
好的,我现在需要帮用户总结一篇文章的内容,控制在100个字以内。首先,我得仔细阅读文章,理解其主要内容。 文章主要讲的是CISA(美国网络安全和基础设施安全局)下令美国联邦机构修补一个关键的GeoServer漏洞。这个漏洞是XML外部实体注入攻击的目标,已经被积极利用。漏洞编号是CVE-2025-58360,影响GeoServer 2.26.1及更早版本。攻击者可以利用这个漏洞进行拒绝服务攻击、访问机密数据或执行服务器端请求伪造。 此外,文章提到有数千个暴露在网上的GeoServer实例,CISA已经将此漏洞加入其已知被利用的漏洞目录,并要求联邦机构在2026年1月1日前修补。虽然该指令仅适用于联邦机构,但CISA建议所有网络防御者尽快修补此漏洞。 接下来,我需要将这些信息浓缩到100字以内。重点包括:CISA下令修补GeoServer漏洞,该漏洞被积极利用,影响版本范围,攻击后果以及修补时间要求。 最后,确保语言简洁明了,不使用复杂的术语,并且直接描述内容。 </think> CISA要求美国联邦机构修复 GeoServer 的 XML 外部实体注入漏洞(CVE-2025-58360),该漏洞已被用于攻击。此漏洞影响 GeoServer 2.26.1 及以下版本,允许攻击者获取文件或发起拒绝服务攻击。CISA已将其列为已知被利用的漏洞,并要求相关机构在 2026 年 1 月 1 日前完成修复。 2025-12-12 10:0:23 Author: www.bleepingcomputer.com(查看原文) 阅读量:10 收藏

CISA has ordered U.S. federal agencies to patch a critical GeoServer vulnerability now actively exploited in XML External Entity (XXE) injection attacks.
In such attacks, an XML input containing a reference to an external entity is processed by a weakly configured XML parser, allowing threat actors to launch denial-of-service attacks, access confidential data, or perform Server-Side Request Forgery (SSRF) to interact with internal systems.
The security flaw (tracked as CVE-2025-58360) flagged by CISA on Thursday is an unauthenticated XML External Entity (XXE) vulnerability in GeoServer 2.26.1 and prior versions (an open-source server for sharing geospatial data over the Internet) that can be exploited to retrieve arbitrary files from vulnerable servers.
"An XML External Entity (XXE) vulnerability was identified affecting GeoServer 2.26.1 and prior versions. The application accepts XML input through a specific endpoint /geoserver/wms operation GetMap," a GeoServer advisory explains.
"However, this input is not sufficiently sanitized or restricted, allowing an attacker to define external entities within the XML request."
The Shadowserver Internet watchdog group now tracks 2,451 IP addresses with GeoServer fingerprints, while Shodan reports over 14,000 instances exposed online.
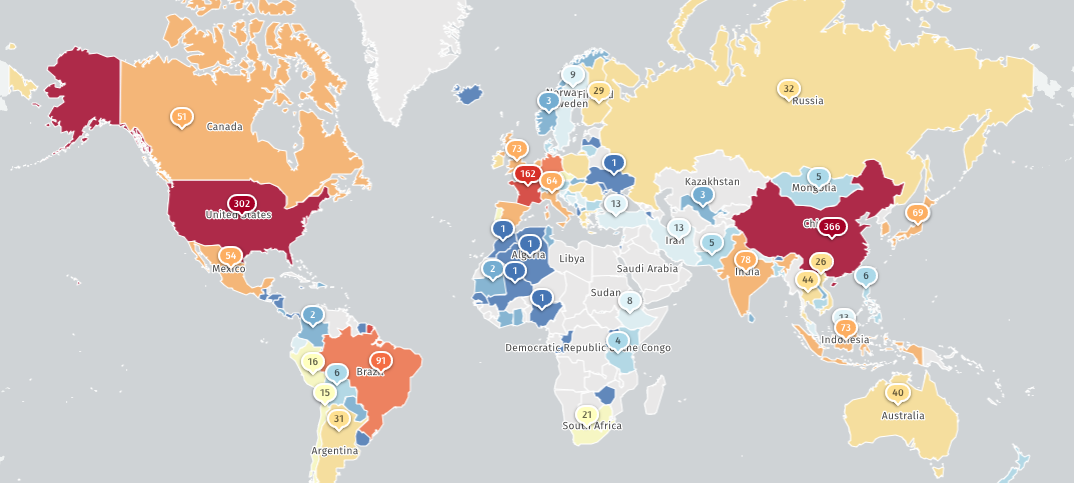
CISA has now added CVE-2025-58360 to its Known Exploited Vulnerabilities (KEV) Catalog, warning that the flaw is being actively exploited in attacks and ordering Federal Civilian Executive Branch (FCEB) agencies to patch servers by January 1st, 2026, as mandated by the Binding Operational Directive (BOD) 22-01 issued in November 2021.
FCEB agencies are non-military agencies within the U.S. executive branch, such as the Department of Energy, the Department of the Treasury, the Department of Homeland Security, and the Department of Health and Human Services.
Although BOD 22-01 only applies to federal agencies, the U.S. cybersecurity agency urged network defenders to prioritize patching this vulnerability as soon as possible.
"These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise," CISA said. "Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable."
Last year, CISA also added OSGeo GeoServer JAI-EXT code injection (CVE-2022-24816) and GeoTools eval injection (CVE-2024-36401) vulnerabilities to its list of actively exploited security flaws.
As the cybersecurity agency revealed in September, the latter was exploited to breach an unnamed U.S. government agency in 2024 after compromising an unpatched GeoServer instance.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.
如有侵权请联系:admin#unsafe.sh
