If you’ve ever looked at a SOC queue and thought, “Where do we even start?” you’re not alone.
Most teams face more alerts than they can realistically investigate, tools that don’t always connect, and investigations that take longer than they should.
In a recent webinar, we shared a simple framework for speeding up detection and response without overloading teams. You can watch the full recording here: SOC Leader’s Playbook
SOC teams that applied this approach have already seen measurable results:
- 21 minutes less MTTR per incident
- 15-second median MTTD
- 3× improvement in team throughput
For now, let’s look at how you can apply the same ideas to help your SOC respond faster in real environments.
The Cost of a Slow SOC
When detection and response take too long, the impact shows up fast and in very practical ways.

- Incidents cost more: According to IBM’s Cost of a Data Breach Report 2025, the average breach now costs $4.4 million, and that number grows the longer attackers stay active.
- Downtime lasts longer: Delayed response means systems stay compromised, business processes slow down, and recovery becomes harder.
- Teams waste time on noise: Analysts spend hours chasing alerts that turn out to be harmless, often repeating the same checks across different tools.
- Real threats get missed: Fatigue and overload make it easier for serious incidents to slip through unnoticed.
- People burn out: Constant pressure and reactive work drain focus and motivation, especially in Tier 1 teams.
For SOC leaders, this creates a familiar loop: more alerts, slower response, higher risk, and exhausted teams. Breaking that loop starts with reducing time at every stage, from the first alert to final containment.

Step 1: Prioritize Incidents and Reduce False Positives
Speed starts with focus. If your SOC treats every alert the same, response will always be slow.
Most teams receive far more alerts than they can realistically investigate. Many are low-risk, duplicated, or lack context. Analysts lose time figuring out what an alert actually means instead of responding to real threats.
The root issue is usually threat intelligence.
Indicators pulled from public reports often arrive too late, after attackers have already changed infrastructure. Other feeds may be fast but offer no explanation beyond “malicious,” forcing analysts to investigate manually. Automation suffers, false positives rise, and the SOC stays reactive.

What works
Effective prioritization depends on threat intelligence that is:
- Real-time, not report-based
- Context-rich, showing how an indicator is used
- Integrated, flowing directly into SIEM, SOAR, and EDR
When alerts arrive already enriched with reputation, behavior, and risk level, teams can automate routine triage and focus on high-impact incidents.
How this looks with ANY.RUN
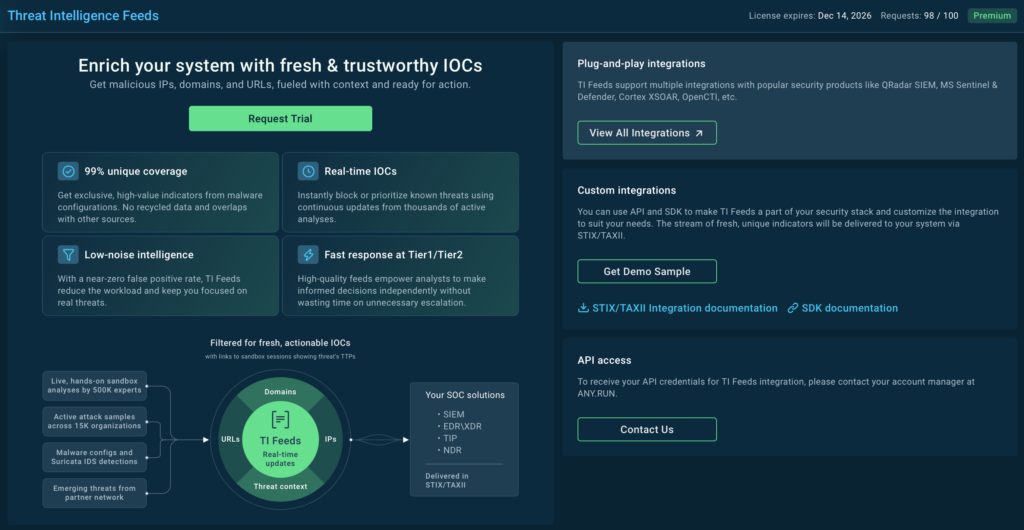
ANY.RUN delivers this through its Threat Intelligence Feeds.
TI Feeds provide real-time IOCs sourced from live attacks analyzed in ANY.RUN’s Interactive Sandbox by 15,000 organizations and 500,000 analysts. As a result, 99% of network IOCs are unique and come with links to full sandbox reports for immediate context.
For SOC teams, this means earlier detection of new threats, fewer false positives, and up to a 20% reduction in Tier 1 workload.
Step 2: Speed Up Threat Investigations
Once an alert is prioritized, the next bottleneck is investigation speed.
Many SOCs still rely on static analysis. It’s fast, but it doesn’t show what actually happens when a file or link runs. Modern malware hides behind obfuscation, delayed execution, or multi-stage delivery, leaving analysts with partial answers and slow decisions.
To respond quickly, teams need to see real behavior, not just a verdict.

What actually speeds investigations up
Effective investigations depend on dynamic analysis that:
- Integrate with your existing tools to automate investigations and avoid manual handoffs
- Expose real threat behavior quickly, even in multi-stage or silent attacks
- Deliver clear, actionable reports with verdicts, IOCs, and TTPs
- Defeat evasion techniques, forcing malware to reveal itself
How teams do this with ANY.RUN
ANY.RUN helps SOC teams move from alert to answer in under 60 seconds.
By detonating files and URLs in real time, the Interactive Sandbox exposes the full attack chain and automatically generates clear reports with verdicts, IOCs, and attacker techniques. This allows teams to confirm threats quickly and move straight to containment, cutting up to 21 minutes from MTTR per incident.
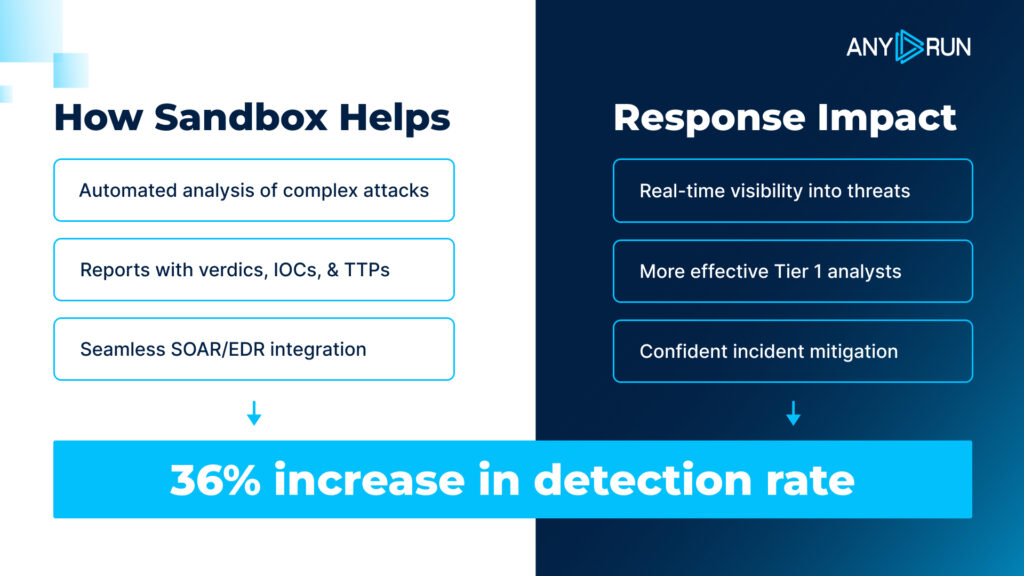
Because the results are easy to interpret, even junior analysts can handle more alerts independently. Many teams report up to a 30% reduction in Tier 1–to–Tier 2 escalations, easing pressure on senior staff and speeding up response overall.
For high-volume workflows, the sandbox also runs in Automated Interactivity mode. Files and URLs can be sent automatically via API, SDK, or native integrations with SOAR, EDR, and other security tools. The sandbox detonates the entire attack chain on its own and returns a conclusive verdict with full context in seconds.
Check a real-world case inside sandbox
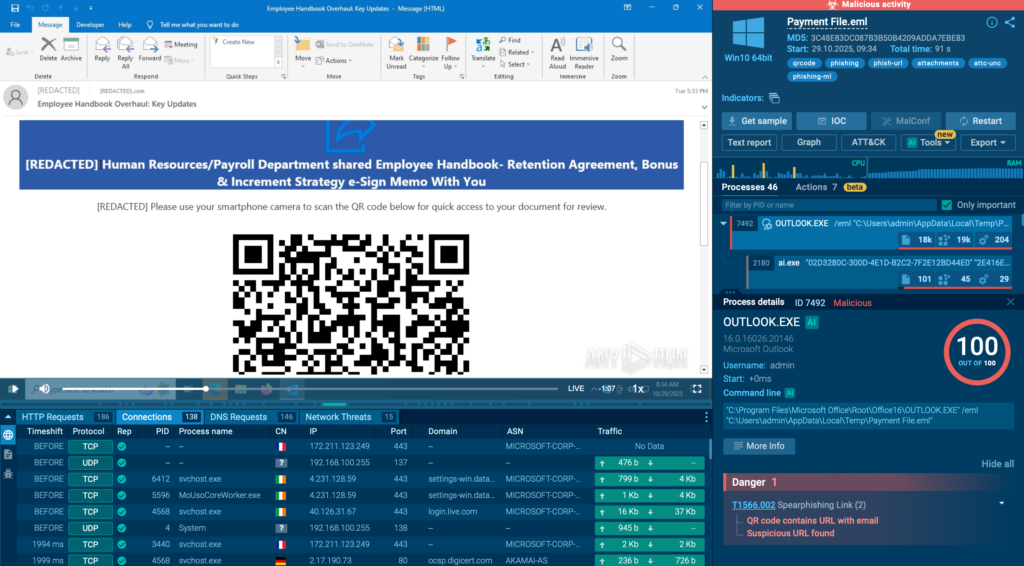
In this analysis, a QR code hidden in a phishing email leads to a CAPTCHA-protected page and then to a fake Microsoft 365 login designed to steal credentials. The sandbox detonates the full chain, reveals the phishing infrastructure, and confirms credential theft behavior in seconds.
Step 3: Verify Alerts Fast
Not every alert points to a file you can detonate.
Often, SOC teams see alerts tied to a suspicious IP, domain, URL, or process. In those cases, the key question is simple: Is this a real threat, or just noise?
The faster you answer that, the faster you can move on.
Where verification slows teams down
Most alerts are enriched using free reputation services. These usually provide only a label like “malicious” with no explanation.
There’s no context about:
- how the indicator was used,
- what malware or campaign it’s linked to,
- or what the attacker is actually doing.
So, analysts start from zero. They search blogs, PDFs, forums, and tools, copy-paste the same indicator repeatedly, and hope something useful turns up. It’s slow, distracting, and often outdated. Even when teams cross-check multiple sources, the information can be incomplete or contradictory.
The result is delayed decisions, unnecessary escalations, and analyst fatigue.

What helps analysts verify alerts faster
Analysts move faster when they have access to a single, reliable source of fresh threat intelligence that gives instant context for any indicator they see.
The most effective solutions don’t rely on second hand reports. They pull data from their own live sources; real malware executions, active honeypots, and real victim environments. That means the intelligence is current, detailed, and available the moment an alert appears.
With this level of context, analysts can make confident decisions in seconds instead of spending time searching, cross-checking, and guessing.
How teams do this with ANY.RUN
ANY.RUN enables fast alert verification through its Threat Intelligence Lookup.
TI Lookup gives analysts instant access to live attack data for IPs, domains, URLs, file hashes, and behavioral indicators. Each lookup returns real-world context, including how the indicator is used, what malware it’s linked to, and where it was observed; all based on active threat analysis, not old reports.
As the intelligence comes from real malware executions shared by 15,000 organizations and 500,000 analysts, analysts can verify alerts in seconds instead of starting from zero.

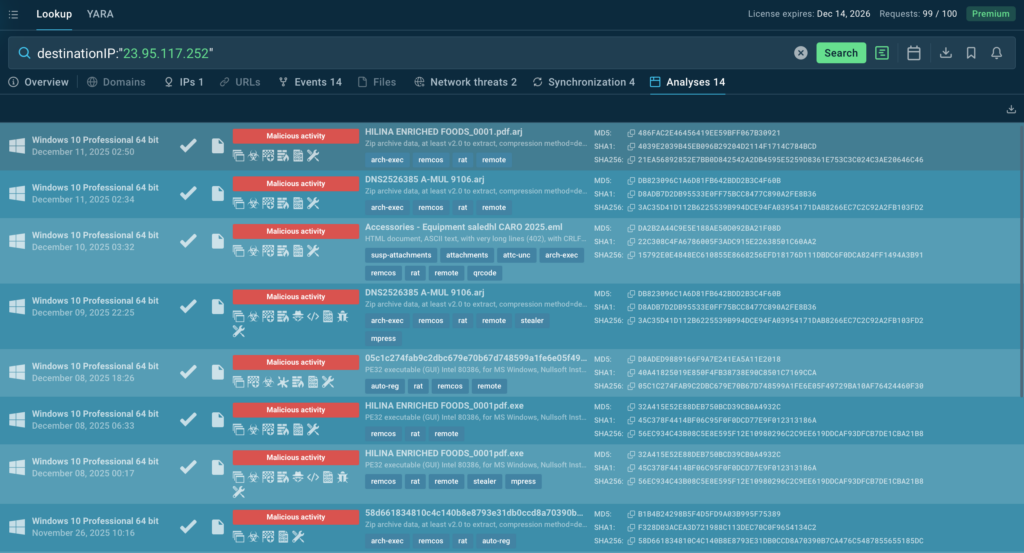
To see how this works in practice, imagine this: A SOC receives an alert about a connection to an unfamiliar IP address. A quick lookup shows it’s actively used in a Remcos malware campaign, with links to sandbox sessions where the same infrastructure was observed. With this context, the analyst can block the connection and close the alert confidently within minutes.
TI Lookup query: destinationIP:”23.95.117.252″
For even faster workflows, TI Lookup integrates directly with SIEM, SOAR, TIP, and XDR platforms. Alerts can be enriched automatically as they arrive, so reputation, behavior, and threat context are available immediately, reducing manual checks, unnecessary escalations, and investigation time.
Make Fast Response the Standard
In most SOCs, the problem isn’t speed. It’s the delay between seeing an alert and knowing what to do next.
When alerts arrive without context, investigations stall. When verification depends on manual research, response drags on. Fixing these gaps changes how the SOC operates:
- incidents are prioritized earlier,
- investigations reach clear answers faster,
- alerts are confirmed before they turn into distractions.

Teams that apply this approach consistently reduce MTTR by 21 minutes, detect threats in a median of 15 seconds, and achieve a 3× increase in team efficiency, without adding pressure to the team.
About ANY.RUN
ANY.RUN provides interactive malware analysis and threat intelligence solutions used by 15,000 SOC teams to investigate threats and verify alerts. They enable analysts to observe real attacker behavior in controlled environments and access context from live attacks. The services support both hands-on investigation and automated workflows and integrates with SIEM, SOAR, and EDR tools commonly used in security operations.
