 确保语言简洁明了,直接描述内容。避免使用“这篇文章”或“总结”这样的开头词。检查字数是否符合要求,并调整句子结构以优化表达。 </think> 现代企业面临复杂IT环境的安全挑战,传统分散式安全方法失效。Seceon提供统一安全平台整合多种功能(如SIEM、XDR、SOAR),通过AI驱动威胁检测与自动化响应实现全面保护。该平台支持本地、云及混合架构,提升效率并降低成本。 2025-12-16 12:34:1 Author: securityboulevard.com(查看原文) 阅读量:2 收藏
Breaking Free from Security Silos in the Modern Enterprise
Today’s organizations face an unprecedented challenge: securing increasingly complex IT environments that span on-premises data centers, multiple cloud platforms, and hybrid architectures. Traditional security approaches that rely on disparate point solutions are failing to keep pace with sophisticated threats, leaving critical gaps in visibility and response capabilities.
The solution? A unified security platform that delivers comprehensive protection across your entire digital ecosystem-regardless of where your assets reside.
Understanding Modern Infrastructure Models
Before diving into security challenges, it’s essential to understand the three fundamental infrastructure models that organizations rely on today-and why each plays a critical role in modern business operations.
On-Premises Infrastructure: The Traditional Foundation
On-premises infrastructure refers to IT resources that organizations own, control, and operate within their physical facilities. This includes servers, storage systems, networking equipment, and security appliances housed in company-owned or co-located data centers.
Key Characteristics:
- Physical hardware owned and maintained by the organization
- Complete control over security configurations and access policies
- Direct management of performance, capacity, and upgrades
Data residency within organizational boundaries
Why On-Premises Remains Critical:
Despite the cloud revolution, on-premises infrastructure continues to serve vital functions for many organizations. Legacy applications that were architected decades ago often cannot be easily migrated to cloud environments without complete re-engineering. Financial institutions, healthcare providers, and government agencies frequently maintain on-premises systems to satisfy regulatory requirements around data sovereignty and control.
Performance-sensitive applications benefit from the predictable latency and dedicated resources that on-premises infrastructure provides. Manufacturing systems, real-time trading platforms, and high-performance computing workloads often demand the control and consistency that only on-premises environments deliver.
For organizations with substantial capital investments in existing infrastructure, maintaining on-premises systems makes economic sense. Rather than abandoning functional hardware and software, these assets continue delivering value for years beyond initial deployment.
Cloud Infrastructure: Agility and Scale
Cloud infrastructure encompasses computing resources delivered as services over the internet by providers like Amazon Web Services, Microsoft Azure, and Google Cloud Platform. Instead of owning physical hardware, organizations consume compute, storage, and networking capabilities on demand.
Key Characteristics:
Managed services that reduce operational overhead
Resources are provisioned and scaled instantly through APIs or web interfaces
Pay-as-you-go pricing models that convert capital expenses to operational expenses
Global infrastructure enabling deployment across multiple geographic regions
The Strategic Importance of Cloud:
Cloud infrastructure fundamentally transforms how organizations build and deploy applications. Development teams can provision test environments in minutes rather than waiting weeks for hardware procurement. New product launches scale automatically to handle millions of users without advance capacity planning.
Geographic expansion becomes straightforward when cloud providers maintain data centers across continents. A startup in India can serve customers in Europe, Asia, and the Americas with low latency by deploying applications across multiple regions—infrastructure that would cost millions to build independently.
The cloud’s elastic nature proves essential for workloads with variable demand. E-commerce platforms scale up during holiday shopping seasons, then scale down when traffic normalizes, paying only for resources actually consumed. This elasticity eliminates the waste inherent in provisioning for peak capacity that sits idle most of the year.
Innovation accelerates because cloud providers offer cutting-edge services, including artificial intelligence, machine learning, big data analytics, and IoT platforms. Organizations leverage these managed services to build sophisticated capabilities without assembling specialized infrastructure teams.
Hybrid Infrastructure: The Best of Both Worlds
Hybrid infrastructure strategically combines on-premises and cloud resources into a unified computing environment. Rather than viewing on-premises and cloud as competing alternatives, hybrid architectures recognize that different workloads have different requirements intelligent placement optimizes both cost and performance.
Key Characteristics:
- Seamless connectivity between on-premises data centers and cloud platforms
- Workload portability enables applications to run where they perform best
- Unified management and security policies across all environments
- Data synchronization and replication between locations
Why Hybrid Dominates Enterprise Strategy:
The reality is that most large organizations will operate hybrid environments indefinitely. Regulatory constraints, application dependencies, economic considerations, and strategic priorities create compelling reasons to maintain both on-premises and cloud infrastructure.
A global retailer might run its core inventory management system on-premises for performance and control, while using cloud infrastructure for customer-facing e-commerce platforms that must scale during peak shopping periods. Financial institutions keep sensitive transaction processing systems within their data centers while leveraging cloud services for customer mobile applications and data analytics.
Hybrid architectures enable gradual cloud migration without forcing risky big-bang transitions. Organizations can move applications to the cloud incrementally, validating performance and functionality before migrating additional workloads. This measured approach reduces risk while building organizational expertise in cloud operations.
Disaster recovery and business continuity capabilities improve dramatically in hybrid environments. On-premises systems can fail over to cloud infrastructure during outages, ensuring business continuity without maintaining duplicate physical data centers. Conversely, critical cloud workloads can fail back to on-premises systems if cloud provider issues arise.
The flexibility to optimize workload placement based on cost, performance, compliance, and business requirements represents the hybrid infrastructure’s fundamental advantage. Organizations aren’t locked into a single model but can make informed decisions about where each application and dataset should reside.
The Security Challenge: Protecting Distributed Infrastructure
Here’s where complexity becomes dangerous. Each infrastructure model introduces unique security considerations, and the combination creates exponentially more challenging protection requirements.
On-premises environments demand physical security, network segmentation, endpoint protection, and access controls managed entirely by internal teams. Cloud platforms introduce shared responsibility models where providers secure the underlying infrastructure while customers remain responsible for their applications, data, and configurations. Hybrid architectures must secure not only each environment independently but also the connections and data flows between them.
Traditional security approaches fail in this distributed reality because they were designed for perimeter-based protection of centralized data centers. When applications span multiple clouds and on-premises systems, there is no single perimeter to defend. Threats move laterally between environments, exploiting gaps in visibility where separate security tools lack context about the broader infrastructure.
The Hidden Costs of Fragmented Security
Most enterprises today operate with 10-20 different security tools, each monitoring a specific segment of their infrastructure. This fragmented approach creates several critical problems:
Alert Fatigue and Blind Spots: Security teams drowning in alerts from multiple dashboards miss critical threats buried in the noise. Without correlation between tools, attacks that span multiple environments go undetected.
Operational Inefficiency: Analysts waste valuable time toggling between separate consoles, manually correlating events, and stitching together incomplete threat narratives. The average organization spends 60% of its security budget just managing tool complexity.
Compliance Gaps: Demonstrating compliance across hybrid environments becomes a nightmare when security data lives in silos. Audit preparation consumes weeks of manual effort pulling reports from different systems.
Delayed Response Times: When threats emerge, every second counts. Fragmented tools slow incident response, giving attackers more time to move laterally, exfiltrate data, or deploy ransomware.For a typical 5,000-person organization, these inefficiencies translate to millions in annual costs-money that could be redirected toward strategic security initiatives rather than managing operational overhead.
What is Unified Security?
Unified security represents a fundamental shift from fragmented point solutions to a single, integrated platform that delivers 360-degree visibility across your entire infrastructure. Instead of separate tools for endpoints, networks, cloud workloads, and applications, a unified platform consolidates all security functions under one intelligent framework.
The core principles of unified security include:
Centralized Visibility: One comprehensive view of all security events, threats, and anomalies across on-premises systems, public clouds, private clouds, and SaaS applications.
Contextual Intelligence: Automatic correlation of data from logs, network flows, endpoints, identities, cloud services, and IoT devices to understand the full scope of threats.
Automated Response: Intelligent orchestration that responds to threats instantly-blocking malicious activity, isolating compromised systems, and mitigating risks before they escalate.Consistent Policy Enforcement: Security policies that apply uniformly across all environments, eliminating configuration gaps and ensuring comprehensive protection
The Seceon Unified Platform: Built Different from Day One
Unlike vendors that cobble together “integrated” solutions through acquisitions, Seceon engineered its platform from the ground up as a single, cohesive system. This architectural approach delivers transformative advantages for securing hybrid and multi-cloud environments.
AI-Driven Threat Detection Across All Environments
Seceon’s platform correlates data from logs, flows, identities, endpoints, cloud, OT, and IoT systems, applying artificial intelligence and machine learning to detect threats that traditional tools miss. The system doesn’t just flag anomalies-it understands context, distinguishing legitimate business activity from malicious behavior across your entire digital infrastructure.
The platform’s Dynamic Threat Modeling capability continuously adapts to your unique environment, learning normal patterns and identifying subtle indicators of compromise. From lateral movement and credential abuse to data exfiltration and insider threats, Seceon sees attack patterns before they progress to full breaches.
Seamless Hybrid and Multi-Cloud Protection
Whether your workloads run on AWS, Azure, Google Cloud, or your private data center, Seceon provides consistent security coverage. The platform monitors both north-south traffic (external connections) and east-west traffic (internal lateral movement), uncovering blind spots that perimeter-focused tools miss entirely.
For organizations embracing hybrid cloud strategies, Seceon eliminates the security gaps that emerge at the boundaries between environments. Security policies apply uniformly across all infrastructure, and threats are detected regardless of where they originate or where they attempt to move.
Converging IT and OT Security
The platform bridges industrial and enterprise systems, providing a single security fabric that extends protection to operational technology environments. Manufacturing facilities, utilities, healthcare systems, and other organizations with IoT and ICS devices gain visibility into previously unmonitored assets.
Seceon’s unified approach means that an attack originating in corporate IT systems can be detected as it attempts to pivot into operational networks—and automatically contained before impacting critical infrastructure.
Built-In Compliance and Reporting
Compliance shouldn’t require a separate team and months of preparation. Seceon includes comprehensive monitoring and reporting for major regulatory frameworks including NIST, ISO 27001, CMMC, HIPAA, PCI-DSS, and GDPR. Real-time dashboards and automated evidence collection transform compliance from a burden into a continuous process.
Real-World Impact: Measurable Results
Organizations that transition to Seceon’s unified platform experience dramatic improvements in both security effectiveness and operational efficiency:
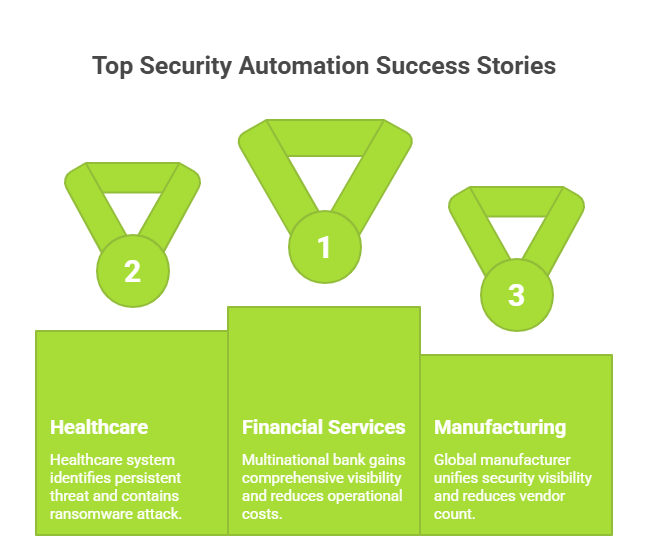
Financial Services: A multinational bank gained comprehensive visibility across hybrid environments while reducing operational costs. The automated detection and response capabilities enabled the security team to focus on strategic initiatives rather than chasing false positives.
Healthcare: A large healthcare system identified a previously undetected persistent threat in their environment and automatically contained a ransomware attack before it could impact critical care systems. HIPAA compliance reporting was streamlined, saving weeks of manual effort.
Manufacturing: A global manufacturer unified security visibility across IT and OT environments, detected an intellectual property theft attempt by an insider, and reduced their security vendor count from 14 to 5-dramatically simplifying management while improving protection.
Cost Savings: Organizations typically achieve 60-75% reduction in total security spending by consolidating multiple point solutions into the Seceon platform. For mid-sized enterprises, this translates to $5-9 million in annual savings.
Key Capabilities That Set Seceon Apart
Comprehensive Security Stack in One Platform
Seceon consolidates capabilities that traditionally require separate products:
- Next-generation SIEM for log management and threat correlation
- Extended Detection and Response (XDR) across endpoints, networks, and cloud
- Security Orchestration, Automation, and Response (SOAR) for automated remediation
- User and Entity Behavior Analytics (UEBA) for detecting insider threats
- Network Detection and Response (NDR) for east-west traffic visibility
- Cloud Security Posture Management (CSPM) for configuration monitoring
AI-Powered Automation
Speed matters in cybersecurity. Seceon’s automation capabilities reduce Mean Time to Respond (MTTR) from hours to minutes by automatically executing remediation actions based on threat severity and confidence levels. Custom playbooks enable security teams to automate responses to common scenarios while maintaining human oversight for complex situations.
Scalability for Enterprises and MSSPs
The platform’s multi-tier, multi-tenant architecture scales to ingest billions of events daily while maintaining millisecond analytics performance. For Managed Security Service Providers, this means a single analyst can monitor and protect hundreds of customer environments simultaneously—a game-changer for delivering enterprise-grade security at scale.
Zero Licensing Complexity
No per-gigabyte pricing. No events-per-second limitations. No painful negotiations over log volumes. Seceon’s transparent licensing model eliminates the cost-based blind spots that plague traditional SIEM deployments, where organizations deliberately limit log collection to manage expenses.
Implementation: Your Path to Unified Security
Transitioning to a unified security platform follows a structured approach that minimizes disruption while maximizing value:
Assessment and Planning: Begin with a comprehensive evaluation of your current security posture. Identify gaps, redundancies, and integration challenges. Define clear success metrics and a phased implementation roadmap.
Foundation Deployment: Deploy the Seceon platform and establish connectivity across your hybrid environment. The system begins ingesting data from existing sources while you maintain current security controls.
Advanced Analytics Integration: Enable AI-driven correlation and threat modeling. As the platform learns your environment’s normal behavior patterns, detection accuracy improves and false positives decrease.
Orchestrated Response and Optimization: Implement automated playbooks and continuous monitoring. Security teams shift from reactive alert chasing to proactive threat hunting and strategic security initiatives.
Seceon’s modular architecture allows organizations to start with foundational visibility and analytics, then expand to full automation and orchestration as security maturity grows.
The Future of Security is Unified
The cybersecurity landscape continues to evolve rapidly. Threat actors leverage automation, artificial intelligence, and multi-vector attacks that exploit the seams between disconnected security tools. Traditional approaches based on point solutions and manual correlation simply cannot keep pace.
Organizations that embrace unified security platforms gain:
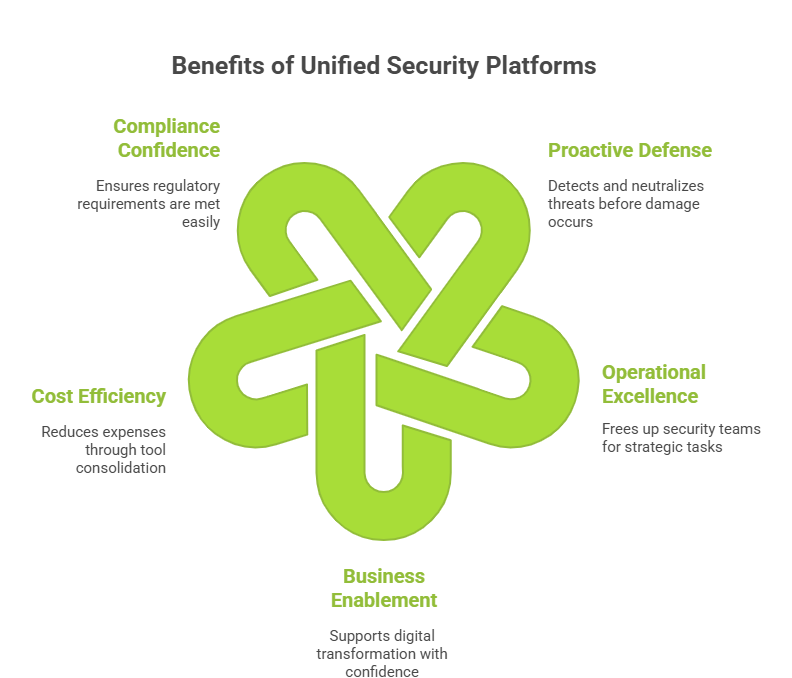
Proactive Defense: Threats are detected and neutralized before they can cause damage, not after the breach is discovered through forensics.
Operational Excellence: Security teams spend time on strategic initiatives rather than tool management, alert triage, and manual investigations.
Business Enablement: Digital transformation initiatives proceed with confidence, knowing that comprehensive security coverage extends to new cloud services, applications, and infrastructure.
Cost Efficiency: Consolidation eliminates redundant tools, reduces staffing overhead, and optimizes security spending.
Compliance Confidence: Continuous monitoring and automated reporting ensure regulatory requirements are met without heroic efforts during audit season.
Experience the Seceon Difference
Seceon’s unified platform represents more than incremental improvement-it’s a fundamental transformation in how organizations approach cybersecurity. By consolidating previously siloed capabilities into a single, AI-driven system, Seceon delivers the comprehensive protection modern enterprises require.
Security silos are a thing of the past. The future belongs to organizations that embrace unified platforms capable of seeing, understanding, and responding to threats across every corner of their digital ecosystem.
Ready to transform your security posture? Discover how Seceon’s unified platform can deliver comprehensive protection for your on-premises, cloud, and hybrid infrastructure while dramatically reducing operational complexity and cost.

The post Unified Security for On-Prem, Cloud, and Hybrid Infrastructure: The Seceon Advantage appeared first on Seceon Inc.
*** This is a Security Bloggers Network syndicated blog from Seceon Inc authored by Anand Prasad. Read the original post at: https://seceon.com/unified-security-for-on-prem-cloud-and-hybrid-infrastructure-the-seceon-advantage/
如有侵权请联系:admin#unsafe.sh