
嗯,用户让我总结一下这篇文章的内容,控制在100字以内,而且不需要用“文章内容总结”或者“这篇文章”这样的开头。好的,我先仔细读一下文章。 文章主要讲的是现代XDR工具虽然敏感,能够检测到很多可疑行为,但同时也带来了大量的警报,这对MSSP来说是个负担。传统的解决办法是调整传感器或抑制检测规则,但这会导致很多警报没有被调查。Morpheus的解决方案是引入一个结合AI的SOC架构,能够自动处理所有警报,并在短时间内完成分类。这样不仅减少了人工负担,还提高了效率和一致性。 接下来我要把这些要点浓缩到100字以内。重点包括:XDR的敏感性导致大量警报、MSSP的传统应对方式及其问题、Morpheus的解决方案及其优势。 可能的结构是:现代XDR工具敏感但产生大量警报;MSSP传统应对方式导致问题;Morpheus通过AI SOC架构自动处理所有警报,在短时间内分类,减少人工负担,提高效率和一致性。 现在试着组织语言: 现代XDR工具敏感但产生大量警报;MSSP传统应对方式导致问题;Morpheus通过AI SOC架构自动处理所有警报,在短时间内分类,减少人工负担,提高效率和一致性。 这样大概控制在100字左右了。 </think> 现代XDR工具敏感但产生大量警报;MSSP传统应对方式导致问题;Morpheus通过AI SOC架构自动处理所有警报,在短时间内分类,减少人工负担,提高效率和一致性。 2025-12-12 23:45:10 Author: securityboulevard.com(查看原文) 阅读量:10 收藏
Whether you run CrowdStrike, SentinelOne, Microsoft Defender, or provide a Managed XDR (Extended Detection and Response) across a mixed vendor stack, the operational challenge is the same. Modern XDRs are intentionally sensitive. They are built to flag everything that might be suspicious, and indicative of malicious behavior.
For Managed Security Service Providers (MSSPs), that sensitivity is both the value and the burden. They offer superior detection, but they generate a firehose of alerts that break traditional staffing models. Scaling your SOC by hiring more analysts decimates margins and guarantees burnout.
To cope, most SOCs make uncomfortable compromises. Sensors are tuned down. Detection rules are suppressed. Backlogs grow. They accept that ~40% of alerts will never be investigated. The industry rationalizes this exposure as a tradeoff it has no choice but to make.
Morpheus changes the economics of managed detection by introducing a blended AI SOC architecture. designed to autonomously investigate every alert at machine speed, while keeping humans in control of high impact decisions. It investigates 100% of alerts, triaging 95% of them in under 2 minutes, restoring full visibility without ballooning headcount.
Here is how Morpheus turns XDR volume from an operational liability into a competitive advantage.
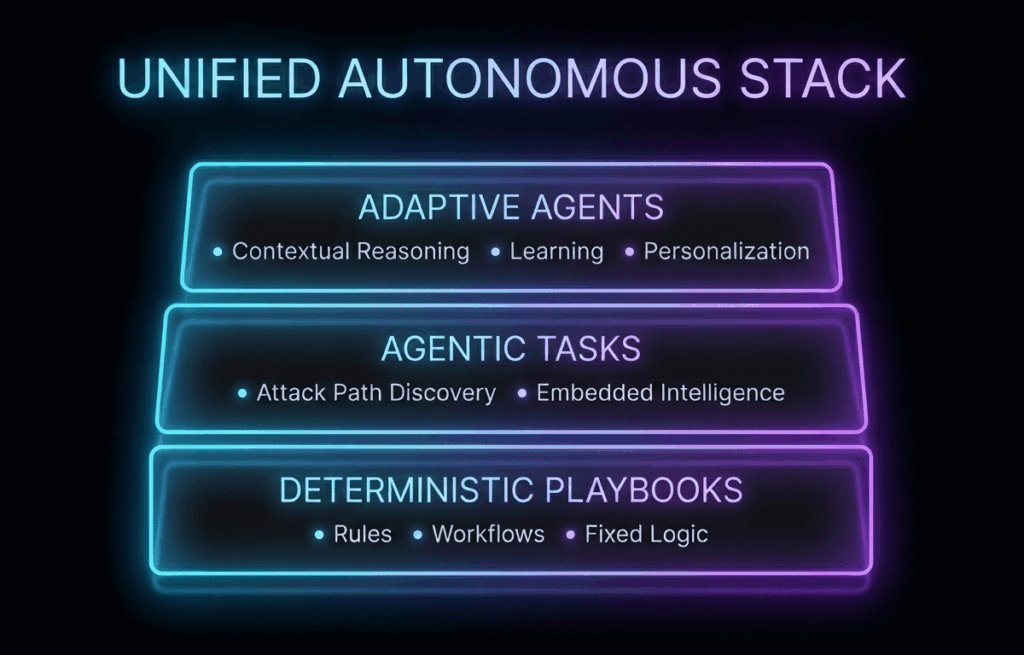
The Blended AI SOC: Architecture Built for MSSP Scale
By adopting a blended AI SOC model, Morpheus acts as an always-on investigation layer that sits on top of your XDR stack.
Unified Data Normalization
Morpheus pulls alerts from every tenant and every tool (S1, CS, Defender, Taegis). It transforms this chaotic, multi-source data into a consistent, enriched model. Your team works from one unified schema, regardless of the underlying XDR technology.
Built for Peak Load
MSSP environments are defined by spikes: a new exploit drops, or a customer is targeted, or when detections are updated across tenants. Many automation platforms respond by aggressively queuing work, delaying outcomes precisely when speed matters most. Morpheus is designed for peak load scenarios. It executes investigations in parallel, maintaining performance during extreme volume surges and ensuring operational continuity during your busiest hours.
Autonomous Investigations
This is where you break the linear scaling trap. Morpheus automatically applies investigation playbooks to incoming alerts based on predefined policies and severity.
Morpheus queries XDR tools for deep context, such as process tree analysis or current device containment status, and correlates that data with identity and network context to build a complete investigative picture. A typical investigation may include lineage analysis, user and host activity review, and reputation or prevalence checks, all executed consistently and at machine speed.
For example, a suspicious PowerShell alert can trigger immediate process tree analysis, recent user and host activity review, and indicator reputation lookups via connected threat intelligence sources. If the behavior aligns with approved administrative tooling on a low-risk asset, Morpheus can recommend closure, or close automatically when your policy allows. If indicators suggest credential abuse, persistence, or other high-risk activity, it escalates the case and attaches the collected evidence and investigation steps.
When an alert is determined to be benign per policy, Morpheus can close it record a detailed audit trail of actions taken and the rationale. This ensures transparency, supports compliance requirements, and allows analysts to focus their time on investigations that truly require human judgment.
Stop the Churn. Start the Scale
The impact of this architecture is measurable. One of D3’s customers, a master MSSP, leveraged D3’s automation to fundamentally alter their operational metrics. Facing massive alert volumes from their diverse customer base, they implemented automated triage to filter noise before it reached human analysts. The results were definitive:
“We minimized alert noise by a staggering 99% (from 145,000 in a two-week period to just 1,000).”
This reduction allowed them to triple their client handling capacity without adding headcount.
By automating the investigation of XDR alerts, MSSPs shift their value proposition from “monitoring” to “outcome delivery”.
- Slash MTTR: The majority of alerts are investigated and resolved in minutes rather than hours.
- Enforce Consistency: Every alert, from every tenant, is investigated using the same rigorous logic, ensuring SLA compliance.
- Protected Margins: High value analysts are no longer consumed by repetitive triage work, allowing teams to scale revenue without scaling cost.
Your XDR stack provides the visibility. Morpheus provides the scale, consistency, and economics required to grow. Ready to see Morpheus in action? Get a demo.
The post The Autonomous MSSP: How to Turn XDR Volume into a Competitive Advantage appeared first on D3 Security.
*** This is a Security Bloggers Network syndicated blog from D3 Security authored by Shriram Sharma. Read the original post at: https://d3security.com/blog/morpheus-autonomous-mssp-for-xdr-noise/
如有侵权请联系:admin#unsafe.sh