Welcome to this week’s edition of the Threat Source newsletter.
“It’s a dangerous business, going out your door. You step onto the road, and if you don’t keep your feet, there’s no knowing where you might be swept off to.” — Bilbo Baggins
It’s almost the end of the year, which feels like the perfect time to start an epic quest.
So, Middle-earth. I’m walking across it. Not with the intention of destroying the One Ring, but to increase my daily step count in the nerdiest way possible.
As I suspect is the origin story for most quests these days, my journey began by downloading an app.

It’s called “The Conqueror.” There are many different distances you can choose from, but I chose Middle-earth because I’m that person who watched all the behind-the-scenes footage from Peter Jackson’s Lord of the Rings extended edition box set and physically shed tears because I wasn’t there.
Heeding Bilbo’s warnings about roads, I’m using a treadmill. After receiving my official race bib (#199574), I hopped on and muttered under my breath, “So it begins.”
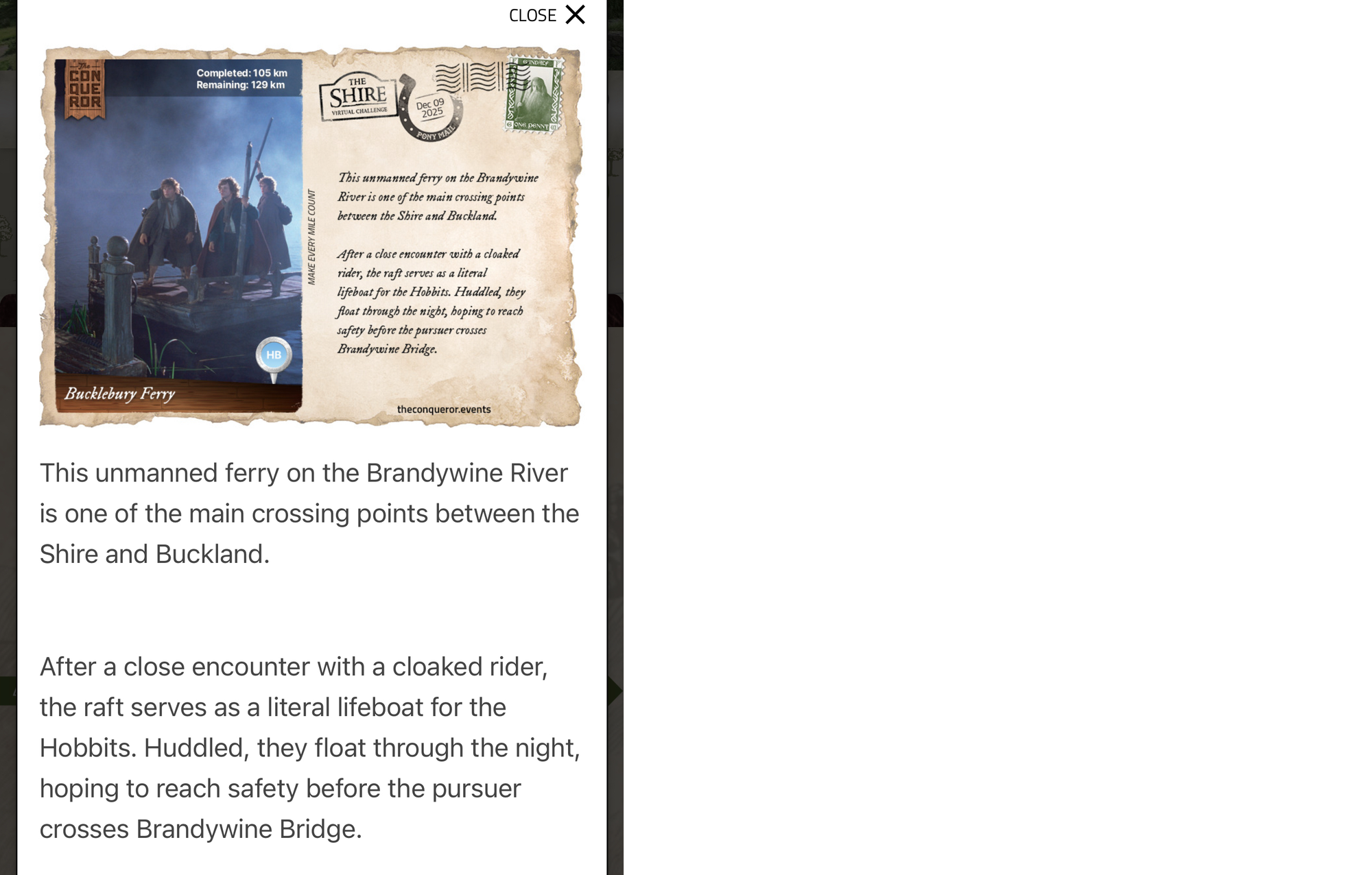
So far, I’ve passed Bag End, South Farthing, Woody End, Maggot’s Farm, and I’m currently doing a stopover at Buckleberry Ferry. That’s 130km (55% of the Shire) done. Only 120km until Bree, where I can rest up with a pint at The Prancing Pony. And a mere 2,787km to go until I get to Mount Doom. If only Frodo hadn’t taken so many detours…
I’ve been rewarded at each milestone with postcards full of extremely nerdy facts about the landscape. And because of The Conqueror’s partnership with an ocean clean-up charity, I’ve also “saved” 20 plastic bottles from entering the sea, which feels very cool to have accomplished while never leaving the house.

It’s a strange, delightful journey: half fitness plan, half fantasy pilgrimage. And it got me thinking about the value of knowing your destination.
Oftentimes when I’m speaking to defenders, one of their main challenges is “I’m struggling to do all the things, all the time.” When everything gets a bit overwhelming, and threats either shift unpredictably or circle back to tactics we thought we’d left behind, it’s easy to lose your sense of direction and say, “What are we doing this for again?”
That’s what I’ve come to like about this quest across Middle-earth: there’s a destination, and there are milestones. Mount Doom is a f*****g long way from Buckleberry Ferry. But I like just knowing the next marker even if I can’t yet see the (Bag)end.
As you’re making plans for next year, it might be worth using that idea: Where are you heading? What are the things you’re doing right now are actually helping you get there? Which detours/madness will lead you into Fangorn Forest?
If in doubt, follow your nose.
The one big thing
While tracking ransomware activities, Cisco Talos uncovered new tactics, techniques, and procedures (TTPs) linked to a financially motivated threat actor targeting victims with DeadLock ransomware. The DeadLock ransomware targets Windows machines with a custom stream cipher encryption algorithm that uses time-based cryptographic keys to encrypt files.
Why do I care?
There’s a few things that the threat actor does as part of this campaign to make recovery for victims more complicated. First, they use the Bring Your Own Vulnerable Driver (BYOVD) technique with a previously unknown loader to exploit the Baidu Antivirus driver vulnerability (CVE-2024-51324), enabling the termination of endpoint detection and response (EDR) processes. Also, the custom encryption method allows DeadLock ransomware to effectively encrypt different file types in enterprise environments while preventing system corruption through selective targeting and anti-forensics techniques.
So now what?
The Talos blog has a full breakdown of the attack, including the new TTPs, attempts at lateral movement, the ways the actor attempts to impair defenses, and the encryption process. Snort SIDs for the threats are: 65576, 65575 and 301358. ClamAV detections are also available for this threat:
- Win.Tool.EDRKiller-10058432-0
- Win.Tool.VulnBaiduDriver-10058431-1
- Ps.Tool.DeleteShadowCopies-10058429-0
- Win.Ransomware.Deadlock-10058428-0
Top security headlines of the week
Chinese hackers are using “stealthy and resilient” Brickstorm malware to target VMware servers
The Cybersecurity and Infrastructure Security Agency (CISA) is warning that China-sponsored threat actors are using Brickstorm malware to achieve long-term persistence in critical infrastructure networks. (ITPro)
Critical Apache Tika vulnerability leads to XXE injection
A critical-severity vulnerability in the Apache Tika open source analysis toolkit could allow attackers to perform XML External Entity (XXE) injection attacks. (Security Week)
Zero-click agentic browser attack can delete entire Google Drive using crafted emails
A new agentic browser attack targeting Perplexity's Comet browser that's capable of turning a seemingly innocuous email into a destructive action that wipes a user's entire Google Drive contents. (The Hacker News)
Can’t get enough Talos?
Spy vs. spy: How GenAI is powering defenders and attackers
Nick Biasini provides an update on how Talos is seeing threat actors currently use genAI, and how defenders can use it as a force multiplier.
Microsoft Patch Tuesday for December 2025
The Patch Tuesday for December of 2025 includes 57 vulnerabilities, including two that Microsoft marked as “critical.” The remaining vulnerabilities listed are classified as “important.”
Most prevalent malware files from Talos telemetry over the past week
SHA256: d933ec4aaf7cfe2f459d64ea4af346e69177e150df1cd23aad1904f5fd41f44a
MD5: 1f7e01a3355b52cbc92c908a61abf643
Talos Rep: https://talosintelligence.com/talos_file_reputation?s=d933ec4aaf7cfe2f459d64ea4af346e69177e150df1cd23aad1904f5fd41f44a
Example Filename: cleanup.bat
Detection Name: W32.D933EC4AAF-90.SBX.TG
SHA256: 9f1f11a708d393e0a4109ae189bc64f1f3e312653dcf317a2bd406f18ffcc507
MD5: 2915b3f8b703eb744fc54c81f4a9c67f
Talos Rep: https://talosintelligence.com/talos_file_reputation?s=9f1f11a708d393e0a4109ae189bc64f1f3e312653dcf317a2bd406f18ffcc507
Example Filename: 9f1f11a708d393e0a4109ae189bc64f1f3e312653dcf317a2bd406f18ffcc507.exe
Detection Name: Win.Worm.Coinminer::1201
SHA256: 1ec34305e593c27bb95d538d45b6a17433e71fa1c1877ce78bf2dbda6839f218
MD5: a1f4931992bf05e9bff4b173c15cab15
Talos Rep: https://talosintelligence.com/talos_file_reputation?s=1ec34305e593c27bb95d538d45b6a17433e71fa1c1877ce78bf2dbda6839f218
Example Filename: a1f4931992bf05e9bff4b173c15cab15.exe
Detection Name: Auto.1EC343.272247.in02
SHA256: 96fa6a7714670823c83099ea01d24d6d3ae8fef027f01a4ddac14f123b1c9974
MD5: aac3165ece2959f39ff98334618d10d9
Talos Rep: https://talosintelligence.com/talos_file_reputation?s=96fa6a7714670823c83099ea01d24d6d3ae8fef027f01a4ddac14f123b1c9974
Example Filename: 96fa6a7714670823c83099ea01d24d6d3ae8fef027f01a4ddac14f123b1c9974.exe
Detection Name: W32.Injector:Gen.21ie.1201
SHA256: 90b1456cdbe6bc2779ea0b4736ed9a998a71ae37390331b6ba87e389a49d3d59
MD5: c2efb2dcacba6d3ccc175b6ce1b7ed0a
Talos Rep: https://talosintelligence.com/talos_file_reputation?s=90b1456cdbe6bc2779ea0b4736ed9a998a71ae37390331b6ba87e389a49d3d59
Example Filename: ck8yh2og.dll
Detection Name: Auto.90B145.282358.in02