黑客利用 Fortinet 产品的两个严重漏洞(CVE-2025-59718 和 CVE-2025-59719),通过伪造 SAML 消息绕过 FortiCloud 单点登录认证,入侵管理员账户并窃取系统配置文件。建议禁用 FortiCloud 登录功能或升级至安全版本以防止攻击。 2025-12-16 16:0:23 Author: www.bleepingcomputer.com(查看原文) 阅读量:0 收藏

Hackers are exploiting critical-severity vulnerabilities affecting multiple Fortinet products to get unauthorized access to admin accounts and steal system configuration files.
The two vulnerabilities are tracked as CVE-2025-59718 and CVE-2025-59719, and Fortinet warned in an advisory on December 9 about the potential for exploitation.
CVE-2025-59718 is a FortiCloud SSO authentication bypass affecting FortiOS, FortiProxy, and FortiSwitchManager. It is caused by improper verification of cryptographic signatures in SAML messages, allowing an attacker to log in without valid authentication by submitting a maliciously crafted SAML assertion.
CVE-2025-59719 is a FortiCloud SSO authentication bypass affecting FortiWeb. It arises from a similar issue with the cryptographic signature validation of SAML messages, enabling unauthenticated administrative access via forged SSO.
Both issues are only exploitable if FortiCloud SSO is enabled, which is not the default setting. However, unless the feature is explicitly disabled, it is activated automatically when registering devices through the FortiCare user interface.
Targeting admin accounts
Researchers at cybersecurity company Arctic Wolf observed attacks exploiting the two security vulnerabilities starting on December 12. They note that the intrusions originated from several IP addresses linked to The Constant Company, BL Networks, and Kaopu Cloud HK.
Based on Arctic Wolf observations, the attackers targeted admin accounts with malicious single sign-on logins (SSO), as seen in the log below:
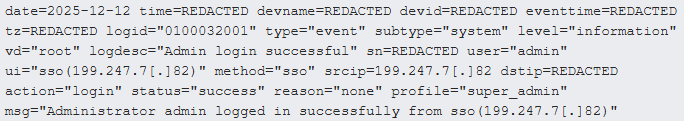
Source: Arctic Wolf
After obtaining admin-level access, the hackers accessed the web management interface and performed actions such as downloading the system’s configuration files.
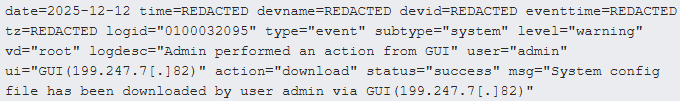
Source: Arctic Wolf
Configuration files can expose network layouts, internet-facing services, firewall policies, potentially vulnerable interfaces, routing tables, and also hashed passwords that may be cracked if weak.
The exfiltration of these files suggests that the activity is not from researchers mapping vulnerable endpoints, as exploitation is part of a malicious operation that may support future attacks.
Blocking the attacks
The two flaws impact multiple versions of Fortinet products except for FortiOS 6.4, FortiWeb 7.0, and FortiWeb 7.2.
To prevent attacks, Fortinet recommends that admins still running a vulnerable version temporarily disable the FortiCloud login feature until an upgrade to a safer version is possible.
This can be done from System → Settings → “Allow administrative login using FortiCloud SSO” = Off.
System administrators are recommended to move to one of the following versions that address both vulnerabilities:
- FortiOS 7.6.4+, 7.4.9+, 7.2.12+, and 7.0.18+
- FortiProxy 7.6.4+, 7.4.11+, 7.2.15+, 7.0.22+
- FortiSwitchManager 7.2.7+, 7.0.6+
- FortiWeb 8.0.1+, 7.6.5+, 7.4.10+
If any signs of compromise are discovered, it is recommended to rotate firewall credentials as soon as possible. Arctic Wolf also recommends limiting firewall/VPN management access to trusted internal networks only.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.
如有侵权请联系:admin#unsafe.sh
